A vulnerability is a weakness or flaw in a system that can be exploited by attackers, while a threat represents the potential danger or harm that exploits may cause. Understanding the distinction between vulnerability and threat is critical for implementing effective security measures and mitigating risks. Prioritizing the identification of vulnerabilities helps organizations anticipate and defend against potential threats before they materialize.
Table of Comparison
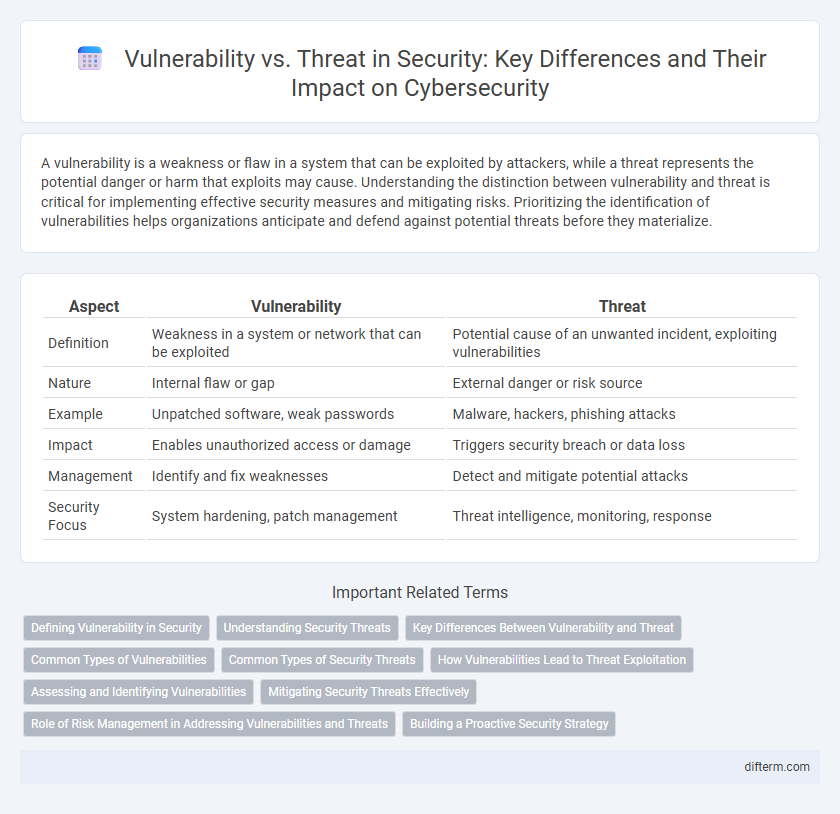
| Aspect | Vulnerability | Threat |
|---|---|---|
| Definition | Weakness in a system or network that can be exploited | Potential cause of an unwanted incident, exploiting vulnerabilities |
| Nature | Internal flaw or gap | External danger or risk source |
| Example | Unpatched software, weak passwords | Malware, hackers, phishing attacks |
| Impact | Enables unauthorized access or damage | Triggers security breach or data loss |
| Management | Identify and fix weaknesses | Detect and mitigate potential attacks |
| Security Focus | System hardening, patch management | Threat intelligence, monitoring, response |
Defining Vulnerability in Security
Vulnerability in security refers to a weakness or flaw in a system, network, or application that can be exploited by attackers to gain unauthorized access or cause damage. These weaknesses may result from software bugs, misconfigurations, or inadequate security controls, making assets susceptible to compromise. Identifying and mitigating vulnerabilities is critical for reducing risk and protecting sensitive data from potential security breaches.
Understanding Security Threats
A vulnerability is a weakness in a system, network, or application that can be exploited by a threat to cause harm or unauthorized access. A threat represents any potential danger that can exploit vulnerabilities to compromise security, such as malware, phishing attacks, or insider threats. Understanding security threats involves identifying and assessing these threats to prioritize defensive measures and strengthen organizational resilience against cyber attacks.
Key Differences Between Vulnerability and Threat
Vulnerability refers to a weakness or flaw in a system, software, or network that can be exploited by attackers to gain unauthorized access or cause damage. Threat is any potential danger or malicious actor that exploits vulnerabilities to compromise security, such as hackers, malware, or phishing attacks. Understanding that vulnerability is a system's susceptibility while threat is the external source aiming to exploit that weakness is crucial for effective risk management and security strategy development.
Common Types of Vulnerabilities
Common types of vulnerabilities include software bugs, misconfigurations, weak authentication, and unpatched systems that expose organizations to security risks. Vulnerabilities serve as entry points for threats such as malware, phishing attacks, and denial-of-service exploits. Understanding these weaknesses is critical for implementing effective patch management, access controls, and continuous monitoring to mitigate potential breaches.
Common Types of Security Threats
Common types of security threats include malware, phishing attacks, ransomware, insider threats, and denial-of-service (DoS) attacks. Each threat exploits specific vulnerabilities in systems, networks, or human behavior to gain unauthorized access or cause damage. Understanding these threats is crucial for implementing effective cybersecurity measures and vulnerability management strategies.
How Vulnerabilities Lead to Threat Exploitation
Vulnerabilities are weaknesses in software, hardware, or network systems that can be exploited by attackers, allowing unauthorized access or control. Threat actors leverage these vulnerabilities to breach security defenses, execute malicious code, or steal sensitive data, turning potential risks into active threats. Effective vulnerability management reduces the attack surface and minimizes the chances of threat exploitation by identifying and patching security gaps promptly.
Assessing and Identifying Vulnerabilities
Assessing vulnerabilities involves systematically scanning systems and applications to identify security weaknesses that could be exploited by attackers. Vulnerability identification methods include automated tools, penetration testing, and code reviews to uncover flaws such as outdated software, misconfigurations, and missing patches. Understanding vulnerabilities is crucial for prioritizing remediation efforts and strengthening an organization's overall security posture against potential threats.
Mitigating Security Threats Effectively
Mitigating security threats effectively requires distinguishing between vulnerabilities and threats, as vulnerabilities represent weaknesses in systems while threats are potential exploits targeting those weaknesses. Implementing proactive vulnerability assessments, continuous monitoring, and patch management significantly reduces exposure to threats such as malware, phishing, and ransomware. Employing multi-layered security controls including firewalls, intrusion detection systems, and user training enhances an organization's ability to prevent, detect, and respond to evolving cyber threats.
Role of Risk Management in Addressing Vulnerabilities and Threats
Risk management plays a critical role in addressing vulnerabilities and threats by systematically identifying, assessing, and prioritizing potential security weaknesses and attack vectors. It implements controls and mitigation strategies to reduce the likelihood and impact of exploitation, ensuring organizational resilience against cyberattacks. Continuous monitoring and assessment enable adaptive responses to evolving vulnerabilities and emerging threat landscapes, maintaining robust security posture.
Building a Proactive Security Strategy
A proactive security strategy prioritizes identifying and mitigating vulnerabilities before threats exploit them, reducing potential attack surfaces and minimizing risks. Understanding the distinction between vulnerabilities--system weaknesses--and threats--potential causes of harm--enables targeted defenses such as regular patch management and continuous monitoring. Implementing automated vulnerability scanning alongside threat intelligence integration strengthens an organization's resilience against evolving cyber threats.
Vulnerability vs Threat Infographic
 difterm.com
difterm.com