Security policy defines the overarching rules and standards that govern an organization's approach to protecting its assets, setting the framework for security objectives and roles. Security procedure provides detailed, step-by-step instructions to implement the policies effectively, ensuring consistent and practical application. Clear distinction between security policy and security procedure is crucial for maintaining robust and enforceable protection in any security environment.
Table of Comparison
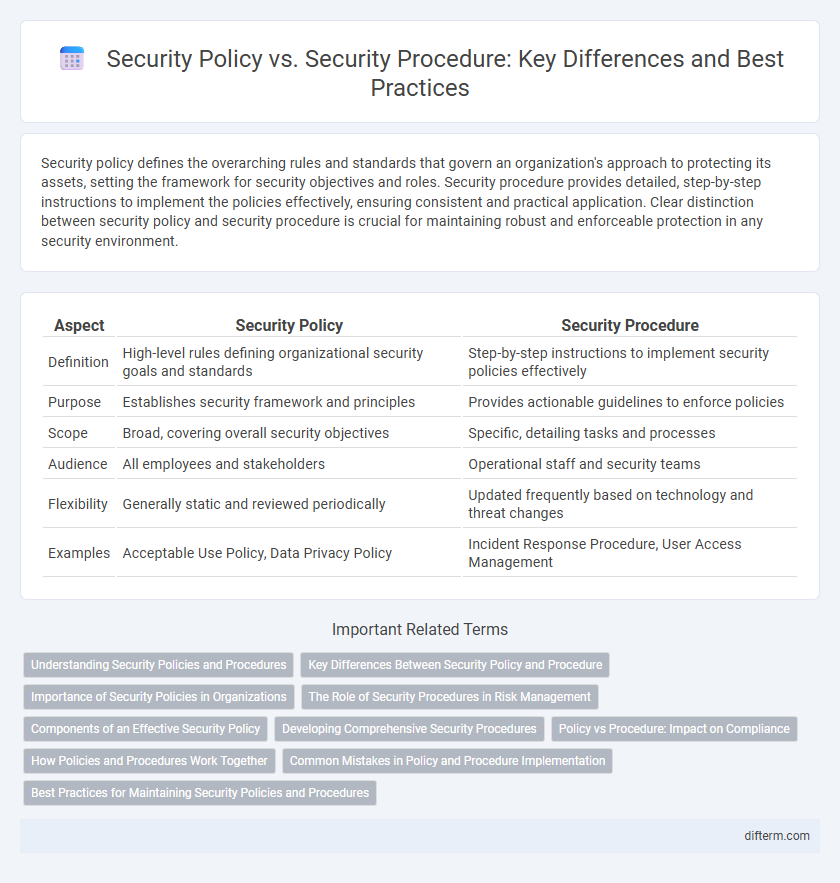
| Aspect | Security Policy | Security Procedure |
|---|---|---|
| Definition | High-level rules defining organizational security goals and standards | Step-by-step instructions to implement security policies effectively |
| Purpose | Establishes security framework and principles | Provides actionable guidelines to enforce policies |
| Scope | Broad, covering overall security objectives | Specific, detailing tasks and processes |
| Audience | All employees and stakeholders | Operational staff and security teams |
| Flexibility | Generally static and reviewed periodically | Updated frequently based on technology and threat changes |
| Examples | Acceptable Use Policy, Data Privacy Policy | Incident Response Procedure, User Access Management |
Understanding Security Policies and Procedures
Security policies define the organizational principles, rules, and frameworks designed to protect information assets and ensure compliance with regulatory requirements. Security procedures provide detailed, step-by-step instructions on how to implement these policies effectively in daily operations. Understanding the distinction between policies and procedures enhances an organization's ability to maintain robust security controls and respond proactively to potential threats.
Key Differences Between Security Policy and Procedure
Security policies establish the overarching principles, rules, and objectives that guide an organization's approach to information protection and risk management. Security procedures provide detailed, step-by-step instructions to implement the policies effectively, ensuring consistent execution by employees. The key difference lies in policies defining the "what" and "why," while procedures explain the "how" to maintain organizational security standards.
Importance of Security Policies in Organizations
Security policies establish the foundational framework and clear guidelines that define an organization's approach to protecting its digital and physical assets. These policies ensure consistent compliance with industry regulations, minimize risks, and foster a culture of accountability among employees. Effective security policies enable organizations to proactively address threats, reduce vulnerabilities, and maintain the integrity of sensitive information.
The Role of Security Procedures in Risk Management
Security procedures translate security policies into actionable steps, ensuring consistent risk mitigation across an organization. These procedures provide detailed instructions for implementing controls and responding to incidents, which reduces vulnerabilities and enhances compliance. Effective risk management relies on well-defined security procedures to operationalize policies and maintain organizational resilience.
Components of an Effective Security Policy
An effective security policy includes clearly defined objectives, roles, and responsibilities to guide organizational security efforts. It outlines acceptable use, access controls, incident response protocols, and compliance requirements to ensure consistent enforcement. Regular reviews and updates align the policy with emerging threats and regulatory changes, strengthening overall information security posture.
Developing Comprehensive Security Procedures
Developing comprehensive security procedures involves translating a security policy's framework into detailed, actionable steps that ensure consistent implementation and enforcement across an organization. These procedures specify roles, responsibilities, and specific actions required to mitigate risks, comply with regulatory requirements, and respond effectively to security incidents. Effective security procedures enhance organizational resilience by providing clear guidelines for operational security controls and employee behavior.
Policy vs Procedure: Impact on Compliance
Security policies establish the overarching rules and standards necessary for regulatory compliance, defining the framework organizations must follow to protect assets and data. Security procedures provide detailed, step-by-step instructions to implement these policies, ensuring consistent execution and operational adherence. The alignment between policy and procedure directly impacts compliance effectiveness by bridging strategic objectives with practical actions.
How Policies and Procedures Work Together
Security policies define the overarching rules and guidelines that govern an organization's approach to protecting its assets, while security procedures provide the detailed, actionable steps required to implement those policies effectively. Together, policies establish the framework for security objectives, and procedures ensure consistent execution and compliance with those objectives across all departments. The synergy between well-defined policies and precise procedures creates a robust security posture by aligning organizational goals with operational practices.
Common Mistakes in Policy and Procedure Implementation
Common mistakes in security policy and procedure implementation include lack of clear communication, resulting in employee confusion and inconsistent adherence to security protocols. Many organizations fail to regularly update policies, leading to outdated procedures that do not address emerging threats or compliance requirements. Insufficient training and lack of enforcement mechanisms further weaken the effectiveness of security measures, increasing vulnerability to cyberattacks and insider threats.
Best Practices for Maintaining Security Policies and Procedures
Effective security policies establish the framework for protecting organizational assets, while security procedures provide detailed, actionable steps to enforce those policies. Best practices for maintaining security policies and procedures include conducting regular reviews and updates to address emerging threats, ensuring employee training and awareness programs are in place, and implementing version control to track changes. Consistent documentation and management buy-in are critical for aligning security objectives with operational execution and regulatory compliance.
Security Policy vs Security Procedure Infographic
 difterm.com
difterm.com