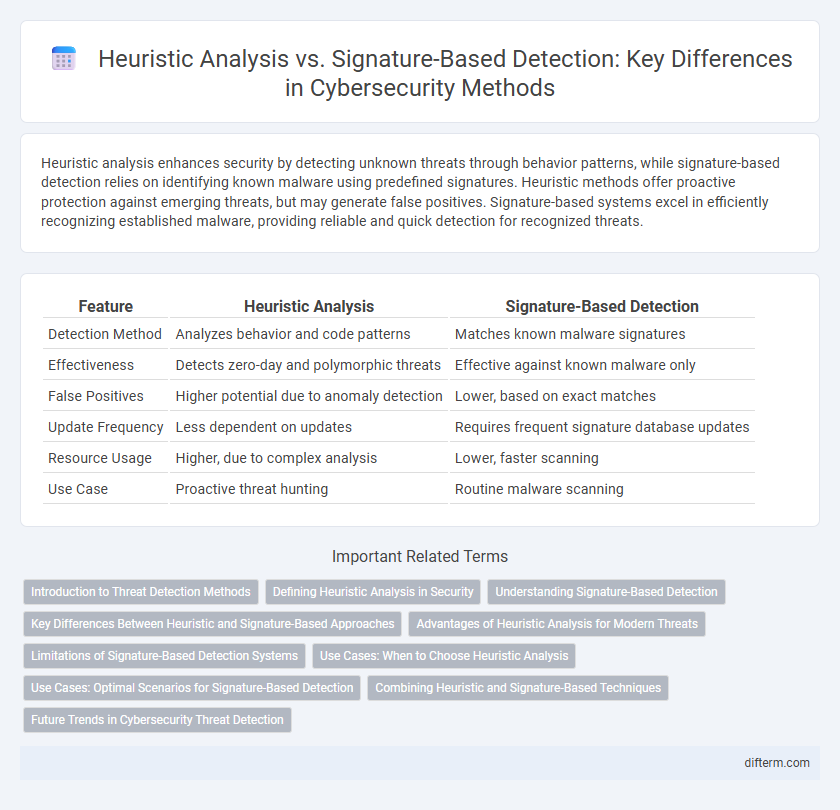
Heuristic analysis enhances security by detecting unknown threats through behavior patterns, while signature-based detection relies on identifying known malware using predefined signatures. Heuristic methods offer proactive protection against emerging threats, but may generate false positives. Signature-based systems excel in efficiently recognizing established malware, providing reliable and quick detection for recognized threats.
Table of Comparison
| Feature | Heuristic Analysis | Signature-Based Detection |
|---|---|---|
| Detection Method | Analyzes behavior and code patterns | Matches known malware signatures |
| Effectiveness | Detects zero-day and polymorphic threats | Effective against known malware only |
| False Positives | Higher potential due to anomaly detection | Lower, based on exact matches |
| Update Frequency | Less dependent on updates | Requires frequent signature database updates |
| Resource Usage | Higher, due to complex analysis | Lower, faster scanning |
| Use Case | Proactive threat hunting | Routine malware scanning |
Introduction to Threat Detection Methods
Heuristic analysis detects threats by analyzing behavior patterns and identifying anomalies, enabling early detection of zero-day and polymorphic malware. Signature-based detection relies on known malware signatures stored in databases, offering fast and accurate identification of previously discovered threats. Combining both methods enhances cybersecurity by balancing proactive threat detection with efficient recognition of established malware.
Defining Heuristic Analysis in Security
Heuristic analysis in security refers to a proactive method of detecting malware by examining code behavior and characteristics rather than relying solely on known virus signatures. This technique uses algorithms to identify suspicious activities and patterns that deviate from normal system operations, enabling the detection of zero-day threats and previously unknown malware. Heuristic analysis enhances security defenses by providing dynamic threat identification beyond static signature databases.
Understanding Signature-Based Detection
Signature-based detection relies on a database of known malware signatures to identify threats by matching code patterns, making it highly effective for quickly recognizing previously discovered viruses and malware. This method requires frequent updates to the signature database to maintain accuracy against evolving threats. While it excels at detecting known attacks, it is less effective against new or polymorphic malware that lacks an established signature.
Key Differences Between Heuristic and Signature-Based Approaches
Heuristic analysis detects threats by examining behavior patterns and anomalies, making it effective against new, unknown malware that lacks a known signature. Signature-based detection relies on a database of known malware signatures, enabling fast and accurate identification but struggling with zero-day threats. The key difference lies in heuristic methods' ability to identify emerging threats proactively, while signature-based techniques excel at recognizing previously identified malware.
Advantages of Heuristic Analysis for Modern Threats
Heuristic analysis excels in identifying zero-day threats and sophisticated malware by detecting abnormal behavior patterns rather than relying on known virus signatures, enabling proactive defense against evolving cyberattacks. This approach reduces false negatives in dynamic environments where signature databases may lag behind emerging threats. Its adaptive nature allows continuous learning and refinement, making it essential for combating polymorphic and metamorphic malware in modern cybersecurity landscapes.
Limitations of Signature-Based Detection Systems
Signature-based detection systems face limitations due to their reliance on known malware signatures, making them ineffective against zero-day threats and polymorphic viruses. These systems require constant updates to their signature databases, leading to delayed response times against emerging malware. Heuristic analysis overcomes this by examining suspicious behavior patterns, enabling detection of unknown and evolving threats.
Use Cases: When to Choose Heuristic Analysis
Heuristic analysis is ideal for detecting zero-day threats and polymorphic malware by analyzing behavioral patterns and anomalies rather than relying on known signatures. It excels in environments where new and evolving malware variants frequently emerge, providing proactive protection against unknown threats. Organizations prioritizing advanced threat detection and mitigation benefit from heuristic techniques to identify sophisticated attacks missed by signature-based detection.
Use Cases: Optimal Scenarios for Signature-Based Detection
Signature-based detection excels in identifying known malware by matching files and behaviors against a database of previously identified threats, making it optimal for environments with established threat profiles. It is highly effective in corporate networks and endpoint security where rapid identification and blocking of common viruses, worms, and trojans are critical. Regular updates to the signature database ensure accurate protection against the latest threats, minimizing false positives in stable, well-understood environments.
Combining Heuristic and Signature-Based Techniques
Integrating heuristic analysis with signature-based detection enhances security systems by leveraging pattern recognition alongside behavior-based anomaly detection, improving threat identification accuracy. Signature-based methods quickly identify known malware through predefined patterns, while heuristic techniques detect novel or mutated threats by analyzing suspicious behavior. This combined approach reduces false negatives and provides comprehensive protection against both established and emerging cyber threats.
Future Trends in Cybersecurity Threat Detection
Heuristic analysis leverages behavior-based algorithms to identify previously unknown threats by examining suspicious activities, while signature-based detection relies on known malware patterns for quick identification. Future trends in cybersecurity threat detection emphasize integrating artificial intelligence and machine learning to enhance heuristic analysis, enabling proactive defense against zero-day attacks and polymorphic malware. Advanced threat intelligence platforms will combine both methods, improving accuracy and reducing false positives in real-time security environments.
Heuristic Analysis vs Signature-Based Detection Infographic
 difterm.com
difterm.com