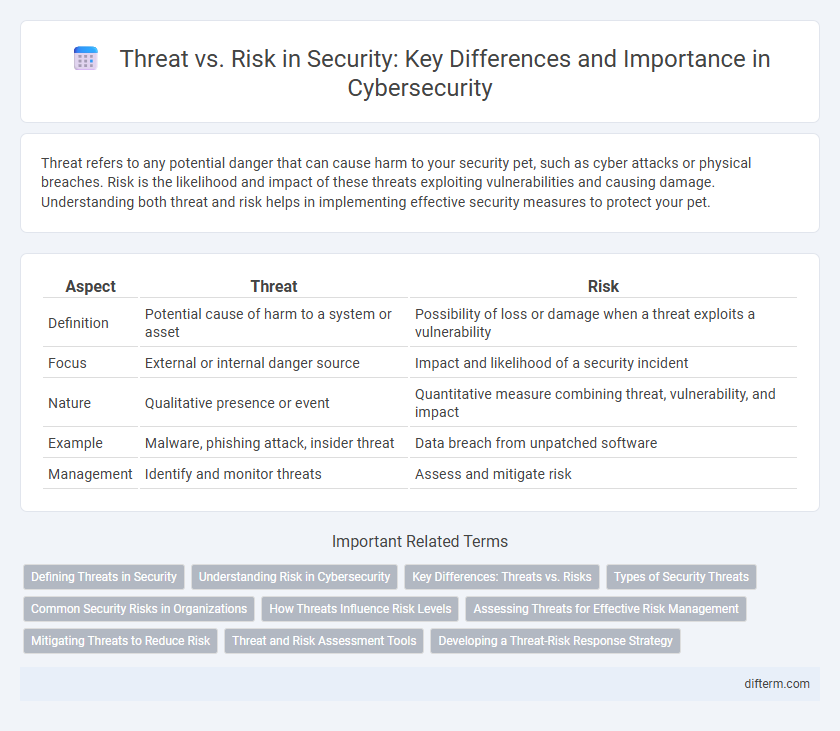
Threat refers to any potential danger that can cause harm to your security pet, such as cyber attacks or physical breaches. Risk is the likelihood and impact of these threats exploiting vulnerabilities and causing damage. Understanding both threat and risk helps in implementing effective security measures to protect your pet.
Table of Comparison
| Aspect | Threat | Risk |
|---|---|---|
| Definition | Potential cause of harm to a system or asset | Possibility of loss or damage when a threat exploits a vulnerability |
| Focus | External or internal danger source | Impact and likelihood of a security incident |
| Nature | Qualitative presence or event | Quantitative measure combining threat, vulnerability, and impact |
| Example | Malware, phishing attack, insider threat | Data breach from unpatched software |
| Management | Identify and monitor threats | Assess and mitigate risk |
Defining Threats in Security
Threats in security represent potential events or actions capable of causing harm to information systems, assets, or individuals. They encompass various sources such as cyberattacks, insider threats, natural disasters, and system vulnerabilities. Accurate identification and understanding of these threats are crucial for implementing effective security measures and minimizing organizational exposure.
Understanding Risk in Cybersecurity
Understanding risk in cybersecurity involves identifying potential threats and assessing their likelihood and impact on assets. Risk quantification combines threat probability with vulnerability and consequence analysis to prioritize security measures effectively. Implementing risk management frameworks enables organizations to mitigate vulnerabilities and reduce overall exposure to cyberattacks.
Key Differences: Threats vs. Risks
Threats represent potential sources of harm or malicious actions targeting assets, while risks measure the likelihood and impact of those threats exploiting vulnerabilities. Understanding threats involves identifying possible attackers or hazards, whereas assessing risks requires evaluating exposure, vulnerability, and potential damage. Effective security strategies prioritize risk management by mitigating vulnerabilities and reducing the probability and severity of threat exploitation.
Types of Security Threats
Security threats encompass various types such as malware, phishing, insider threats, and denial-of-service attacks, each exploiting different vulnerabilities within systems. Malware includes viruses, ransomware, and spyware designed to disrupt operations or steal sensitive data. Phishing targets human factors by deceiving users into revealing credentials, while insider threats involve employees or contractors misusing access, and denial-of-service attacks overwhelm resources to cause service outages.
Common Security Risks in Organizations
Common security risks in organizations include data breaches, insider threats, phishing attacks, and ransomware infections. These risks exploit vulnerabilities in IT infrastructure, human error, and inadequate security policies. Understanding the distinction between threat (a potential cause of harm) and risk (the likelihood and impact of that threat materializing) helps prioritize mitigation strategies effectively.
How Threats Influence Risk Levels
Threats directly impact risk levels by increasing the likelihood of a security breach or exploitation. The severity and frequency of threats determine the potential damage and urgency of risk mitigation strategies. Effective risk management requires continuous threat assessment to prioritize vulnerabilities and allocate resources efficiently.
Assessing Threats for Effective Risk Management
Assessing threats involves identifying potential sources of harm such as cyberattacks, insider threats, or physical breaches that could exploit vulnerabilities within an organization. Effective risk management relies on evaluating the likelihood and impact of these threats to prioritize security measures and allocate resources efficiently. Continuous monitoring and threat intelligence are essential to adapt defenses and minimize exposure in an evolving risk landscape.
Mitigating Threats to Reduce Risk
Mitigating threats involves identifying vulnerabilities and implementing security controls to prevent potential attacks, thereby directly lowering risk levels. Employing strategies such as intrusion detection systems, regular software updates, and employee training strengthens defenses against exploit attempts. Effective threat mitigation transforms uncertain hazards into manageable risks, ensuring robust cybersecurity posture.
Threat and Risk Assessment Tools
Threat and risk assessment tools play a critical role in identifying potential security vulnerabilities and evaluating their impact on organizational assets. These tools use data analytics, threat intelligence feeds, and automated scanning to detect and quantify risks, enabling proactive mitigation strategies. By integrating real-time monitoring and historical data analysis, they enhance decision-making and prioritize security investments effectively.
Developing a Threat-Risk Response Strategy
Developing a threat-risk response strategy requires identifying potential threats and assessing the risks they pose to an organization's assets and operations. By analyzing threat intelligence and quantifying risk levels using frameworks such as NIST or ISO 27001, security teams can prioritize mitigation efforts effectively. Implementing a combination of proactive measures, incident response plans, and continuous monitoring ensures resilience against evolving cyber threats and minimizes potential impact.
Threat vs Risk Infographic
 difterm.com
difterm.com