Cyber espionage involves the covert theft of sensitive information from individuals, organizations, or governments, aiming to gain strategic or competitive advantages. Cyber sabotage targets critical infrastructure or systems to disrupt operations, cause damage, or create chaos, often with a destructive intent. Understanding the distinction between these threats is essential for developing effective cybersecurity strategies to protect digital assets and national security.
Table of Comparison
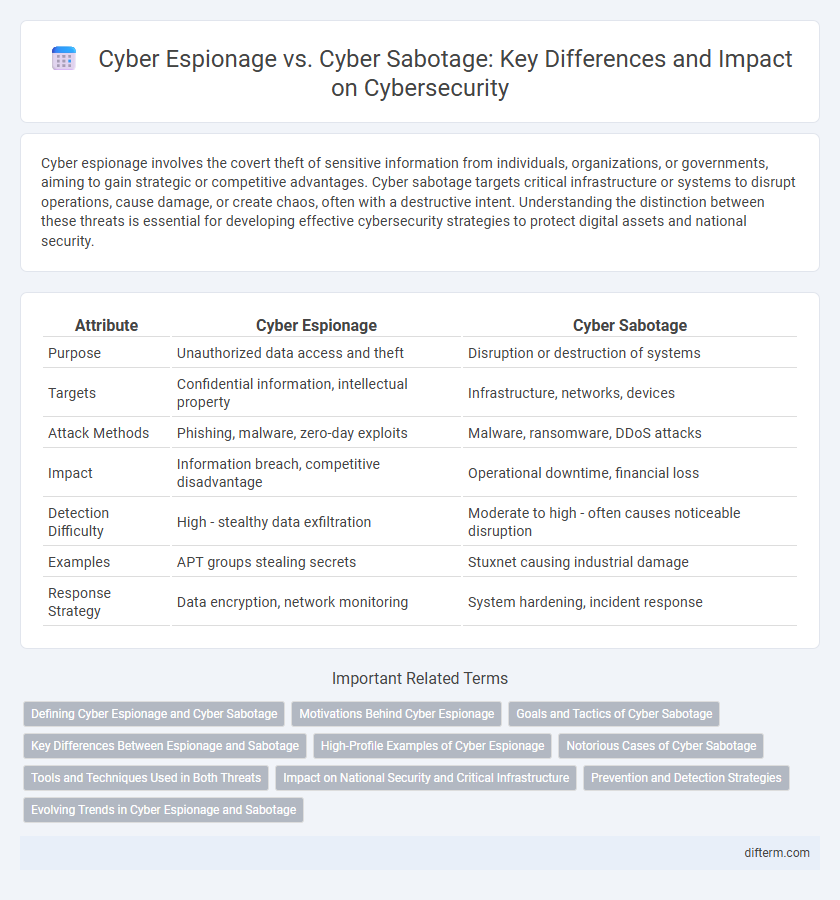
| Attribute | Cyber Espionage | Cyber Sabotage |
|---|---|---|
| Purpose | Unauthorized data access and theft | Disruption or destruction of systems |
| Targets | Confidential information, intellectual property | Infrastructure, networks, devices |
| Attack Methods | Phishing, malware, zero-day exploits | Malware, ransomware, DDoS attacks |
| Impact | Information breach, competitive disadvantage | Operational downtime, financial loss |
| Detection Difficulty | High - stealthy data exfiltration | Moderate to high - often causes noticeable disruption |
| Examples | APT groups stealing secrets | Stuxnet causing industrial damage |
| Response Strategy | Data encryption, network monitoring | System hardening, incident response |
Defining Cyber Espionage and Cyber Sabotage
Cyber espionage involves covertly infiltrating computer networks to steal sensitive information or intellectual property aimed at gaining a strategic advantage, often conducted by state-sponsored actors. Cyber sabotage refers to deliberate actions targeting digital infrastructure or systems to disrupt, damage, or destroy operations, leading to service outages or physical harm. Both tactics pose significant risks to national security, but espionage focuses on information theft while sabotage prioritizes operational disruption.
Motivations Behind Cyber Espionage
Cyber espionage primarily aims to gather confidential information, trade secrets, or intellectual property to gain strategic, economic, or political advantages. State-sponsored actors often target government agencies, defense contractors, and critical infrastructure to enhance national security or influence geopolitical dynamics. Unlike cyber sabotage, which focuses on disruption or damage, espionage emphasizes stealth and intelligence collection to inform decision-making processes.
Goals and Tactics of Cyber Sabotage
Cyber sabotage aims to disrupt, damage, or destroy critical infrastructure and information systems by deploying malware, ransomware, or coordinated attacks on operational technology. Tactics often include exploiting vulnerabilities in industrial control systems (ICS), launching distributed denial-of-service (DDoS) attacks, and employing zero-day exploits to maximize operational disruption. Unlike cyber espionage, which prioritizes stealth and data theft, cyber sabotage focuses on causing immediate and visible harm to target networks and physical assets.
Key Differences Between Espionage and Sabotage
Cyber espionage involves covertly infiltrating computer systems to gather sensitive information without detection, aiming at long-term intelligence advantage. Cyber sabotage targets the disruption, damage, or destruction of digital infrastructure, causing immediate operational failures or harm to physical assets. The key difference lies in espionage prioritizing stealthy data extraction, while sabotage centers on overt attacks aimed at impairing functionality or causing chaos.
High-Profile Examples of Cyber Espionage
High-profile examples of cyber espionage include the 2010 Stuxnet attack, which targeted Iran's nuclear facilities by infiltrating industrial control systems to gather intelligence and disrupt operations covertly. The 2014 Sony Pictures hack, attributed to North Korean operatives, involved the theft of sensitive corporate data and unreleased films, demonstrating the damaging effects of state-sponsored cyber espionage on both media and national security. Another notable incident is the 2015 Anthem data breach, where hackers accessed the personal information of nearly 80 million Americans, highlighting vulnerabilities in healthcare cybersecurity to espionage activities.
Notorious Cases of Cyber Sabotage
Notorious cases of cyber sabotage highlight the destructive potential of attacks targeting critical infrastructure and industrial control systems, such as the Stuxnet worm that disrupted Iran's nuclear facilities in 2010. The 2017 NotPetya malware campaign caused widespread operational chaos by crippling global logistics and financial sectors, demonstrating the catastrophic impact on essential services. These incidents emphasize the need for robust cybersecurity measures to defend against cyber sabotage's ability to cause physical and economic damage.
Tools and Techniques Used in Both Threats
Cyber espionage employs advanced malware, phishing campaigns, and zero-day exploits to stealthily infiltrate systems and extract sensitive data, often leveraging custom backdoors and keyloggers. Cyber sabotage uses destructive tools like ransomware, wipers, and distributed denial-of-service (DDoS) attacks to disrupt operations, targeting critical infrastructure with techniques that erase data or halt system functionalities. Both threats exploit vulnerabilities in software and human factors but differ in their end goals and specific toolsets tailored for data theft versus operational disruption.
Impact on National Security and Critical Infrastructure
Cyber espionage targets sensitive government information and defense secrets, risking national security by enabling foreign adversaries to gain strategic advantages. Cyber sabotage, through destructive attacks on critical infrastructure like power grids and communication networks, threatens national stability by causing widespread disruption and potential loss of life. Both tactics undermine public trust and can destabilize economic and political systems, necessitating robust cybersecurity measures to protect national assets.
Prevention and Detection Strategies
Cyber espionage primarily targets sensitive information through stealthy infiltration, making early detection via advanced threat intelligence and continuous network monitoring crucial. Cyber sabotage focuses on disrupting or damaging systems, requiring robust incident response plans and real-time anomaly detection to prevent operational downtime. Implementing multi-layered security frameworks, including behavioral analytics and endpoint protection, enhances prevention and detection capabilities against both threats.
Evolving Trends in Cyber Espionage and Sabotage
Evolving trends in cyber espionage reveal the increasing use of advanced persistent threats (APTs) and artificial intelligence to conduct stealthier data exfiltration campaigns targeting critical infrastructure and intellectual property. Cyber sabotage techniques are becoming more sophisticated, employing zero-day exploits and ransomware to disrupt operational technology and industrial control systems with precision. Emerging strategies highlight the blending of espionage and sabotage tactics to achieve long-term disruption, emphasizing the importance of adaptive cybersecurity frameworks and threat intelligence sharing.
Cyber Espionage vs Cyber Sabotage Infographic
 difterm.com
difterm.com