Hardening involves proactively configuring systems and applications to reduce vulnerabilities before exploitation occurs, whereas patching focuses on applying updates to fix known security flaws after their discovery. Effective security strategies require both approaches: hardening minimizes the attack surface initially, while patching ensures ongoing protection against emerging threats. Combining these methods strengthens overall system resilience and mitigates risks from both known and unknown vulnerabilities.
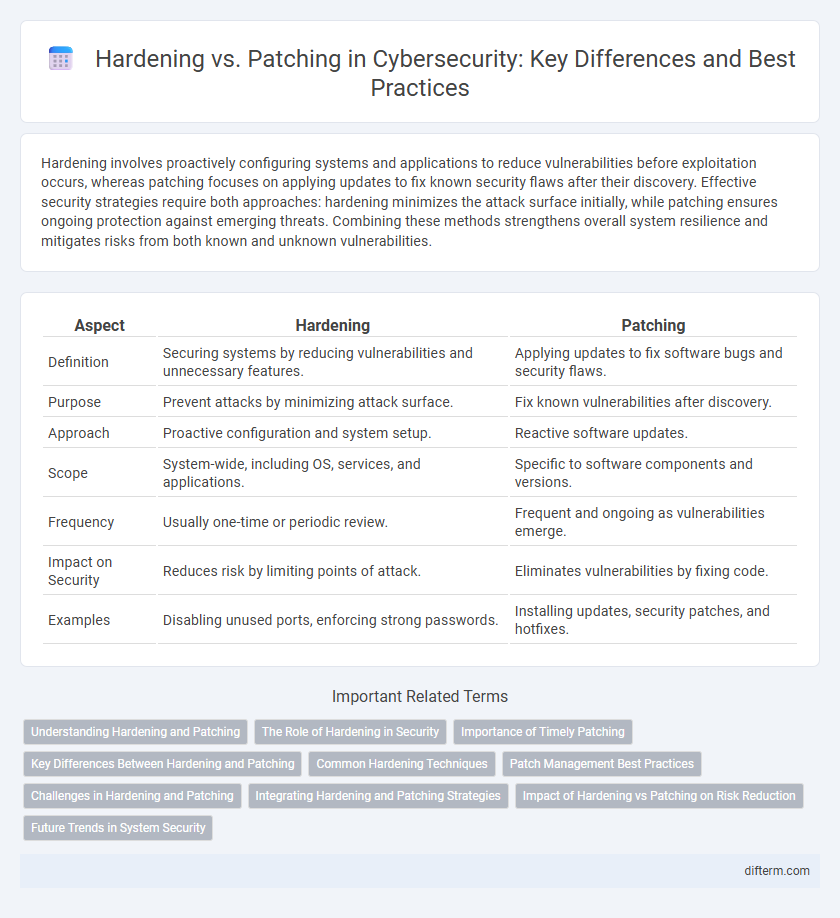
Table of Comparison
| Aspect | Hardening | Patching |
|---|---|---|
| Definition | Securing systems by reducing vulnerabilities and unnecessary features. | Applying updates to fix software bugs and security flaws. |
| Purpose | Prevent attacks by minimizing attack surface. | Fix known vulnerabilities after discovery. |
| Approach | Proactive configuration and system setup. | Reactive software updates. |
| Scope | System-wide, including OS, services, and applications. | Specific to software components and versions. |
| Frequency | Usually one-time or periodic review. | Frequent and ongoing as vulnerabilities emerge. |
| Impact on Security | Reduces risk by limiting points of attack. | Eliminates vulnerabilities by fixing code. |
| Examples | Disabling unused ports, enforcing strong passwords. | Installing updates, security patches, and hotfixes. |
Understanding Hardening and Patching
Understanding security hardening involves configuring systems and software to minimize vulnerabilities by disabling unnecessary services, closing open ports, and enforcing strict access controls. Patching focuses on applying updates that fix known software vulnerabilities and bugs to prevent exploitation by attackers. Both techniques are critical for reducing risk, with hardening proactively limiting attack surfaces and patching reactively addressing identified security flaws.
The Role of Hardening in Security
Hardening enhances security by proactively reducing vulnerabilities through configuration management, access control, and disabling unnecessary services, creating a resilient system baseline. It complements patching, which addresses specific flaws after they are discovered, by providing a robust infrastructure that minimizes potential attack surfaces. This proactive approach ensures continuous protection against threats and limits the impact of zero-day exploits before patches become available.
Importance of Timely Patching
Timely patching is critical in cybersecurity to close vulnerabilities that threat actors exploit, ensuring systems remain resistant to emerging attacks. Regular updates mitigate risks associated with zero-day exploits and reduce the attack surface, complementing hardening measures focused on system configuration. Neglecting prompt patch deployment can lead to breaches despite robust hardening, highlighting patch management's role in comprehensive security strategies.
Key Differences Between Hardening and Patching
Hardening involves implementing security measures to reduce vulnerabilities before threats can exploit them, such as configuring system settings and disabling unnecessary services. Patching focuses on fixing specific security flaws by applying updates or fixes released by software vendors to address discovered vulnerabilities. While hardening provides a proactive defense by minimizing the attack surface, patching offers reactive protection by correcting weaknesses after they are identified.
Common Hardening Techniques
Common hardening techniques in cybersecurity include disabling unnecessary services, applying least privilege principles, enforcing strong password policies, and configuring firewalls to restrict unauthorized access. Implementing system updates and securing configurations for operating systems, applications, and network devices reduces vulnerability exposure. Regular audits and vulnerability assessments help ensure that security controls remain effective and aligned with organizational policies.
Patch Management Best Practices
Effective patch management is crucial for maintaining system security by promptly identifying, testing, and deploying patches to address vulnerabilities. Implementing automated patch deployment tools minimizes human error and ensures consistent updates across all devices in the network. Regular auditing and prioritization based on risk assessment enhance protection against exploits while complementing security hardening practices.
Challenges in Hardening and Patching
Hardening faces challenges such as ensuring comprehensive configuration across diverse systems, managing complex security baselines, and avoiding disruptions to critical operations. Patching struggles with timely deployment due to testing requirements, compatibility issues, and addressing zero-day vulnerabilities before exploitation. Both approaches demand continual monitoring and resource allocation to maintain robust security postures.
Integrating Hardening and Patching Strategies
Integrating hardening and patching strategies creates a comprehensive security framework by reducing vulnerabilities through proactive system configuration and timely updates. Hardening minimizes the attack surface by disabling unnecessary services and enforcing strict access controls, while patching addresses existing software flaws to prevent exploitation. Combining these approaches ensures continuous protection against evolving threats and strengthens overall cybersecurity resilience.
Impact of Hardening vs Patching on Risk Reduction
Hardening systematically reduces attack surface by configuring systems and applications to enforce strict security controls and eliminate unnecessary services. Patching addresses vulnerabilities by updating software to fix known security flaws, mitigating specific risks tied to discovered exploits. Both approaches complement each other, with hardening providing broad preventive defense and patching delivering targeted vulnerability resolution, leading to significant overall risk reduction.
Future Trends in System Security
Future trends in system security emphasize a balanced approach combining hardening techniques, such as configuration management and reducing attack surfaces, with continuous patching to address emerging vulnerabilities. Automation and AI-driven tools are increasingly leveraged to predict potential threats and deploy patches proactively, enabling adaptive defenses against sophisticated cyberattacks. Zero-trust architecture and cloud-native security measures also shape the evolution of robust system protection strategies.
Hardening vs Patching Infographic
 difterm.com
difterm.com