Vulnerabilities are weaknesses or flaws within a security system that can be discovered through analysis or testing. Exploits are specific techniques or code used by attackers to take advantage of these vulnerabilities and compromise system integrity. Understanding the difference between vulnerabilities and exploits is crucial for effective cybersecurity risk management and defense strategies.
Table of Comparison
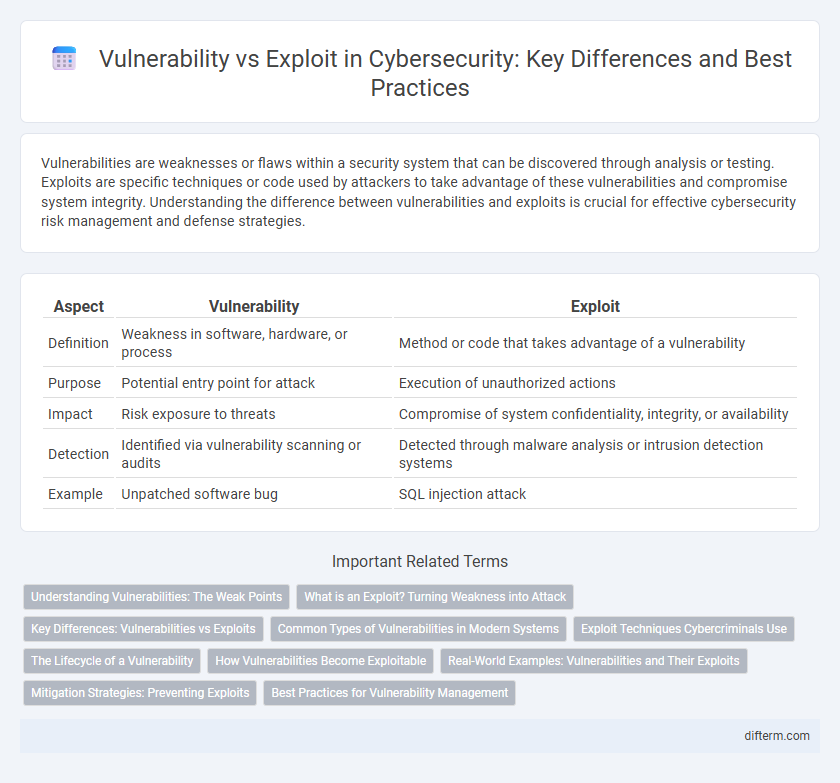
| Aspect | Vulnerability | Exploit |
|---|---|---|
| Definition | Weakness in software, hardware, or process | Method or code that takes advantage of a vulnerability |
| Purpose | Potential entry point for attack | Execution of unauthorized actions |
| Impact | Risk exposure to threats | Compromise of system confidentiality, integrity, or availability |
| Detection | Identified via vulnerability scanning or audits | Detected through malware analysis or intrusion detection systems |
| Example | Unpatched software bug | SQL injection attack |
Understanding Vulnerabilities: The Weak Points
Vulnerabilities are weaknesses or flaws within software, hardware, or network systems that attackers can target to gain unauthorized access or cause damage. These weak points often arise from coding errors, misconfigurations, or outdated software lacking security patches. Understanding and identifying vulnerabilities is critical for implementing effective security measures and preventing exploits that leverage these weaknesses to compromise systems.
What is an Exploit? Turning Weakness into Attack
An exploit is a specific technique or code that leverages a vulnerability within a system to gain unauthorized access or cause unintended behavior. By turning security weaknesses into attack vectors, exploits enable hackers to bypass defenses, escalate privileges, or execute malicious activities. Understanding exploits is crucial for developing effective security patches and improving overall system resilience.
Key Differences: Vulnerabilities vs Exploits
Vulnerabilities are weaknesses or flaws in software, hardware, or processes that can be targeted by attackers, whereas exploits are the specific methods or code used to take advantage of these vulnerabilities. Understanding the key difference between a vulnerability and an exploit is critical for cybersecurity professionals to assess risk and implement effective safeguards. Vulnerabilities exist independently as potential security gaps, while exploits actively leverage these gaps to compromise system integrity, confidentiality, or availability.
Common Types of Vulnerabilities in Modern Systems
Common types of vulnerabilities in modern systems include buffer overflows, SQL injection, cross-site scripting (XSS), and improper authentication mechanisms. These weaknesses allow attackers to execute unauthorized commands, access sensitive data, or escalate privileges within a network. Understanding and mitigating these vulnerabilities is crucial to preventing exploits that can compromise system integrity and confidentiality.
Exploit Techniques Cybercriminals Use
Exploit techniques cybercriminals use include buffer overflow attacks, SQL injection, and phishing campaigns designed to leverage existing system vulnerabilities. Advanced Persistent Threats (APTs) often combine social engineering with zero-day exploits to gain unauthorized access and maintain a foothold within networks. Understanding these methods is crucial for developing proactive defense mechanisms and enhancing cybersecurity resilience.
The Lifecycle of a Vulnerability
The lifecycle of a vulnerability begins with its identification, where security researchers or automated tools detect a software flaw that could be exploited. During the development stage, exploits are crafted to take advantage of this vulnerability, often targeting unpatched systems. Once public disclosure occurs, patches are typically released, but active exploitation may continue if mitigation measures are delayed or improperly applied.
How Vulnerabilities Become Exploitable
Vulnerabilities become exploitable when attackers identify and leverage weaknesses in software, hardware, or network configurations to gain unauthorized access or cause harm. Exploits often arise through the combination of unpatched security flaws, insufficient access controls, or social engineering techniques that enable attackers to bypass protections. Effective vulnerability management and continuous monitoring are critical to identifying potential attack vectors before they can be exploited.
Real-World Examples: Vulnerabilities and Their Exploits
The Heartbleed vulnerability in OpenSSL allowed attackers to exploit a flaw in the heartbeat extension, exposing sensitive data like private keys and passwords from millions of servers worldwide. Another example is the EternalBlue vulnerability in Windows SMB protocol, which was exploited by the WannaCry ransomware, causing widespread disruption across industries. These real-world cases demonstrate how vulnerabilities become critical threats when exploited, emphasizing the importance of timely patching and vulnerability management.
Mitigation Strategies: Preventing Exploits
Implementing regular patch management and software updates addresses vulnerabilities before they can be exploited by attackers. Network segmentation and robust access controls limit the attack surface and contain potential breaches from exploited weaknesses. Employing intrusion detection systems and continuous monitoring enhances early identification and response to exploit attempts, strengthening overall cybersecurity defenses.
Best Practices for Vulnerability Management
Effective vulnerability management requires timely identification and prioritization of security weaknesses based on their potential impact and exploitability. Implementing automated scanning tools combined with continuous monitoring helps organizations detect vulnerabilities before attackers can exploit them. Patching known vulnerabilities promptly and conducting regular risk assessments are essential best practices to minimize exposure to exploits and protect critical assets.
Vulnerability vs Exploit Infographic
 difterm.com
difterm.com