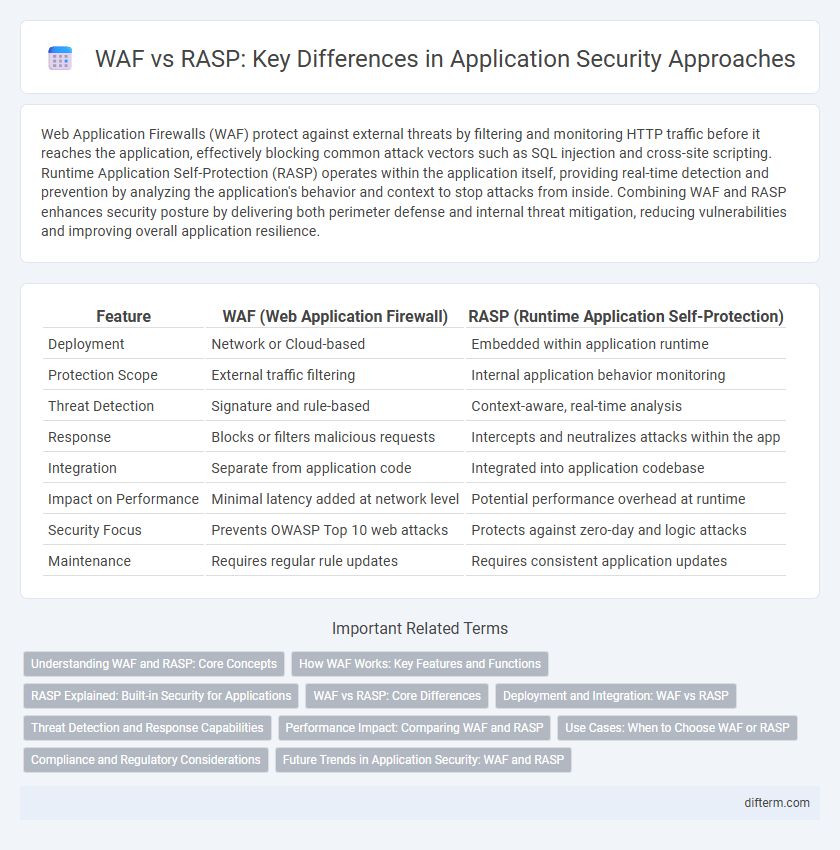
Web Application Firewalls (WAF) protect against external threats by filtering and monitoring HTTP traffic before it reaches the application, effectively blocking common attack vectors such as SQL injection and cross-site scripting. Runtime Application Self-Protection (RASP) operates within the application itself, providing real-time detection and prevention by analyzing the application's behavior and context to stop attacks from inside. Combining WAF and RASP enhances security posture by delivering both perimeter defense and internal threat mitigation, reducing vulnerabilities and improving overall application resilience.
Table of Comparison
| Feature | WAF (Web Application Firewall) | RASP (Runtime Application Self-Protection) |
|---|---|---|
| Deployment | Network or Cloud-based | Embedded within application runtime |
| Protection Scope | External traffic filtering | Internal application behavior monitoring |
| Threat Detection | Signature and rule-based | Context-aware, real-time analysis |
| Response | Blocks or filters malicious requests | Intercepts and neutralizes attacks within the app |
| Integration | Separate from application code | Integrated into application codebase |
| Impact on Performance | Minimal latency added at network level | Potential performance overhead at runtime |
| Security Focus | Prevents OWASP Top 10 web attacks | Protects against zero-day and logic attacks |
| Maintenance | Requires regular rule updates | Requires consistent application updates |
Understanding WAF and RASP: Core Concepts
Web Application Firewall (WAF) protects web applications by filtering and monitoring HTTP traffic to block malicious requests, operating largely at the network perimeter. Runtime Application Self-Protection (RASP) integrates directly within the application runtime, providing real-time detection and prevention of attacks from inside the application environment. Understanding WAF and RASP highlights how WAF focuses on external threat filtering, while RASP delivers fine-grained security by analyzing application behaviors during execution.
How WAF Works: Key Features and Functions
A Web Application Firewall (WAF) protects web applications by filtering and monitoring HTTP traffic between a web application and the internet, blocking malicious requests such as SQL injection, cross-site scripting (XSS), and other OWASP top 10 threats. Key features of a WAF include rule-based filtering, real-time traffic analysis, and customizable security policies that adapt to application-specific vulnerabilities. It functions by inspecting incoming and outgoing traffic at the HTTP/HTTPS layer, applying signature-based detection and anomaly behavior analysis to prevent attacks before they reach the application server.
RASP Explained: Built-in Security for Applications
Runtime Application Self-Protection (RASP) is a security technology integrated directly into an application's runtime environment, providing real-time protection by detecting and blocking attacks as they occur. Unlike traditional Web Application Firewalls (WAFs) that operate at the network perimeter, RASP analyzes application behavior internally to prevent threats like SQL injection, cross-site scripting, and zero-day exploits with greater accuracy. This built-in security approach reduces false positives and enhances application resilience by using contextual awareness of the app's logic and data flow.
WAF vs RASP: Core Differences
Web Application Firewall (WAF) operates as an external barrier that monitors and filters HTTP traffic to protect web applications from common threats such as SQL injection and cross-site scripting. Runtime Application Self-Protection (RASP) integrates within the application runtime environment, providing real-time detection and prevention by analyzing application behavior from the inside. Core differences include WAF's perimeter defense approach versus RASP's in-app security, with WAF focusing on traffic inspection and RASP offering granular protection through direct application code interaction.
Deployment and Integration: WAF vs RASP
WAF (Web Application Firewall) is deployed at the network edge, filtering and monitoring HTTP traffic between the internet and web applications, making it faster to implement without touching application code. RASP (Runtime Application Self-Protection) integrates directly into the application runtime environment, providing deeper security by detecting and blocking threats from within the application itself. WAF offers easier deployment with broad coverage, while RASP requires integration within the application, offering precise, context-aware protection tailored to the specific application environment.
Threat Detection and Response Capabilities
Web Application Firewalls (WAF) provide perimeter-based threat detection by filtering and blocking malicious HTTP traffic, effectively mitigating common attacks like SQL injection and cross-site scripting. Runtime Application Self-Protection (RASP) operates within the application, delivering real-time threat detection and response by monitoring application behavior and intercepting attacks from inside the runtime environment. RASP's deeper integration enables more precise threat identification and immediate mitigation actions, reducing false positives and enhancing overall security posture.
Performance Impact: Comparing WAF and RASP
Web Application Firewalls (WAF) typically introduce latency by inspecting and filtering incoming traffic before it reaches the application, which can affect overall response times under high loads. Runtime Application Self-Protection (RASP) operates within the application process, enabling real-time threat detection with minimal performance degradation by analyzing application behavior directly. Performance impact varies based on deployment scale and traffic volume, but RASP generally offers more efficient resource utilization compared to WAF for dynamic, runtime security.
Use Cases: When to Choose WAF or RASP
Web Application Firewalls (WAF) are ideal for organizations seeking perimeter protection against common threats like SQL injection and cross-site scripting, especially in environments with frequent external attacks and compliance requirements. Runtime Application Self-Protection (RASP) is best suited for applications needing real-time, in-depth security by monitoring and blocking threats from within the application itself, often used in dynamic DevOps environments with frequent code changes. Choosing WAF or RASP depends on factors such as attack surface, deployment complexity, and the need for immediate threat detection inside the application context.
Compliance and Regulatory Considerations
Web Application Firewalls (WAF) provide a critical layer of defense by filtering and monitoring HTTP traffic, helping organizations comply with standards like PCI DSS and GDPR through real-time attack prevention. Runtime Application Self-Protection (RASP) integrates security directly into the application, offering enhanced visibility into application behaviors and internal threat detection that supports compliance with evolving regulatory frameworks. Combining WAF and RASP technologies ensures comprehensive coverage for regulatory requirements by addressing both external threats and insider vulnerabilities.
Future Trends in Application Security: WAF and RASP
Future trends in application security emphasize the integration of Web Application Firewalls (WAF) with Runtime Application Self-Protection (RASP) to enhance real-time threat detection and response. Advances in machine learning and AI-driven analytics are enabling WAF and RASP to provide adaptive security that evolves with emerging vulnerabilities. This convergence supports proactive defense mechanisms that reduce exploitation windows and improve overall application resilience.
WAF vs RASP Infographic
 difterm.com
difterm.com