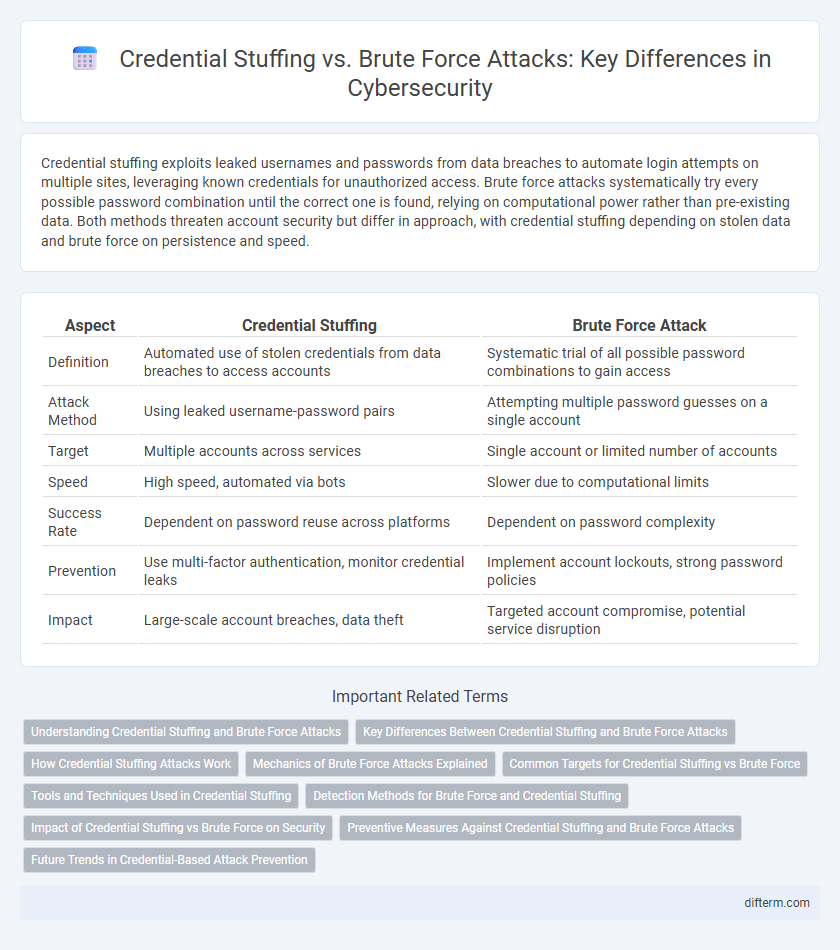
Credential stuffing exploits leaked usernames and passwords from data breaches to automate login attempts on multiple sites, leveraging known credentials for unauthorized access. Brute force attacks systematically try every possible password combination until the correct one is found, relying on computational power rather than pre-existing data. Both methods threaten account security but differ in approach, with credential stuffing depending on stolen data and brute force on persistence and speed.
Table of Comparison
| Aspect | Credential Stuffing | Brute Force Attack |
|---|---|---|
| Definition | Automated use of stolen credentials from data breaches to access accounts | Systematic trial of all possible password combinations to gain access |
| Attack Method | Using leaked username-password pairs | Attempting multiple password guesses on a single account |
| Target | Multiple accounts across services | Single account or limited number of accounts |
| Speed | High speed, automated via bots | Slower due to computational limits |
| Success Rate | Dependent on password reuse across platforms | Dependent on password complexity |
| Prevention | Use multi-factor authentication, monitor credential leaks | Implement account lockouts, strong password policies |
| Impact | Large-scale account breaches, data theft | Targeted account compromise, potential service disruption |
Understanding Credential Stuffing and Brute Force Attacks
Credential stuffing exploits leaked username and password pairs from previous breaches to access multiple accounts automatically, relying on users reusing credentials across sites. Brute force attacks systematically attempt every possible password combination to gain unauthorized access, often targeting single accounts with high computational effort. Understanding these attack vectors highlights the importance of using unique, strong passwords and implementing multi-factor authentication to mitigate risks.
Key Differences Between Credential Stuffing and Brute Force Attacks
Credential stuffing exploits leaked usernames and passwords from previous breaches to automate login attempts, targeting valid credentials for unauthorized access. Brute force attacks systematically try every possible combination of characters to guess passwords without relying on prior data. The primary difference lies in credential stuffing leveraging stolen data for informed attacks, whereas brute force attacks use exhaustive trial-and-error methods.
How Credential Stuffing Attacks Work
Credential stuffing attacks operate by leveraging large databases of leaked username and password pairs obtained from previous data breaches to automate login attempts on multiple websites. Attackers use specialized software to rapidly test these stolen credentials across numerous accounts, exploiting reused passwords to gain unauthorized access. This method contrasts with brute force attacks by relying on existing valid credentials rather than systematically guessing passwords.
Mechanics of Brute Force Attacks Explained
Brute force attacks involve systematically attempting every possible combination of passwords until the correct one is found, relying on computational power to crack credentials. Unlike credential stuffing, which uses leaked username-password pairs, brute force attacks target a single account with numerous password guesses. Attackers often utilize automated tools and bots to accelerate the guessing process, exploiting weak or easily guessable passwords to gain unauthorized access.
Common Targets for Credential Stuffing vs Brute Force
Credential stuffing primarily targets popular online platforms such as social media, e-commerce, and financial services where users often reuse passwords across multiple accounts. Brute force attacks commonly focus on login portals of enterprise systems, websites with weak password policies, and network devices with default or easily guessable credentials. Both attack methods exploit vulnerabilities in user authentication but differ in their approach and preferred targets.
Tools and Techniques Used in Credential Stuffing
Credential stuffing leverages automated tools like Sentry MBA, Snipr, and OpenBullet to rapidly test stolen username-password pairs across multiple websites, exploiting users' habit of password reuse. These tools utilize proxy networks and CAPTCHA-solving services to evade detection and bypass security measures. Advanced techniques include IP rotation, multi-threading, and the integration of machine learning algorithms to optimize hit rates and avoid account lockouts.
Detection Methods for Brute Force and Credential Stuffing
Brute force attacks are detected by monitoring repeated failed login attempts from a single IP address or user account, using anomaly detection systems that flag rapid, consecutive password guesses. Credential stuffing is identified through behavior analysis that tracks login patterns, such as multiple login attempts using leaked credentials across different accounts or geographic locations, combined with device fingerprinting and IP reputation checks. Both methods benefit from multi-factor authentication enforcement and rate limiting to prevent automated attack success.
Impact of Credential Stuffing vs Brute Force on Security
Credential stuffing significantly escalates security risks by exploiting massive databases of leaked username-password pairs to automate unauthorized account access, leading to data breaches and financial losses. Brute force attacks, while slower and more resource-intensive, systematically attempt numerous password combinations to compromise accounts, often triggering security defenses like account lockouts. The impact of credential stuffing is more extensive due to its scale and efficiency in bypassing traditional security measures compared to brute force attacks.
Preventive Measures Against Credential Stuffing and Brute Force Attacks
Implementing multi-factor authentication (MFA) significantly reduces the risk of credential stuffing and brute force attacks by requiring additional verification beyond passwords. Employing rate limiting and IP blacklisting helps to detect and block suspicious login attempts. Regularly updating password policies and encouraging the use of unique, complex passwords further strengthen defenses against unauthorized access.
Future Trends in Credential-Based Attack Prevention
Emerging trends in credential-based attack prevention emphasize leveraging advanced machine learning algorithms to detect anomalous login behaviors indicative of credential stuffing and brute force attacks. Implementing adaptive multi-factor authentication (MFA) systems dynamically adjusts security protocols based on real-time risk assessments, enhancing resistance to automated credential attacks. Integration of zero-trust architecture frameworks further reduces attack surfaces by enforcing continuous verification, limiting unauthorized access despite compromised credentials.
Credential Stuffing vs Brute Force Attack Infographic
 difterm.com
difterm.com