Physical security involves protecting tangible assets such as buildings, equipment, and personnel from unauthorized access or damage, using measures like locks, surveillance cameras, and security guards. Logical security focuses on safeguarding digital information and systems through authentication protocols, encryption, firewalls, and access controls. Both types of security are essential for a comprehensive defense strategy, ensuring protection against physical breaches and cyber threats.
Table of Comparison
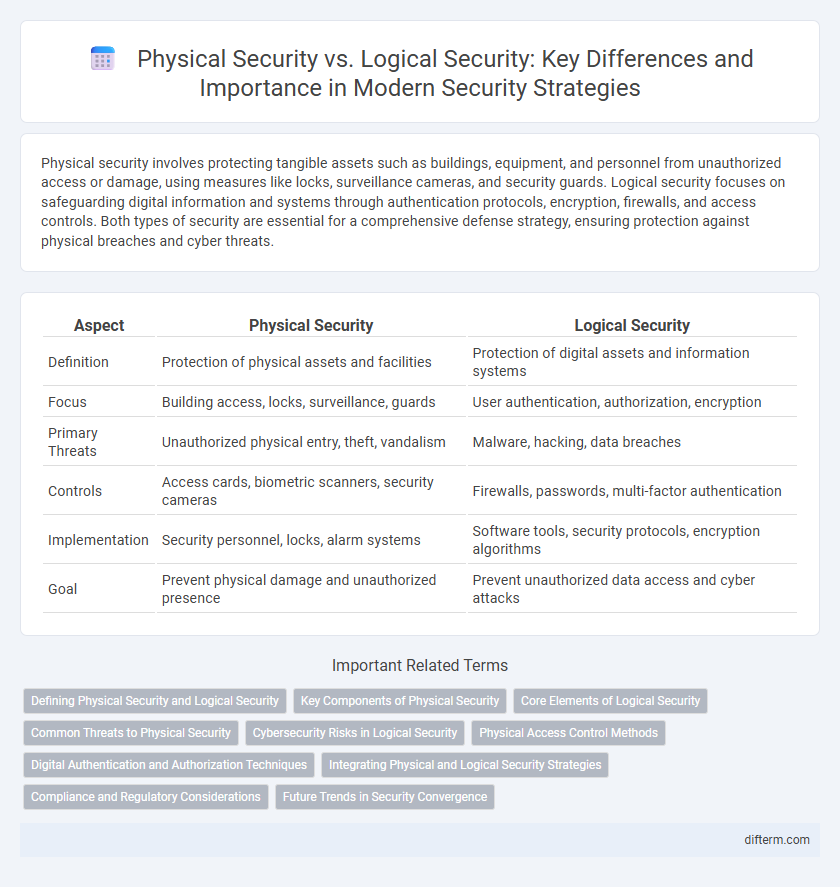
| Aspect | Physical Security | Logical Security |
|---|---|---|
| Definition | Protection of physical assets and facilities | Protection of digital assets and information systems |
| Focus | Building access, locks, surveillance, guards | User authentication, authorization, encryption |
| Primary Threats | Unauthorized physical entry, theft, vandalism | Malware, hacking, data breaches |
| Controls | Access cards, biometric scanners, security cameras | Firewalls, passwords, multi-factor authentication |
| Implementation | Security personnel, locks, alarm systems | Software tools, security protocols, encryption algorithms |
| Goal | Prevent physical damage and unauthorized presence | Prevent unauthorized data access and cyber attacks |
Defining Physical Security and Logical Security
Physical security involves protecting tangible assets such as buildings, equipment, and personnel from physical threats like theft, vandalism, or natural disasters using barriers, surveillance, and access controls. Logical security refers to safeguarding digital information and IT systems through measures including firewalls, encryption, authentication protocols, and antivirus software. Both security types are critical for comprehensive protection against diverse risks in organizational environments.
Key Components of Physical Security
Physical security encompasses key components such as access control systems, surveillance cameras, security guards, and environmental controls like fire suppression and temperature regulation. These elements work together to protect tangible assets from unauthorized access, theft, or damage. Effective physical security integrates barriers, monitoring devices, and response protocols to ensure a secure environment.
Core Elements of Logical Security
Logical security centers on core elements such as authentication, authorization, and encryption to protect digital assets from unauthorized access. Access controls enforce user permissions, ensuring only verified users can interact with sensitive systems and data. Continuous monitoring and intrusion detection systems are also critical to identify and respond to potential security threats in real time.
Common Threats to Physical Security
Common threats to physical security include unauthorized access, theft, vandalism, natural disasters, and insider threats such as employee sabotage. These risks compromise the confidentiality, integrity, and availability of critical assets by enabling physical breaches that can lead to data loss or operational disruption. Implementing access controls, surveillance systems, and environmental safeguards is essential to mitigate these physical security vulnerabilities.
Cybersecurity Risks in Logical Security
Logical security faces significant cybersecurity risks such as unauthorized access, malware infiltration, and insider threats that exploit software vulnerabilities and weak authentication protocols. Cyberattacks targeting logical security can lead to data breaches, financial loss, and compromised sensitive information within IT systems. Effective implementation of multi-factor authentication, encryption, and continuous monitoring is essential to mitigate these logical security risks.
Physical Access Control Methods
Physical access control methods include locks, biometric scanners, security guards, and surveillance cameras designed to prevent unauthorized entry to sensitive areas. These mechanisms ensure that only authorized personnel can access physical spaces, reducing the risk of theft, vandalism, or sabotage. Unlike logical security, which protects data and systems through software-based controls, physical security focuses on tangible barriers and monitoring to safeguard assets.
Digital Authentication and Authorization Techniques
Digital authentication techniques such as biometrics, multi-factor authentication, and digital certificates strengthen logical security by verifying user identities before granting access. Authorization mechanisms, including role-based access control (RBAC) and attribute-based access control (ABAC), govern user permissions and ensure that only authorized individuals can access sensitive digital resources. Physical security complements these methods by protecting hardware and infrastructure from unauthorized physical access, thus maintaining the integrity of authentication devices and data centers.
Integrating Physical and Logical Security Strategies
Integrating physical and logical security strategies enhances overall protection by creating a unified defense against threats targeting both tangible assets and digital information systems. Coordination between access control systems, surveillance technologies, and cybersecurity protocols ensures seamless monitoring and response to potential security breaches. Leveraging integrated platforms enables real-time data sharing, improving incident detection and risk management across physical and logical security domains.
Compliance and Regulatory Considerations
Physical security measures such as access controls, surveillance systems, and environmental safeguards are essential to comply with regulatory standards like HIPAA, PCI-DSS, and GDPR, which mandate protection of sensitive data and infrastructure. Logical security involves protocols like encryption, authentication, and network security to ensure data integrity and confidentiality in alignment with compliance requirements. Organizations must implement integrated physical and logical security controls to meet comprehensive regulatory frameworks and avoid penalties.
Future Trends in Security Convergence
Future trends in security convergence emphasize the integration of physical security systems, such as access control and surveillance, with logical security measures like identity management and network protection. Advances in AI-driven analytics and IoT connectivity enable unified threat detection platforms that correlate physical events with cyber incidents for real-time response. This convergence enhances organizational resilience by providing comprehensive situational awareness and automated security orchestration across physical and digital domains.
Physical Security vs Logical Security Infographic
 difterm.com
difterm.com