Cross-Site Scripting (XSS) attacks inject malicious scripts into trusted websites, compromising user data and session integrity by exploiting vulnerabilities in web applications. Cross-Site Request Forgery (CSRF) tricks authenticated users into submitting unwanted actions by exploiting their active sessions, effectively forcing unintended commands on web applications. Implementing input validation, output encoding, and anti-CSRF tokens are essential to protect against these distinct but dangerous security threats.
Table of Comparison
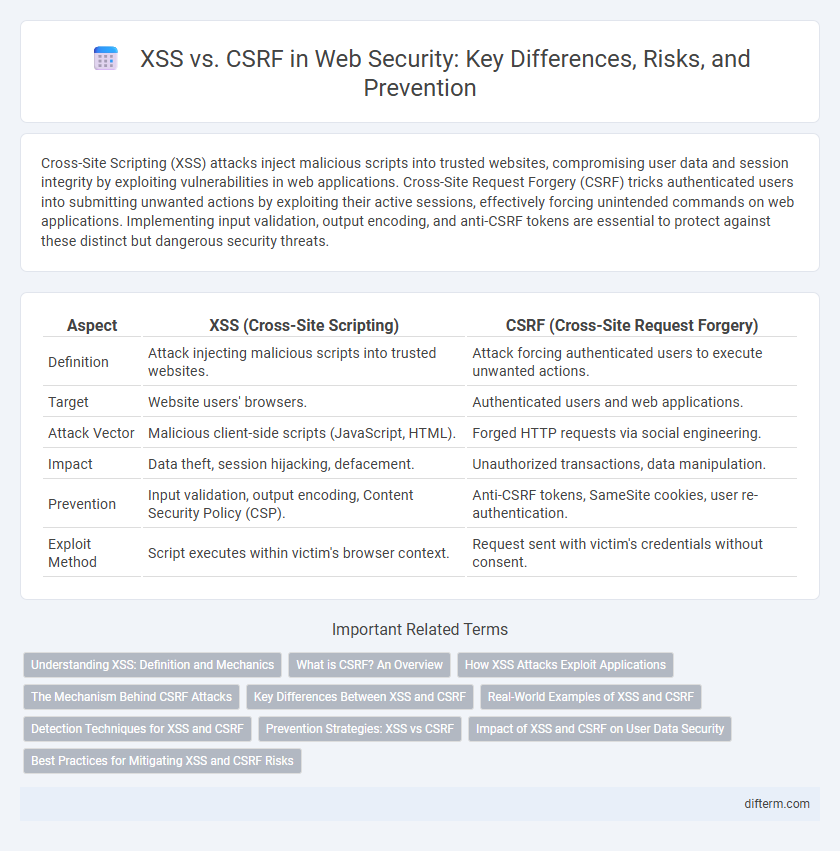
| Aspect | XSS (Cross-Site Scripting) | CSRF (Cross-Site Request Forgery) |
|---|---|---|
| Definition | Attack injecting malicious scripts into trusted websites. | Attack forcing authenticated users to execute unwanted actions. |
| Target | Website users' browsers. | Authenticated users and web applications. |
| Attack Vector | Malicious client-side scripts (JavaScript, HTML). | Forged HTTP requests via social engineering. |
| Impact | Data theft, session hijacking, defacement. | Unauthorized transactions, data manipulation. |
| Prevention | Input validation, output encoding, Content Security Policy (CSP). | Anti-CSRF tokens, SameSite cookies, user re-authentication. |
| Exploit Method | Script executes within victim's browser context. | Request sent with victim's credentials without consent. |
Understanding XSS: Definition and Mechanics
Cross-Site Scripting (XSS) is a web security vulnerability allowing attackers to inject malicious scripts into trusted websites, exploiting browsers to execute unauthorized code. The attack typically targets client-side scripts to steal cookies, session tokens, or manipulate the Document Object Model (DOM). Understanding the mechanics involves recognizing input validation failures and output encoding gaps that enable script injection and execution in a victim's browser.
What is CSRF? An Overview
Cross-Site Request Forgery (CSRF) is a security vulnerability that tricks a user into submitting unintended actions on a web application where they are authenticated. This exploit takes advantage of the user's existing session credentials to perform malicious requests without their knowledge. CSRF protection techniques include the use of anti-CSRF tokens, same-site cookies, and strict referer header validation to prevent unauthorized commands.
How XSS Attacks Exploit Applications
XSS attacks exploit vulnerabilities in web applications by injecting malicious scripts into trusted websites, allowing attackers to execute unauthorized code in users' browsers. These scripts can steal sensitive data such as cookies, session tokens, or manipulate the website content to deceive users. Unlike CSRF, which forces unauthorized actions through authenticated users, XSS directly compromises client-side security by targeting the application's input validation and output encoding mechanisms.
The Mechanism Behind CSRF Attacks
CSRF attacks exploit the trust that a website has in a user's browser by tricking the browser into sending unauthorized requests without the user's knowledge. This is achieved through malicious scripts embedded in third-party websites, which leverage the user's active session cookies or authentication tokens to perform actions on behalf of the user. Unlike XSS, which injects malicious code into a trusted website, CSRF relies on exploiting authenticated sessions and the lack of proper request verification mechanisms.
Key Differences Between XSS and CSRF
XSS (Cross-Site Scripting) attacks exploit vulnerabilities in web applications to inject malicious scripts, targeting users by executing unauthorized code in their browsers. CSRF (Cross-Site Request Forgery) tricks authenticated users into submitting unintended requests, exploiting the trust between the user's browser and the web application. The key difference lies in XSS compromising client-side scripts, while CSRF abuses user authentication to perform actions without the user's consent.
Real-World Examples of XSS and CSRF
Real-world XSS attacks often target popular websites like Twitter and Facebook, where malicious scripts steal user credentials or spread worms within the platform. CSRF exploits have compromised banking applications such as PayPal and HSBC, tricking users into unknowingly performing unauthorized fund transfers. These examples emphasize the critical need for effective input validation and anti-CSRF tokens in web security.
Detection Techniques for XSS and CSRF
XSS detection techniques primarily involve input validation, employing Content Security Policy (CSP), and using automated tools like web vulnerability scanners to identify malicious script injections. CSRF detection relies on verifying anti-CSRF tokens embedded in web requests and monitoring anomalous user behavior or request patterns. Both attack types benefit from runtime application self-protection (RASP) solutions that analyze and block suspicious interactions in real-time.
Prevention Strategies: XSS vs CSRF
Effective XSS prevention strategies include input validation, output encoding, and implementing Content Security Policy (CSP) to mitigate script injection risks. CSRF prevention relies heavily on generating unique anti-CSRF tokens for each user session and validating these tokens on sensitive requests to ensure authenticity. Combining these measures strengthens the overall security posture by addressing both client-side script exploits and unauthorized request forgeries.
Impact of XSS and CSRF on User Data Security
Cross-Site Scripting (XSS) targets the injection of malicious scripts into trusted websites, enabling attackers to steal sensitive user data such as cookies and session tokens, potentially leading to identity theft and unauthorized account access. Cross-Site Request Forgery (CSRF) exploits authenticated users' sessions to perform unwanted actions without their consent, compromising user data integrity and leading to unauthorized transactions or data manipulation. Both XSS and CSRF significantly threaten user data security by enabling attackers to bypass authentication mechanisms and manipulate sensitive information.
Best Practices for Mitigating XSS and CSRF Risks
Implementing Content Security Policy (CSP) and sanitizing user inputs are critical best practices for mitigating XSS risks by restricting execution of malicious scripts. To defend against CSRF, deploying anti-CSRF tokens and enforcing SameSite cookie attributes effectively prevent unauthorized state-changing requests. Regular security testing and adhering to secure development frameworks further strengthen protection against both XSS and CSRF vulnerabilities.
XSS vs CSRF Infographic
 difterm.com
difterm.com