Vulnerability scanning identifies security weaknesses in systems and applications by regularly assessing for potential threats and exposures. Patch management involves applying updates and fixes to software to remediate these vulnerabilities, ensuring systems remain protected against cyberattacks. Combining continuous vulnerability scanning with timely patch management is essential for maintaining robust security in any IT environment.
Table of Comparison
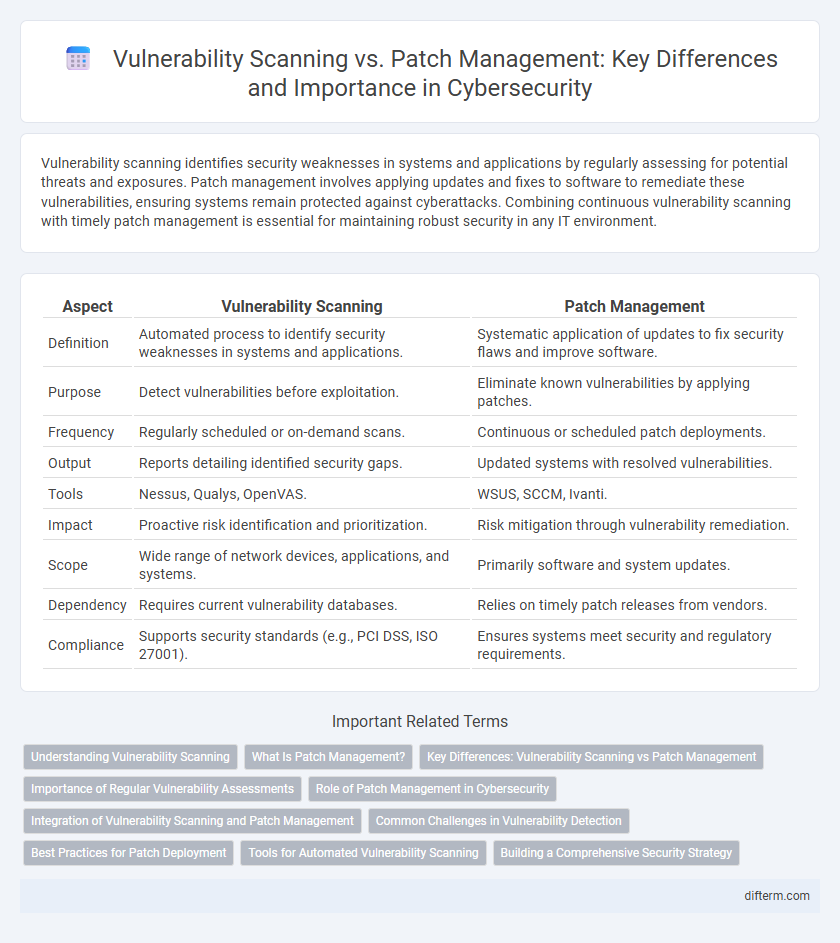
| Aspect | Vulnerability Scanning | Patch Management |
|---|---|---|
| Definition | Automated process to identify security weaknesses in systems and applications. | Systematic application of updates to fix security flaws and improve software. |
| Purpose | Detect vulnerabilities before exploitation. | Eliminate known vulnerabilities by applying patches. |
| Frequency | Regularly scheduled or on-demand scans. | Continuous or scheduled patch deployments. |
| Output | Reports detailing identified security gaps. | Updated systems with resolved vulnerabilities. |
| Tools | Nessus, Qualys, OpenVAS. | WSUS, SCCM, Ivanti. |
| Impact | Proactive risk identification and prioritization. | Risk mitigation through vulnerability remediation. |
| Scope | Wide range of network devices, applications, and systems. | Primarily software and system updates. |
| Dependency | Requires current vulnerability databases. | Relies on timely patch releases from vendors. |
| Compliance | Supports security standards (e.g., PCI DSS, ISO 27001). | Ensures systems meet security and regulatory requirements. |
Understanding Vulnerability Scanning
Vulnerability scanning is a proactive security measure that identifies weaknesses in network systems, applications, and devices by detecting missing patches, misconfigurations, and outdated software versions. It leverages automated tools to systematically examine IT environments, providing real-time insights into potential entry points for cyber attackers. Effective vulnerability scanning supports timely risk assessment and prioritizes remediation efforts, forming a critical first step before implementing patch management strategies.
What Is Patch Management?
Patch management is the process of identifying, acquiring, testing, and installing software updates or patches on computer systems to fix vulnerabilities, improve functionality, and enhance security. It involves systematically applying patches to operating systems, applications, and firmware to prevent exploitation by cyber threats. Effective patch management reduces the risk of security breaches by addressing known vulnerabilities before attackers can exploit them.
Key Differences: Vulnerability Scanning vs Patch Management
Vulnerability scanning identifies and assesses security weaknesses within systems by detecting outdated software, misconfigurations, and exploitable vulnerabilities. Patch management focuses on the systematic process of acquiring, testing, and deploying software updates to remediate identified security flaws and improve system stability. While vulnerability scanning provides insight into potential risks, patch management enforces the correction of these vulnerabilities to maintain a secure environment.
Importance of Regular Vulnerability Assessments
Regular vulnerability assessments are essential for identifying security weaknesses before attackers can exploit them, enabling proactive risk mitigation and stronger defense postures. While patch management addresses known vulnerabilities by applying updates, continuous scanning uncovers emerging threats and zero-day vulnerabilities that patches may not yet cover. Integrating frequent vulnerability scans into security protocols ensures timely detection and prioritization of remediation efforts, reducing the attack surface effectively.
Role of Patch Management in Cybersecurity
Patch management plays a critical role in cybersecurity by systematically identifying, acquiring, testing, and deploying software updates to remediate security vulnerabilities that could be exploited by attackers. It reduces the risk of data breaches, malware infections, and system downtime by ensuring that all applications and operating systems remain up to date with the latest security patches. Effective patch management complements vulnerability scanning by not only detecting weaknesses but also resolving them promptly to maintain a strong security posture.
Integration of Vulnerability Scanning and Patch Management
Integrating vulnerability scanning with patch management accelerates the identification and remediation of security risks by providing real-time insights into system weaknesses and corresponding patch requirements. This synergy enables organizations to prioritize critical vulnerabilities based on exposure and exploitability, ensuring timely deployment of security patches. Seamless integration reduces the attack surface, enhances compliance with regulatory standards, and improves overall vulnerability management efficiency.
Common Challenges in Vulnerability Detection
Vulnerability scanning often struggles with false positives and incomplete coverage, leading to gaps in identifying critical security flaws. Patch management faces challenges in timely deployment due to testing requirements and compatibility issues, which can delay remediation and prolong exposure to threats. Both processes require continuous updating and integration with asset management systems to ensure comprehensive vulnerability detection and effective risk mitigation.
Best Practices for Patch Deployment
Effective patch deployment relies on a systematic vulnerability scanning process to identify security gaps and prioritize patches based on risk severity. Best practices include timely application of patches, verifying compatibility to prevent system disruptions, and maintaining comprehensive documentation for compliance audits. Continuous monitoring and automated patch management tools enhance accuracy and reduce the window of exposure to potential threats.
Tools for Automated Vulnerability Scanning
Automated vulnerability scanning tools, such as Nessus, Qualys, and Rapid7 Nexpose, provide continuous assessment of network devices, applications, and systems to identify security weaknesses before they can be exploited. These tools leverage extensive vulnerability databases and real-time threat intelligence to detect misconfigurations, outdated software, and potential entry points for attackers. Integrating automated scanners with patch management solutions streamlines remediation efforts by prioritizing vulnerabilities and enabling timely deployment of security updates.
Building a Comprehensive Security Strategy
Vulnerability scanning identifies security weaknesses by systematically examining systems, networks, and applications to detect potential threats before attackers exploit them. Patch management complements this process by ensuring timely deployment of software updates that fix identified vulnerabilities and enhance system defenses. Combining continuous vulnerability scanning with proactive patch management forms a robust, comprehensive security strategy that minimizes risk exposure and strengthens organizational resilience against cyberattacks.
Vulnerability Scanning vs Patch Management Infographic
 difterm.com
difterm.com