Application firewalls protect specific software applications by filtering incoming and outgoing traffic based on predefined rules, offering granular control over user actions and data access. Network firewalls, on the other hand, monitor and control traffic between different networks to prevent unauthorized access, acting as a barrier at the perimeter level. Choosing between them depends on whether protection is needed at the application layer or the broader network infrastructure for enhanced security in pet-related systems.
Table of Comparison
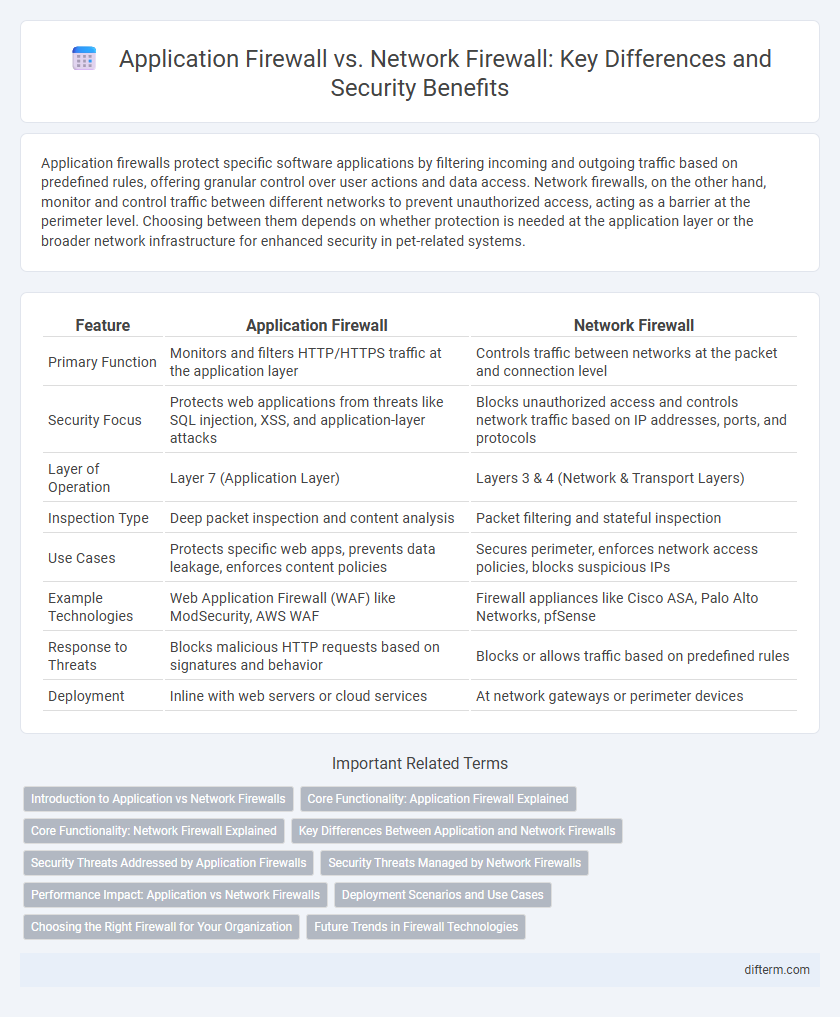
| Feature | Application Firewall | Network Firewall |
|---|---|---|
| Primary Function | Monitors and filters HTTP/HTTPS traffic at the application layer | Controls traffic between networks at the packet and connection level |
| Security Focus | Protects web applications from threats like SQL injection, XSS, and application-layer attacks | Blocks unauthorized access and controls network traffic based on IP addresses, ports, and protocols |
| Layer of Operation | Layer 7 (Application Layer) | Layers 3 & 4 (Network & Transport Layers) |
| Inspection Type | Deep packet inspection and content analysis | Packet filtering and stateful inspection |
| Use Cases | Protects specific web apps, prevents data leakage, enforces content policies | Secures perimeter, enforces network access policies, blocks suspicious IPs |
| Example Technologies | Web Application Firewall (WAF) like ModSecurity, AWS WAF | Firewall appliances like Cisco ASA, Palo Alto Networks, pfSense |
| Response to Threats | Blocks malicious HTTP requests based on signatures and behavior | Blocks or allows traffic based on predefined rules |
| Deployment | Inline with web servers or cloud services | At network gateways or perimeter devices |
Introduction to Application vs Network Firewalls
Application firewalls filter traffic to and from specific applications, providing deep packet inspection and controlling application-layer protocols like HTTP and FTP. Network firewalls operate at the network perimeter, monitoring and blocking traffic based on IP addresses, ports, and protocols, ensuring broad protection across the entire network. Both firewalls complement each other by addressing different layers of the OSI model and enhancing overall network security.
Core Functionality: Application Firewall Explained
Application firewalls operate at the application layer (Layer 7) of the OSI model, inspecting and filtering incoming and outgoing traffic based on specific application data and protocols like HTTP and FTP. They provide granular control by analyzing user requests, blocking threats such as SQL injection, cross-site scripting, and other web application attacks. Unlike network firewalls that focus on packet filtering and IP addresses, application firewalls enable deep packet inspection to protect web applications from sophisticated attacks targeting vulnerabilities within application logic.
Core Functionality: Network Firewall Explained
A network firewall serves as a crucial barrier that monitors and controls incoming and outgoing network traffic based on predetermined security rules, effectively protecting the entire network from unauthorized access and cyber threats. Unlike application firewalls that filter specific application-level traffic, network firewalls operate at the packet level, inspecting IP addresses, ports, and protocols to enforce security policies across all devices within a network segment. This core functionality enables network firewalls to prevent attacks such as unauthorized intrusions, malware transmission, and denial-of-service attempts by filtering traffic at the perimeter or within internal segments.
Key Differences Between Application and Network Firewalls
Application firewalls filter traffic based on specific application-level protocols and data, providing granular control by monitoring HTTP, FTP, SMTP, and other protocol exchanges, while network firewalls operate at the packet level, focusing on IP addresses, ports, and protocols to block or allow traffic. Application firewalls offer deeper inspection to detect and prevent threats like SQL injection and cross-site scripting, which network firewalls typically cannot identify. Network firewalls are generally faster and handle high traffic volumes efficiently, whereas application firewalls provide enhanced security for web applications by understanding the context of the data being transmitted.
Security Threats Addressed by Application Firewalls
Application firewalls specifically address security threats such as injection attacks, cross-site scripting (XSS), and unauthorized API access by filtering and monitoring HTTP/HTTPS traffic at the application layer. Unlike network firewalls that primarily block port-level attacks and unauthorized IP traffic, application firewalls provide granular control over user inputs and application behavior, preventing exploitation of web vulnerabilities. They are essential for protecting web applications from sophisticated attacks targeting business logic and sensitive data.
Security Threats Managed by Network Firewalls
Network firewalls primarily manage security threats such as unauthorized access, packet filtering, and intrusion prevention by inspecting traffic at the IP and transport layers. They effectively block IP spoofing, denial-of-service (DoS) attacks, and port scanning attempts, ensuring robust perimeter defense. Network firewalls enforce security policies by controlling traffic flow between different networks, reducing exposure to external cyber threats.
Performance Impact: Application vs Network Firewalls
Application firewalls inspect traffic at the application layer, providing granular control but potentially introducing higher latency due to deep packet inspection and protocol analysis. Network firewalls operate at the network or transport layers, offering faster performance with less detailed inspection, which can result in lower latency and higher throughput. The choice between the two impacts overall system performance, with application firewalls prioritizing security granularity and network firewalls optimizing speed and resource efficiency.
Deployment Scenarios and Use Cases
Application firewalls operate at the application layer, filtering and monitoring traffic to prevent attacks like SQL injection and cross-site scripting, making them ideal for protecting web applications and APIs. Network firewalls function at the network layer, controlling incoming and outgoing traffic based on IP addresses, ports, and protocols, which suits perimeter security and traffic segmentation in enterprise networks. Deployment scenarios often pair application firewalls with network firewalls to provide layered security, where network firewalls handle broad traffic control and application firewalls enforce granular application-specific protections.
Choosing the Right Firewall for Your Organization
Selecting the right firewall depends on your organization's security needs: application firewalls provide deep packet inspection and protection against application-layer attacks, ideal for securing web applications and APIs. Network firewalls focus on controlling traffic based on IP addresses and ports, offering robust perimeter defense against unauthorized access attempts. Assessing factors like traffic types, compliance requirements, and desired granularity is essential for optimizing your security infrastructure.
Future Trends in Firewall Technologies
Next-generation firewall technologies integrate AI-driven threat detection and automated response capabilities to enhance protection beyond traditional boundaries. Application firewalls increasingly leverage machine learning to identify and block sophisticated zero-day attacks targeting specific applications, while network firewalls adopt deeper packet inspection and behavior analysis to monitor complex network traffic patterns. The convergence of cloud-native firewall services with edge computing ensures scalable, adaptive security frameworks designed for hybrid and multi-cloud environments in the future.
Application Firewall vs Network Firewall Infographic
 difterm.com
difterm.com