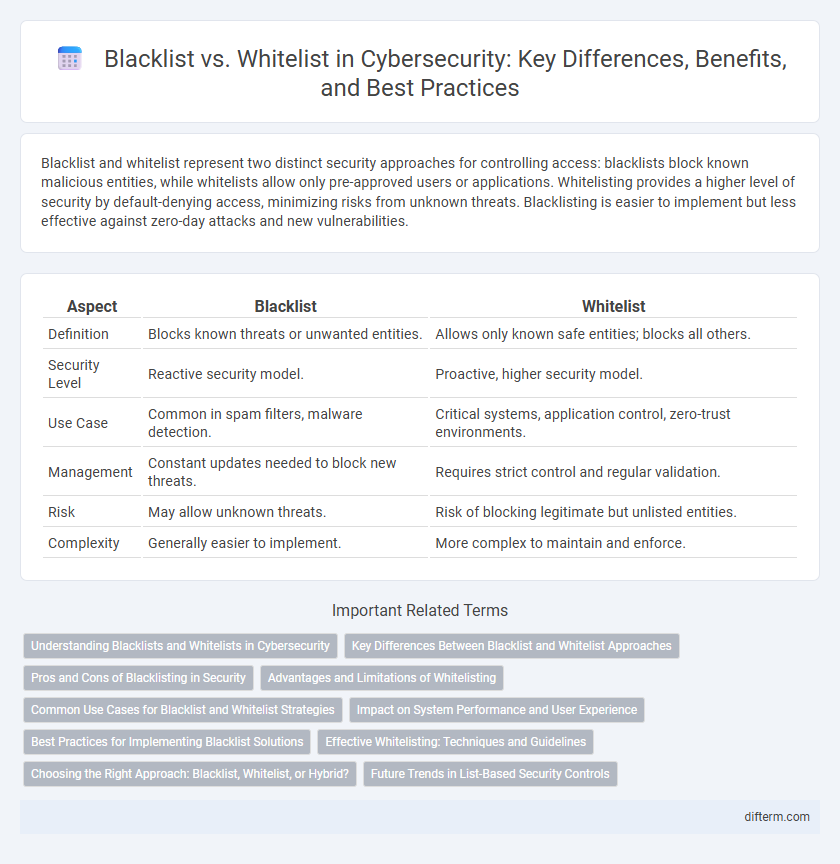
Blacklist and whitelist represent two distinct security approaches for controlling access: blacklists block known malicious entities, while whitelists allow only pre-approved users or applications. Whitelisting provides a higher level of security by default-denying access, minimizing risks from unknown threats. Blacklisting is easier to implement but less effective against zero-day attacks and new vulnerabilities.
Table of Comparison
| Aspect | Blacklist | Whitelist |
|---|---|---|
| Definition | Blocks known threats or unwanted entities. | Allows only known safe entities; blocks all others. |
| Security Level | Reactive security model. | Proactive, higher security model. |
| Use Case | Common in spam filters, malware detection. | Critical systems, application control, zero-trust environments. |
| Management | Constant updates needed to block new threats. | Requires strict control and regular validation. |
| Risk | May allow unknown threats. | Risk of blocking legitimate but unlisted entities. |
| Complexity | Generally easier to implement. | More complex to maintain and enforce. |
Understanding Blacklists and Whitelists in Cybersecurity
Blacklists and whitelists serve as fundamental security tools by controlling access to systems and networks through predefined lists of entities. Blacklists block known malicious IP addresses, domains, or applications, preventing them from causing harm, while whitelists permit only approved, trusted entities, minimizing the attack surface by restricting everything else. Organizations enhance cybersecurity posture by combining both methods to effectively manage threats and ensure safe access to digital resources.
Key Differences Between Blacklist and Whitelist Approaches
Blacklist approaches block access to known malicious entities based on a predefined list, allowing all other traffic by default, which can leave systems vulnerable to new threats. Whitelist approaches permit only pre-approved entities, providing tighter security by default-deny but requiring continuous updates and management to avoid hindering legitimate users. The key difference lies in their default trust model: blacklist assumes everything is safe unless proven dangerous, whereas whitelist assumes everything is unsafe unless explicitly allowed.
Pros and Cons of Blacklisting in Security
Blacklisting in security allows organizations to block known malicious IP addresses, domains, or applications, providing a straightforward way to prevent known threats. However, it struggles with zero-day exploits and unknown threats, as it relies on previously identified risks, potentially allowing some malicious activities to bypass detection. Maintaining and updating blacklists can be resource-intensive, often leading to gaps in protection due to incomplete or outdated threat intelligence.
Advantages and Limitations of Whitelisting
Whitelisting enhances security by allowing only pre-approved applications or IP addresses to access systems, significantly reducing the attack surface and blocking unauthorized access attempts. Its main advantage lies in preventing zero-day exploits and unknown threats by restricting execution to trusted software, improving overall network integrity. However, whitelisting can be resource-intensive to maintain, potentially leading to operational delays and hindering legitimate users if the list is not regularly updated or managed effectively.
Common Use Cases for Blacklist and Whitelist Strategies
Blacklist strategies are commonly used in email filtering to block known spam addresses and malware sources, enhancing network protection by explicitly denying access to harmful entities. Whitelist strategies are preferred in high-security environments like corporate networks and financial institutions, allowing only pre-approved users, software, or IP addresses to access sensitive systems, which minimizes risks from unknown threats. Combining both approaches often improves overall security posture by blocking known threats while ensuring reliable access for trusted entities.
Impact on System Performance and User Experience
Blacklist filtering can degrade system performance by continually scanning and blocking known malicious entities, leading to slower response times and increased resource consumption. Whitelist approaches enhance user experience by allowing only pre-approved, trusted applications or users, minimizing false positives and reducing latency. However, strict whitelisting may limit flexibility and require substantial administrative effort to maintain accuracy.
Best Practices for Implementing Blacklist Solutions
Effective blacklist implementation requires regularly updating threat databases to block known malicious IPs, domains, and applications, enhancing network security. Employ dynamic blacklists that integrate real-time threat intelligence feeds to adapt to emerging cyber threats rapidly. Combine blacklist solutions with anomaly detection systems to minimize false positives while maintaining robust protection against known vulnerabilities.
Effective Whitelisting: Techniques and Guidelines
Effective whitelisting involves creating a precise list of approved applications, IP addresses, or users to prevent unauthorized access and enhance security posture. Techniques include regularly updating the whitelist to accommodate legitimate changes, using automated tools for real-time monitoring and instant threat detection, and enforcing strict access controls based on least privilege principles. Implementing multi-factor authentication alongside whitelisting further strengthens protection against cyber threats and reduces false positives.
Choosing the Right Approach: Blacklist, Whitelist, or Hybrid?
Choosing between blacklist, whitelist, or hybrid security approaches depends on the specific threat landscape and organizational needs. Blacklists block identified malicious IPs or domains, offering broad but reactive protection, while whitelists allow only pre-approved entities, providing strict access control at the cost of flexibility. Hybrid models combine both methods to balance security and usability, enabling dynamic threat response alongside trusted entity validation.
Future Trends in List-Based Security Controls
Future trends in list-based security controls emphasize dynamic and adaptive blacklists and whitelists powered by AI and machine learning, enabling real-time threat detection and response. Integration with cloud-native security platforms enhances scalability and automation, reducing false positives and improving threat intelligence accuracy. Emerging approaches prioritize behavior-based analytics and continuous validation to evolve beyond static list management, addressing increasingly sophisticated cyber threats effectively.
Blacklist vs Whitelist Infographic
 difterm.com
difterm.com