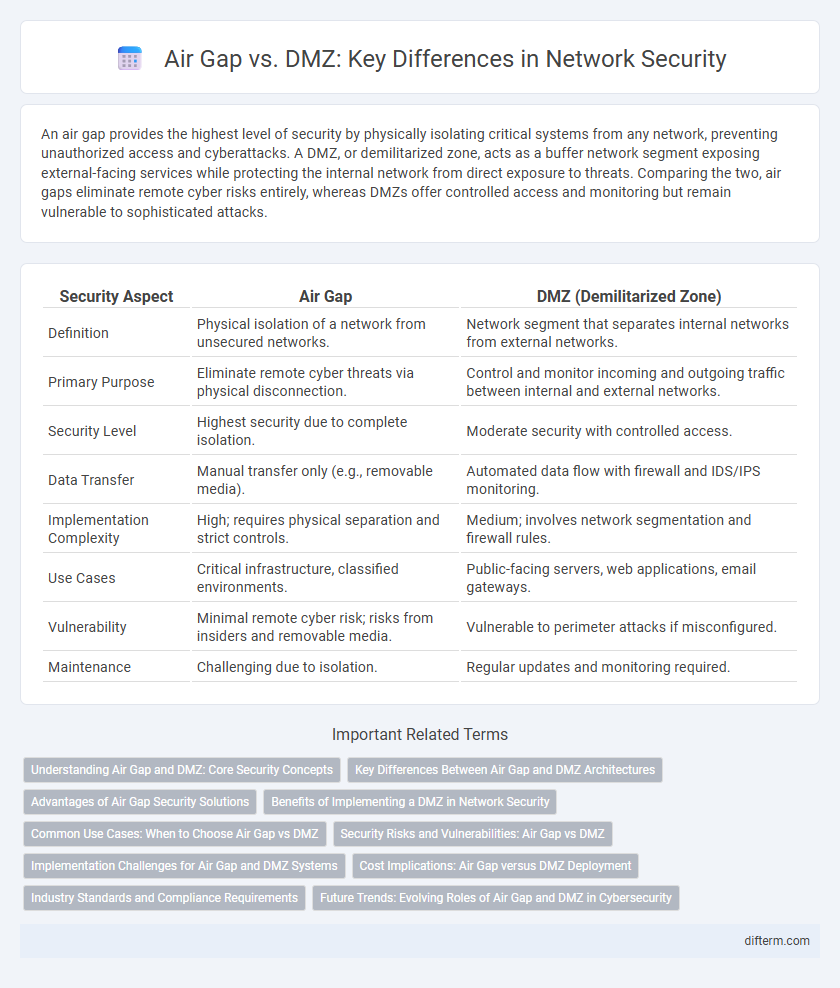
An air gap provides the highest level of security by physically isolating critical systems from any network, preventing unauthorized access and cyberattacks. A DMZ, or demilitarized zone, acts as a buffer network segment exposing external-facing services while protecting the internal network from direct exposure to threats. Comparing the two, air gaps eliminate remote cyber risks entirely, whereas DMZs offer controlled access and monitoring but remain vulnerable to sophisticated attacks.
Table of Comparison
| Security Aspect | Air Gap | DMZ (Demilitarized Zone) |
|---|---|---|
| Definition | Physical isolation of a network from unsecured networks. | Network segment that separates internal networks from external networks. |
| Primary Purpose | Eliminate remote cyber threats via physical disconnection. | Control and monitor incoming and outgoing traffic between internal and external networks. |
| Security Level | Highest security due to complete isolation. | Moderate security with controlled access. |
| Data Transfer | Manual transfer only (e.g., removable media). | Automated data flow with firewall and IDS/IPS monitoring. |
| Implementation Complexity | High; requires physical separation and strict controls. | Medium; involves network segmentation and firewall rules. |
| Use Cases | Critical infrastructure, classified environments. | Public-facing servers, web applications, email gateways. |
| Vulnerability | Minimal remote cyber risk; risks from insiders and removable media. | Vulnerable to perimeter attacks if misconfigured. |
| Maintenance | Challenging due to isolation. | Regular updates and monitoring required. |
Understanding Air Gap and DMZ: Core Security Concepts
Air gap security involves physically isolating critical systems from unsecured networks to eliminate external threats, ensuring no direct or indirect electronic connection exists. In contrast, a DMZ (demilitarized zone) creates a segmented network zone between an internal trusted network and untrusted external networks, allowing controlled access while minimizing risk exposure. Understanding these core concepts is crucial for designing layered security architectures that balance protection with operational connectivity.
Key Differences Between Air Gap and DMZ Architectures
Air Gap architecture physically isolates critical systems from unsecured networks, preventing any direct electronic communication, thereby eliminating remote cyber threats. DMZ (Demilitarized Zone) architecture creates a secure network segment between an internal network and external sources, allowing controlled access and monitoring through firewalls and intrusion detection systems. The key difference lies in Air Gap's total disconnection ensuring maximum security versus DMZ's controlled connectivity balancing accessibility with risk mitigation.
Advantages of Air Gap Security Solutions
Air gap security solutions provide unparalleled protection by physically isolating critical systems from unsecured networks, eliminating the risk of remote cyber attacks and unauthorized access. This isolation ensures sensitive data and infrastructure remain impervious to malware, ransomware, and network-based exploits. Air gaps are especially advantageous in high-security environments like military, industrial control systems, and financial institutions where preventing data breaches is paramount.
Benefits of Implementing a DMZ in Network Security
Implementing a DMZ in network security enhances protection by isolating public-facing services from the internal network, reducing the risk of unauthorized access. It provides controlled traffic filtering with firewall configurations, enabling safer interaction between external users and sensitive internal systems. The DMZ supports monitoring and logging of suspicious activity, facilitating rapid response to potential threats while maintaining operational continuity.
Common Use Cases: When to Choose Air Gap vs DMZ
Air Gap is ideal for isolating highly sensitive systems, such as critical infrastructure and classified government data networks, where zero connectivity is essential to prevent cyber threats. DMZ (Demilitarized Zone) is suitable for environments requiring controlled access to public-facing services, like web servers and email gateways, while protecting internal networks from external attacks. Organizations select Air Gap for maximum security without remote access, whereas DMZ balances accessibility and protection for external communication.
Security Risks and Vulnerabilities: Air Gap vs DMZ
Air Gap security minimizes vulnerabilities by physically isolating critical systems from external networks, drastically reducing exposure to cyber threats such as malware and remote exploits. DMZ architectures, while providing controlled access zones between internal networks and untrusted external sources, introduce risks including misconfiguration and potential lateral movement by attackers once the perimeter is breached. Effective risk mitigation requires continuous monitoring and strict access controls tailored to the specific exposure profiles of Air Gaps and DMZ environments.
Implementation Challenges for Air Gap and DMZ Systems
Implementing air gap systems presents challenges such as ensuring strict physical isolation to prevent data leakage while maintaining operational efficiency, often requiring specialized hardware and rigorous procedural controls. DMZ setups face complexities in configuring firewalls and access controls correctly to balance security and functionality, with risks arising from misconfigurations that could expose internal networks to external threats. Both approaches demand continuous monitoring and regular audits to address vulnerabilities unique to their architecture and deployment environments.
Cost Implications: Air Gap versus DMZ Deployment
Air gap implementation entails higher initial costs due to dedicated hardware and physical isolation requirements, increasing expenses for maintenance and specialized personnel. DMZ deployment offers a more cost-effective solution by leveraging existing network infrastructure, but incurs ongoing expenses related to firewall management and continuous monitoring. Budget considerations should weigh the substantial upfront investment of air gaps against the operational costs and risk exposure associated with DMZ configurations.
Industry Standards and Compliance Requirements
Air gap architecture ensures maximum security by physically isolating critical systems from external networks, aligning with stringent industry standards such as NIST SP 800-53 and IEC 62443 for high-assurance environments. DMZ (Demilitarized Zone) implementations adhere to common compliance frameworks like PCI DSS and HIPAA by segmenting network zones to limit access and monitor threats while allowing controlled connectivity. Both strategies meet regulatory requirements for data protection and risk management, with air gaps favored in industrial control systems and DMZs prevalent in enterprise IT infrastructures.
Future Trends: Evolving Roles of Air Gap and DMZ in Cybersecurity
Emerging cybersecurity trends indicate increased integration of AI and machine learning within air gap and DMZ architectures to proactively detect threats and enhance network segmentation. Air gaps continue to serve critical roles in protecting highly sensitive systems by physically isolating them from unsecured networks, while DMZs are evolving to support cloud workloads and zero-trust frameworks, improving controlled access and threat containment. The convergence of these technologies alongside advancements in behavioral analytics and automated response mechanisms is shaping future security models that emphasize adaptive defense and minimized attack surfaces.
Air Gap vs DMZ Infographic
 difterm.com
difterm.com