Risk analysis involves identifying and evaluating potential threats and vulnerabilities to understand the likelihood and impact of security risks. Risk assessment builds on this by quantifying the identified risks and prioritizing them to guide decision-making and resource allocation. Both processes are essential for developing effective security strategies and mitigating potential damage.
Table of Comparison
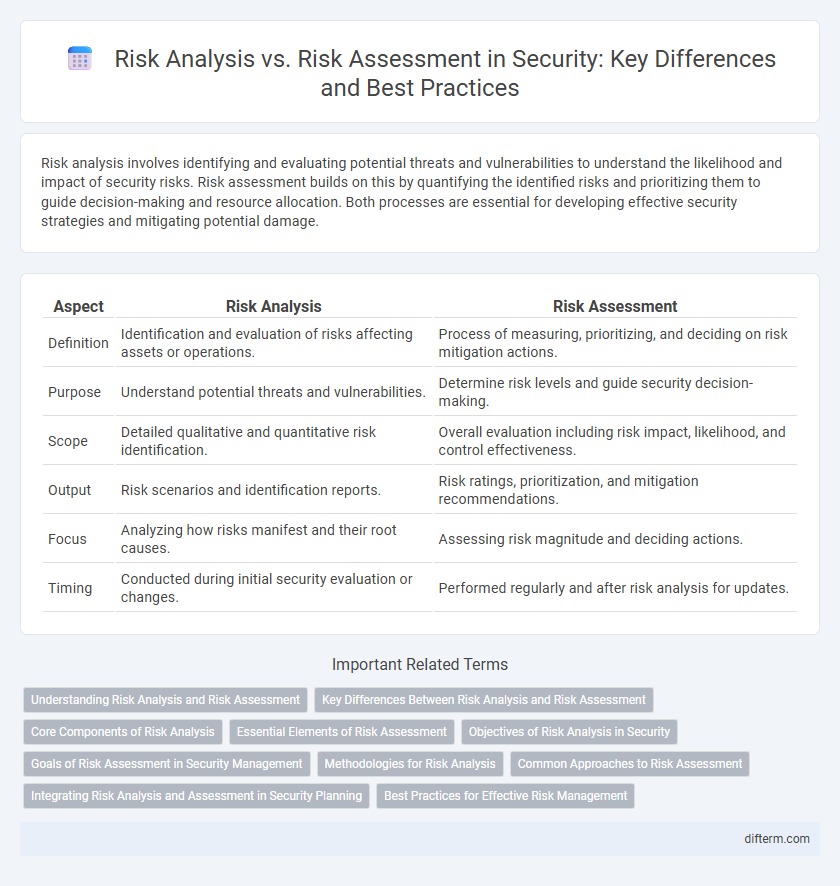
| Aspect | Risk Analysis | Risk Assessment |
|---|---|---|
| Definition | Identification and evaluation of risks affecting assets or operations. | Process of measuring, prioritizing, and deciding on risk mitigation actions. |
| Purpose | Understand potential threats and vulnerabilities. | Determine risk levels and guide security decision-making. |
| Scope | Detailed qualitative and quantitative risk identification. | Overall evaluation including risk impact, likelihood, and control effectiveness. |
| Output | Risk scenarios and identification reports. | Risk ratings, prioritization, and mitigation recommendations. |
| Focus | Analyzing how risks manifest and their root causes. | Assessing risk magnitude and deciding actions. |
| Timing | Conducted during initial security evaluation or changes. | Performed regularly and after risk analysis for updates. |
Understanding Risk Analysis and Risk Assessment
Risk analysis involves identifying, evaluating, and prioritizing potential threats to an organization's assets, focusing on understanding the likelihood and impact of risks. Risk assessment builds upon this by systematically measuring the risks and determining appropriate mitigation strategies to reduce vulnerabilities and enhance security posture. Both processes are essential in developing a comprehensive risk management framework that protects sensitive data and critical infrastructure.
Key Differences Between Risk Analysis and Risk Assessment
Risk analysis systematically identifies and evaluates potential threats, vulnerabilities, and their impacts to quantify risk levels, while risk assessment encompasses the entire process of identifying, analyzing, and prioritizing risks for mitigation. Risk analysis is data-driven, focusing on understanding and measuring risk factors, whereas risk assessment integrates risk analysis results with decision-making to formulate security strategies. The key differences lie in risk analysis being a subset focused on detailed evaluation, and risk assessment being a comprehensive approach that guides risk management actions.
Core Components of Risk Analysis
Risk analysis involves identifying potential threats, vulnerabilities, and the likelihood of adverse events impacting an organization's assets, emphasizing threat identification, vulnerability assessment, and impact evaluation as its core components. Risk assessment builds upon this analysis by quantitatively or qualitatively estimating risk levels to prioritize mitigation strategies effectively. Understanding these core components ensures comprehensive security planning and focused resource allocation to reduce organizational risk exposure.
Essential Elements of Risk Assessment
Risk assessment involves identifying, analyzing, and evaluating potential threats to an organization's assets, systems, or operations. Essential elements include asset identification, threat and vulnerability analysis, risk estimation, and prioritization based on impact and likelihood. This process supports decision-making to implement controls and mitigate risks effectively within a security framework.
Objectives of Risk Analysis in Security
Risk analysis in security aims to identify, evaluate, and prioritize potential threats and vulnerabilities affecting an organization's assets to determine the likelihood and impact of risks. It focuses on understanding the nature of risks to develop effective mitigation strategies and allocate resources efficiently. This process supports informed decision-making by providing a comprehensive view of security challenges and their potential consequences.
Goals of Risk Assessment in Security Management
Risk assessment aims to identify, evaluate, and prioritize security risks to protect organizational assets and ensure compliance with regulatory requirements. The process involves analyzing potential threats, vulnerabilities, and impacts to develop effective risk mitigation strategies. Clear risk assessment goals include minimizing harm, supporting informed decision-making, and enhancing overall security posture.
Methodologies for Risk Analysis
Risk analysis methodologies focus on identifying, quantifying, and prioritizing risks through techniques such as qualitative risk analysis, quantitative risk analysis, and semi-quantitative approaches. Common methods include Failure Mode and Effects Analysis (FMEA), Fault Tree Analysis (FTA), and scenario analysis, enabling systematic evaluation of potential threats and vulnerabilities. These methodologies provide detailed insights into risk probabilities and impacts, guiding effective risk mitigation strategies and resource allocation.
Common Approaches to Risk Assessment
Common approaches to risk assessment in security include qualitative, quantitative, and hybrid methods that identify, evaluate, and prioritize potential threats based on likelihood and impact. Qualitative assessments use expert judgment and categorical scales to analyze risks, while quantitative assessments apply numerical data and statistical models to measure risk levels precisely. Hybrid methods combine both approaches to provide a balanced view, ensuring comprehensive risk management strategies tailored to organizational needs.
Integrating Risk Analysis and Assessment in Security Planning
Integrating risk analysis and risk assessment in security planning enhances the identification, evaluation, and prioritization of potential threats, allowing organizations to strategically allocate resources for mitigation. Risk analysis provides a detailed examination of vulnerabilities, threat vectors, and potential impacts, while risk assessment quantifies these risks to support decision-making processes. Seamless integration of both processes ensures comprehensive risk management frameworks that bolster security posture and resilience against evolving cyber threats.
Best Practices for Effective Risk Management
Effective risk management requires a clear distinction between risk analysis and risk assessment, where risk analysis involves identifying potential threats and vulnerabilities, while risk assessment evaluates the likelihood and impact of these risks. Best practices emphasize comprehensive data collection, continuous monitoring, and integration of quantitative and qualitative methods to prioritize risks accurately. Implementing a structured framework, such as ISO 31000 or NIST SP 800-30, enhances decision-making and strengthens an organization's overall security posture.
Risk Analysis vs Risk Assessment Infographic
 difterm.com
difterm.com