Man-in-the-Middle (MitM) attacks intercept and alter communication between two parties without their knowledge, compromising data integrity and confidentiality. Replay attacks involve capturing valid data transmissions and retransmitting them to trick the recipient into unauthorized actions. Protecting pets' security systems from these threats requires robust encryption and authentication protocols to ensure message originality and prevent unauthorized access.
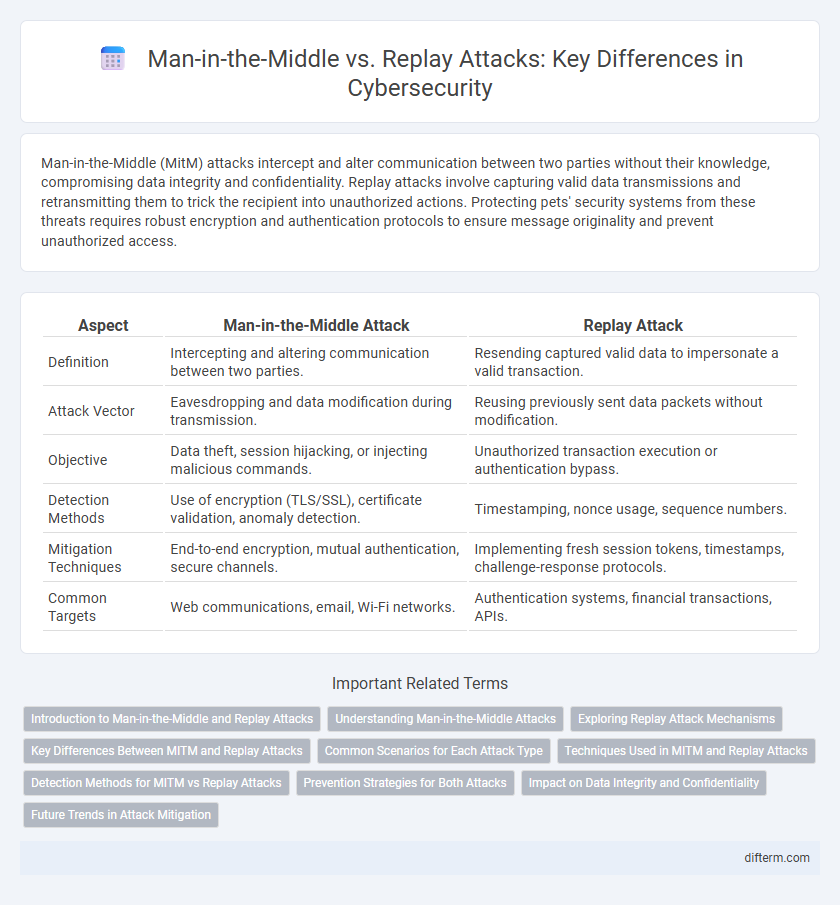
Table of Comparison
| Aspect | Man-in-the-Middle Attack | Replay Attack |
|---|---|---|
| Definition | Intercepting and altering communication between two parties. | Resending captured valid data to impersonate a valid transaction. |
| Attack Vector | Eavesdropping and data modification during transmission. | Reusing previously sent data packets without modification. |
| Objective | Data theft, session hijacking, or injecting malicious commands. | Unauthorized transaction execution or authentication bypass. |
| Detection Methods | Use of encryption (TLS/SSL), certificate validation, anomaly detection. | Timestamping, nonce usage, sequence numbers. |
| Mitigation Techniques | End-to-end encryption, mutual authentication, secure channels. | Implementing fresh session tokens, timestamps, challenge-response protocols. |
| Common Targets | Web communications, email, Wi-Fi networks. | Authentication systems, financial transactions, APIs. |
Introduction to Man-in-the-Middle and Replay Attacks
Man-in-the-Middle (MITM) attacks involve an adversary secretly intercepting and potentially altering communication between two parties without their knowledge. Replay attacks occur when an attacker captures and retransmits valid data transmissions to deceive the receiver or gain unauthorized access. Understanding these attack vectors is crucial for implementing robust security measures such as encryption, authentication, and session validation.
Understanding Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks involve an attacker secretly intercepting and potentially altering communication between two parties without their knowledge, compromising data confidentiality and integrity. These attacks exploit vulnerabilities in network protocols, such as unsecured Wi-Fi or weak encryption methods, enabling attackers to eavesdrop, steal credentials, or inject malicious content. Understanding MitM attacks is crucial for implementing strong encryption, authentication mechanisms, and secure communication channels to prevent unauthorized access and data breaches.
Exploring Replay Attack Mechanisms
Replay attacks exploit captured valid data transmissions to gain unauthorized access or manipulate systems, often by resending authentication messages or transaction requests. This attack mechanism targets vulnerabilities in session tokens, time stamps, or nonces, enabling adversaries to impersonate legitimate users without cracking encryption. Effective countermeasures include implementing robust timestamping, unique nonce values, and replay detection protocols within secure communication channels.
Key Differences Between MITM and Replay Attacks
Man-in-the-Middle (MITM) attacks involve an intruder intercepting and altering communication between two parties, enabling data manipulation in real-time, whereas Replay Attacks consist of capturing and retransmitting valid data to deceive a system without modification. MITM attacks target the confidentiality and integrity of ongoing communications, often exploiting cryptographic weaknesses, while Replay Attacks primarily compromise authentication by reusing legitimate transmission to gain unauthorized access. Key differences include the active manipulation and real-time interference characteristic of MITM versus the passive recording and delayed retransmission inherent in Replay Attacks.
Common Scenarios for Each Attack Type
Man-in-the-Middle attacks commonly occur in public Wi-Fi networks, where attackers intercept communications between users and websites to steal sensitive information like login credentials and financial data. Replay attacks typically arise in authentication systems and wireless networks, where attackers capture valid data transmissions and resend them to gain unauthorized access or disrupt operations. Both attack types exploit communication channels but differ in their methods: interception and alteration for Man-in-the-Middle, and duplication of valid messages for Replay attacks.
Techniques Used in MITM and Replay Attacks
Man-in-the-Middle (MITM) attacks employ techniques such as eavesdropping, session hijacking, and packet injection to intercept and alter communications between two parties without their knowledge. Replay attacks leverage the capture and retransmission of valid data transmissions, exploiting authentication tokens or session credentials to gain unauthorized access. Both attack methods exploit weaknesses in encryption, authentication protocols, and session management to compromise data integrity and confidentiality in network communications.
Detection Methods for MITM vs Replay Attacks
Detection methods for Man-in-the-Middle (MITM) attacks include continuous monitoring of SSL/TLS certificate validity and analyzing network traffic for anomalies such as duplicated responses or unexpected packet modifications. Replay attack detection relies on timestamp verification, nonce usage, and sequence number tracking to identify and prevent retransmission of captured valid messages. Implementing mutual authentication protocols and cryptographic challenge-response mechanisms enhances early identification and mitigation of both MITM and replay threats.
Prevention Strategies for Both Attacks
Effective prevention strategies for Man-in-the-Middle attacks include implementing strong encryption protocols like TLS, using mutual authentication, and deploying intrusion detection systems to monitor suspicious activities. To prevent Replay Attacks, incorporating unique session tokens, timestamps, and nonces in communication ensures message freshness, while secure key management prevents unauthorized message retransmission. Combining multi-factor authentication with network segmentation further enhances security against both attack vectors.
Impact on Data Integrity and Confidentiality
Man-in-the-Middle (MitM) attacks directly compromise data integrity and confidentiality by intercepting and potentially altering communications between two parties in real-time, leading to unauthorized data manipulation and exposure. Replay attacks primarily threaten data integrity by resending valid data transmissions without alteration, which can result in unauthorized actions or access without modifying the original content. MitM attacks pose a higher risk to confidentiality due to their active interception nature, while replay attacks mainly disrupt integrity through the misuse of legitimate, previously captured data.
Future Trends in Attack Mitigation
Emerging security frameworks are integrating machine learning algorithms to detect anomalies indicative of Man-in-the-Middle and Replay Attacks in real-time, enhancing response accuracy. Blockchain-based authentication mechanisms are gaining traction to prevent data tampering and ensure transaction integrity against these threats. Quantum encryption technologies are being researched to provide robust future-proof defense layers, significantly reducing the risk of interception and replay in communication channels.
Man-in-the-Middle vs Replay Attack Infographic
 difterm.com
difterm.com