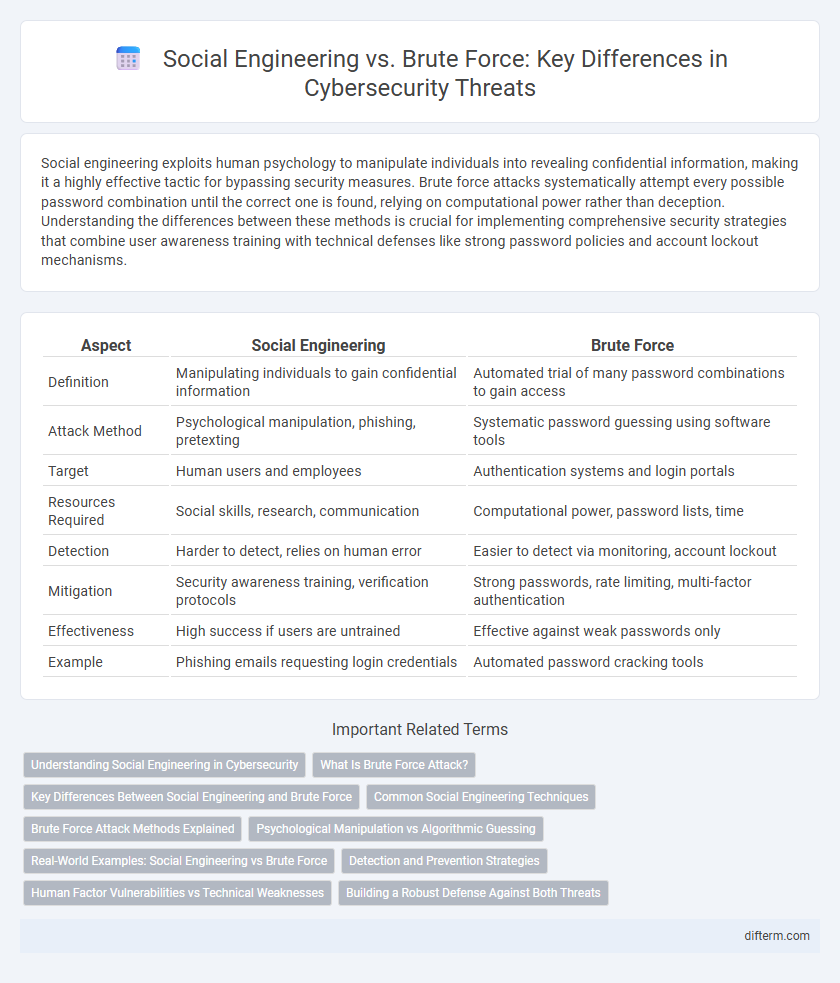
Social engineering exploits human psychology to manipulate individuals into revealing confidential information, making it a highly effective tactic for bypassing security measures. Brute force attacks systematically attempt every possible password combination until the correct one is found, relying on computational power rather than deception. Understanding the differences between these methods is crucial for implementing comprehensive security strategies that combine user awareness training with technical defenses like strong password policies and account lockout mechanisms.
Table of Comparison
| Aspect | Social Engineering | Brute Force |
|---|---|---|
| Definition | Manipulating individuals to gain confidential information | Automated trial of many password combinations to gain access |
| Attack Method | Psychological manipulation, phishing, pretexting | Systematic password guessing using software tools |
| Target | Human users and employees | Authentication systems and login portals |
| Resources Required | Social skills, research, communication | Computational power, password lists, time |
| Detection | Harder to detect, relies on human error | Easier to detect via monitoring, account lockout |
| Mitigation | Security awareness training, verification protocols | Strong passwords, rate limiting, multi-factor authentication |
| Effectiveness | High success if users are untrained | Effective against weak passwords only |
| Example | Phishing emails requesting login credentials | Automated password cracking tools |
Understanding Social Engineering in Cybersecurity
Social engineering in cybersecurity exploits human psychology to manipulate individuals into divulging confidential information, bypassing technical security measures without direct hacking attempts. This method often targets employees through phishing, pretexting, or baiting to gain unauthorized access to sensitive data. Unlike brute force attacks that rely on systematic guessing of passwords, social engineering capitalizes on trust and human error, making it a highly effective and insidious threat vector.
What Is Brute Force Attack?
A brute force attack is a cybersecurity method where attackers systematically try all possible password combinations to gain unauthorized access to a system. This technique relies on computational power to crack passwords, bypassing traditional authentication safeguards. Unlike social engineering, which manipulates human behavior, brute force attacks target the technical vulnerabilities in password strength and encryption protocols.
Key Differences Between Social Engineering and Brute Force
Social engineering exploits human psychology by manipulating individuals into divulging confidential information, while brute force attacks rely on automated techniques to systematically guess passwords or encryption keys. Unlike brute force, which targets technical vulnerabilities through repetitive trial and error, social engineering leverages deception and trust to bypass security controls. Effective defense requires training employees to recognize social manipulation and implementing strong authentication methods to mitigate brute force risks.
Common Social Engineering Techniques
Phishing remains one of the most prevalent social engineering techniques, exploiting human trust by impersonating legitimate entities to steal sensitive information. Pretexting involves creating a fabricated scenario to manipulate victims into divulging confidential data or performing actions that compromise security. Tailgating exploits physical access controls by following authorized personnel into restricted areas without proper credentials.
Brute Force Attack Methods Explained
Brute force attack methods involve systematically attempting all possible password combinations until the correct one is found, exploiting weak or common credentials. Automated tools rapidly generate and test countless password variations, making attacks effective against systems lacking strong password policies or account lockouts. These attacks rely heavily on computational power and time, contrasting with social engineering tactics that manipulate human psychology.
Psychological Manipulation vs Algorithmic Guessing
Social engineering exploits psychological manipulation to deceive individuals into revealing sensitive information by targeting human trust and behavior patterns. In contrast, brute force attacks rely on algorithmic guessing, systematically trying all possible password combinations to gain unauthorized access. Understanding the distinction between human-centric social engineering and computational brute force methods is crucial for implementing comprehensive cybersecurity defenses.
Real-World Examples: Social Engineering vs Brute Force
Social engineering attacks exploit human psychology to gain unauthorized access, as seen in the 2016 Democratic National Committee email breach where phishing emails tricked staff into revealing credentials. Brute force attacks rely on automated algorithms to systematically guess passwords, exemplified by the 2012 LinkedIn breach where hackers cracked millions of weak passwords using dictionary attacks. Real-world examples highlight that social engineering often bypasses technical defenses by targeting user behavior, while brute force requires significant computational resources and is deterred by strong password policies.
Detection and Prevention Strategies
Social engineering attacks exploit human psychology to manipulate individuals into revealing sensitive information, requiring employee training and awareness programs as primary detection and prevention strategies. Brute force attacks rely on automated attempts to guess passwords, necessitating strong password policies, rate limiting, and multi-factor authentication to mitigate unauthorized access. Continuous monitoring of network traffic and anomaly detection systems enhance early identification of both attack types, reducing potential security breaches.
Human Factor Vulnerabilities vs Technical Weaknesses
Social engineering exploits human factor vulnerabilities by manipulating individuals into divulging sensitive information or performing actions that compromise security, often bypassing technical safeguards. In contrast, brute force attacks target technical weaknesses such as weak passwords or encryption by systematically trying all possible combinations to gain unauthorized access. Understanding the distinction highlights the need for comprehensive security measures that address both human behavior and technical defenses.
Building a Robust Defense Against Both Threats
Building a robust defense against social engineering and brute force attacks requires a multi-layered security strategy combining user education and advanced technical controls. Implementing strong password policies, multi-factor authentication (MFA), and continuous monitoring helps mitigate brute force risks, while regular phishing simulations and security awareness training reduce susceptibility to social engineering tactics. Integrating anomaly detection systems and enforcing strict access controls further strengthens the organization's resilience against these prevalent cyber threats.
Social Engineering vs Brute Force Infographic
 difterm.com
difterm.com