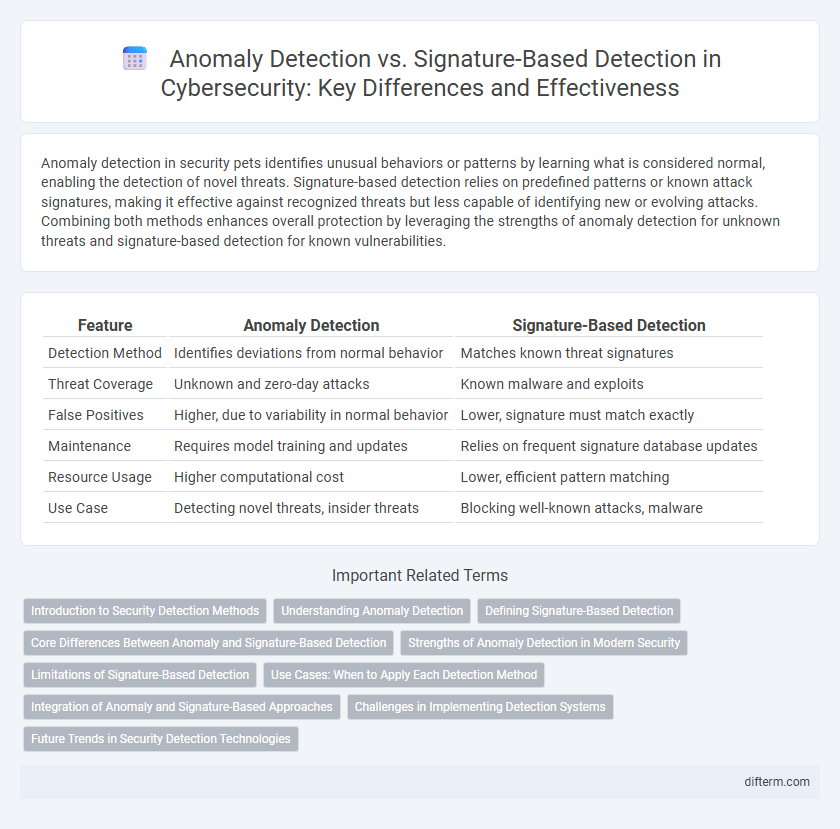
Anomaly detection in security pets identifies unusual behaviors or patterns by learning what is considered normal, enabling the detection of novel threats. Signature-based detection relies on predefined patterns or known attack signatures, making it effective against recognized threats but less capable of identifying new or evolving attacks. Combining both methods enhances overall protection by leveraging the strengths of anomaly detection for unknown threats and signature-based detection for known vulnerabilities.
Table of Comparison
| Feature | Anomaly Detection | Signature-Based Detection |
|---|---|---|
| Detection Method | Identifies deviations from normal behavior | Matches known threat signatures |
| Threat Coverage | Unknown and zero-day attacks | Known malware and exploits |
| False Positives | Higher, due to variability in normal behavior | Lower, signature must match exactly |
| Maintenance | Requires model training and updates | Relies on frequent signature database updates |
| Resource Usage | Higher computational cost | Lower, efficient pattern matching |
| Use Case | Detecting novel threats, insider threats | Blocking well-known attacks, malware |
Introduction to Security Detection Methods
Anomaly detection identifies deviations from established behavioral patterns, enabling the recognition of unknown threats by analyzing unusual activities in network traffic or user behavior. Signature-based detection relies on a predefined database of known threat signatures to quickly identify malware, viruses, or intrusions with high accuracy but limited adaptability to new attack variants. Both methods complement each other in security frameworks, with anomaly detection enhancing proactive threat discovery and signature-based detection offering precise identification of recognized malicious entities.
Understanding Anomaly Detection
Anomaly detection identifies unusual patterns or deviations from normal behavior within network traffic or system operations, enabling the detection of previously unknown threats. Unlike signature-based detection, which relies on a database of known malware fingerprints, anomaly detection uses machine learning algorithms and statistical models to recognize irregularities. This proactive approach enhances cybersecurity by uncovering zero-day attacks and insider threats that evade traditional signature methods.
Defining Signature-Based Detection
Signature-based detection relies on predefined patterns or known threat signatures stored in a database to identify malicious activities in cybersecurity systems. It efficiently detects previously identified threats by matching incoming data against these known signatures, enabling rapid response to recognized attacks. However, this method struggles with zero-day exploits or novel threats that do not have existing signatures in the database.
Core Differences Between Anomaly and Signature-Based Detection
Anomaly detection identifies deviations from established normal behavior patterns using machine learning and statistical models, enabling it to detect zero-day threats and unknown attacks. Signature-based detection relies on predefined patterns or signatures derived from known threats, offering high accuracy for recognized malware and exploits but failing against novel threats. Core differences include anomaly detection's adaptability and broader coverage versus signature-based detection's precision and dependence on updated threat databases.
Strengths of Anomaly Detection in Modern Security
Anomaly detection excels in identifying previously unknown threats by analyzing deviations from established behavior patterns, enabling early detection of zero-day attacks and insider threats. Its adaptive learning capabilities allow continuous monitoring and adjustment to evolving network activities, providing robust protection in dynamic environments. This approach reduces dependence on pre-existing threat databases, making it highly effective against sophisticated, polymorphic malware and novel attack vectors.
Limitations of Signature-Based Detection
Signature-based detection relies on known threat patterns, making it ineffective against zero-day exploits or polymorphic malware that frequently change their code structure. Its dependence on updated signature databases leads to delayed response times and potential gaps in protection. This approach struggles to identify novel or sophisticated attacks that do not match existing signatures.
Use Cases: When to Apply Each Detection Method
Anomaly detection excels in identifying unknown threats and zero-day attacks by analyzing deviations from normal behavior patterns in network traffic or user activity. Signature-based detection is most effective for quickly identifying known malware and vulnerabilities by matching against a database of previously identified threat signatures. Deploy anomaly detection in dynamic environments with evolving threats, while signature-based methods suit scenarios requiring fast, reliable detection of established attack vectors.
Integration of Anomaly and Signature-Based Approaches
Integrating anomaly detection with signature-based detection enhances security by combining the strengths of both methods to identify known and unknown threats. Anomaly detection monitors deviations from established behavioral baselines, while signature-based systems rely on predefined patterns of known attacks. This hybrid approach improves threat detection accuracy, reduces false positives, and provides comprehensive coverage against evolving cyber threats.
Challenges in Implementing Detection Systems
Anomaly detection systems face challenges such as high false-positive rates and the need for extensive training data to accurately model normal behavior, which complicates their deployment in dynamic environments. Signature-based detection struggles with identifying zero-day attacks and polymorphic malware due to its reliance on known threat signatures, limiting its effectiveness against novel threats. Both approaches demand continuous updates and tuning to maintain accuracy, creating resource-intensive and complex implementation processes for security teams.
Future Trends in Security Detection Technologies
Future trends in security detection technologies emphasize enhanced anomaly detection leveraging artificial intelligence and machine learning to identify novel threats by analyzing behavioral patterns rather than relying on predefined signatures. Signature-based detection remains essential for known malware and exploits, but its limitations drive the integration of hybrid models combining both methods for comprehensive threat visibility. Advances in real-time data analytics, cloud security, and adaptive algorithms are expected to improve detection accuracy and reduce false positives, making security systems more proactive and resilient against evolving cyberattacks.
Anomaly detection vs signature-based detection Infographic
 difterm.com
difterm.com