Non-repudiation ensures that a sender cannot deny the authenticity of their message, providing proof of origin and delivery in security communications. Integrity guarantees that the data remains unaltered from the time it was sent to the time it is received, preserving its accuracy and trustworthiness. Both concepts are critical for secure transactions, but non-repudiation emphasizes accountability while integrity focuses on preventing unauthorized data modification.
Table of Comparison
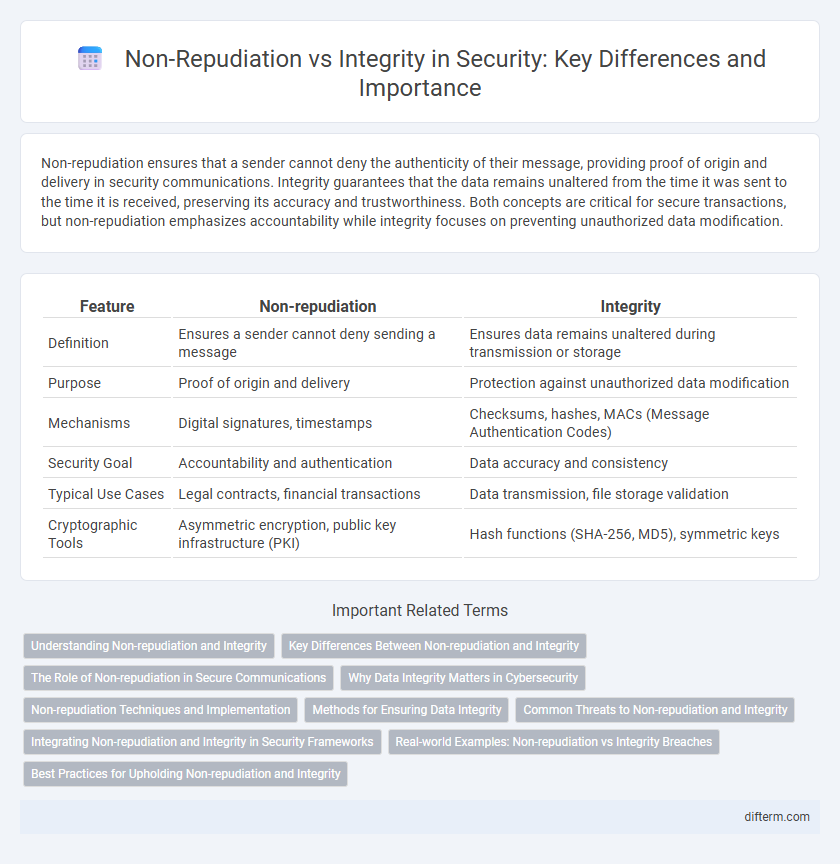
| Feature | Non-repudiation | Integrity |
|---|---|---|
| Definition | Ensures a sender cannot deny sending a message | Ensures data remains unaltered during transmission or storage |
| Purpose | Proof of origin and delivery | Protection against unauthorized data modification |
| Mechanisms | Digital signatures, timestamps | Checksums, hashes, MACs (Message Authentication Codes) |
| Security Goal | Accountability and authentication | Data accuracy and consistency |
| Typical Use Cases | Legal contracts, financial transactions | Data transmission, file storage validation |
| Cryptographic Tools | Asymmetric encryption, public key infrastructure (PKI) | Hash functions (SHA-256, MD5), symmetric keys |
Understanding Non-repudiation and Integrity
Non-repudiation ensures that a sender cannot deny the authenticity of their message, providing proof of origin and delivery. Integrity guarantees that data remains unaltered and accurate during transmission or storage, safeguarding against tampering and corruption. Understanding these concepts is crucial in designing secure communication systems that protect against fraud and unauthorized modifications.
Key Differences Between Non-repudiation and Integrity
Non-repudiation ensures that a sender cannot deny the authenticity of their signature on a document or a message they originated, typically enforced through digital signatures and audit trails. Integrity guarantees that data remains unaltered and intact from its source to destination, verified by mechanisms like cryptographic hash functions. While non-repudiation confirms the origin and commitment to information, integrity strictly protects against unauthorized data modification.
The Role of Non-repudiation in Secure Communications
Non-repudiation ensures that a sender cannot deny the authenticity of a transmitted message, providing verifiable proof that the message originated from a specific source. This security principle complements data integrity by guaranteeing that the message remains unaltered and confirming the sender's identity, crucial for legal and financial communications. In secure communications, non-repudiation protocols, such as digital signatures and timestamping, play a vital role in preventing fraud and establishing accountability.
Why Data Integrity Matters in Cybersecurity
Data integrity ensures that information remains accurate, consistent, and unaltered during storage or transmission, which is crucial for maintaining trust in cybersecurity systems. Non-repudiation guarantees that a party cannot deny the authenticity of their digital actions, while integrity focuses on preventing unauthorized data modification. Ensuring data integrity protects against cyberattacks such as tampering, data breaches, and fraud, forming a foundational element for secure communication and reliable decision-making.
Non-repudiation Techniques and Implementation
Non-repudiation techniques ensure the authenticity and origin of data by using digital signatures, cryptographic hash functions, and timestamping, which prevent entities from denying their involvement in a transaction. Implementing non-repudiation involves Public Key Infrastructure (PKI) systems that manage digital certificates and enable robust key management for secure communication. These methods complement integrity measures by providing proof of data origin and delivery, enhancing accountability in secure systems.
Methods for Ensuring Data Integrity
Methods for ensuring data integrity include cryptographic hash functions, which generate unique fixed-size digests for verifying data originality and detect any alterations. Digital signatures combine hashing with asymmetric encryption to provide both integrity and authentication, ensuring the data has not been tampered with and confirming the sender's identity. Error-detecting codes like checksums and cyclic redundancy checks (CRC) also help identify accidental data corruption during transmission or storage.
Common Threats to Non-repudiation and Integrity
Common threats to non-repudiation include repudiation attacks where users deny sending or receiving a message, often exploiting weak or missing digital signatures. Integrity is frequently compromised by data tampering, such as man-in-the-middle attacks or unauthorized modifications during transmission. Both security aspects require robust cryptographic measures like hashing and digital signatures to ensure message authenticity and prevent unauthorized alterations.
Integrating Non-repudiation and Integrity in Security Frameworks
Integrating non-repudiation and integrity within security frameworks ensures that data remains unaltered and that the origin of the data can be irrefutably verified, preventing denial of actions or transactions. Techniques such as digital signatures and cryptographic hash functions are employed to uphold data integrity while providing non-repudiation guarantees across communication channels. Strong integration of these mechanisms fortifies security architectures, enabling robust accountability and trust in digital interactions.
Real-world Examples: Non-repudiation vs Integrity Breaches
Non-repudiation breaches occur when a party denies sending a critical transaction, such as in financial fraud cases where digital signatures are disputed, undermining accountability. Integrity breaches involve unauthorized data modifications, exemplified by hackers altering medical records to affect patient treatment. Both types of security violations highlight the importance of cryptographic techniques; digital signatures ensure non-repudiation, while hashing safeguards data integrity.
Best Practices for Upholding Non-repudiation and Integrity
Best practices for upholding non-repudiation involve implementing digital signatures and secure audit trails to ensure accountability and prevent denial of actions. Maintaining data integrity requires the use of cryptographic hash functions and checksum verification to detect unauthorized alterations. Combining robust access controls with continuous monitoring enhances both non-repudiation and integrity in security protocols.
Non-repudiation vs Integrity Infographic
 difterm.com
difterm.com