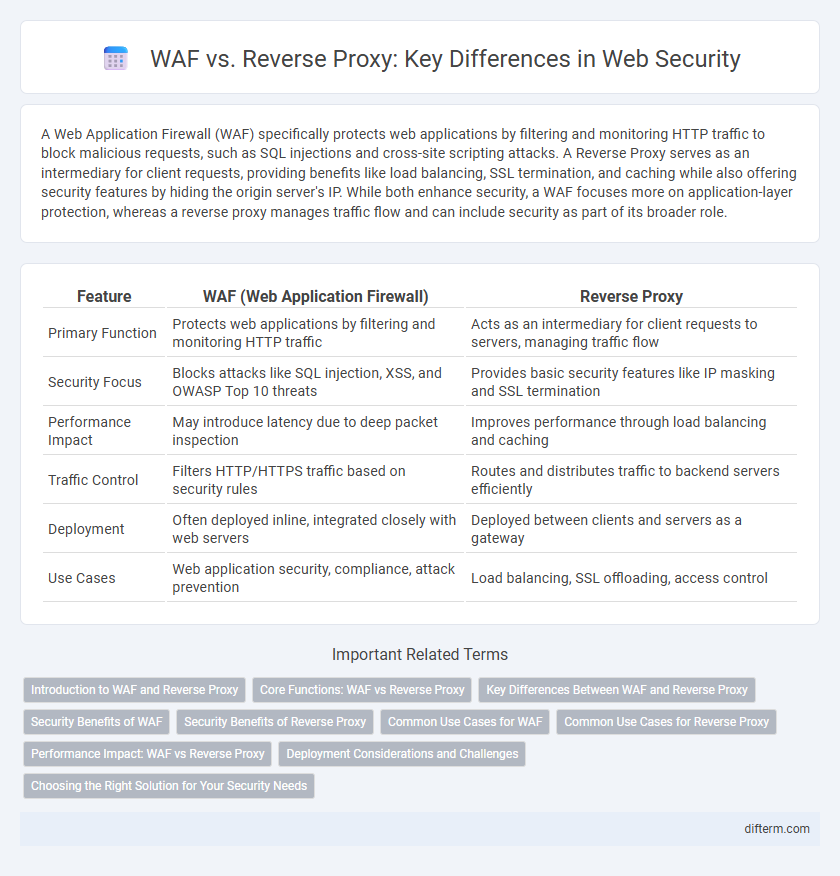
A Web Application Firewall (WAF) specifically protects web applications by filtering and monitoring HTTP traffic to block malicious requests, such as SQL injections and cross-site scripting attacks. A Reverse Proxy serves as an intermediary for client requests, providing benefits like load balancing, SSL termination, and caching while also offering security features by hiding the origin server's IP. While both enhance security, a WAF focuses more on application-layer protection, whereas a reverse proxy manages traffic flow and can include security as part of its broader role.
Table of Comparison
| Feature | WAF (Web Application Firewall) | Reverse Proxy |
|---|---|---|
| Primary Function | Protects web applications by filtering and monitoring HTTP traffic | Acts as an intermediary for client requests to servers, managing traffic flow |
| Security Focus | Blocks attacks like SQL injection, XSS, and OWASP Top 10 threats | Provides basic security features like IP masking and SSL termination |
| Performance Impact | May introduce latency due to deep packet inspection | Improves performance through load balancing and caching |
| Traffic Control | Filters HTTP/HTTPS traffic based on security rules | Routes and distributes traffic to backend servers efficiently |
| Deployment | Often deployed inline, integrated closely with web servers | Deployed between clients and servers as a gateway |
| Use Cases | Web application security, compliance, attack prevention | Load balancing, SSL offloading, access control |
Introduction to WAF and Reverse Proxy
Web Application Firewall (WAF) is a security solution designed to protect web applications by filtering and monitoring HTTP traffic between the internet and the application, effectively blocking malicious attacks like SQL injection and cross-site scripting. Reverse Proxy acts as an intermediary server that directs client requests to backend servers, enhancing security by hiding internal server details, balancing load, and providing SSL termination. Both WAF and Reverse Proxy contribute to securing web environments, with WAF focusing on application-layer threat mitigation and Reverse Proxy emphasizing traffic management and server anonymity.
Core Functions: WAF vs Reverse Proxy
A Web Application Firewall (WAF) primarily protects web applications by filtering and monitoring HTTP traffic to block malicious requests such as SQL injection, cross-site scripting, and zero-day threats. A reverse proxy, while also acting as an intermediary between clients and servers, focuses on load balancing, caching, SSL termination, and improving overall network performance and reliability. Both play crucial roles in security architecture, but WAF is specialized for application-layer threat detection and prevention, whereas reverse proxies enhance traffic management and resource optimization.
Key Differences Between WAF and Reverse Proxy
A Web Application Firewall (WAF) specifically filters and monitors HTTP traffic to protect web applications from attacks such as SQL injection, cross-site scripting, and other OWASP Top Ten threats. A reverse proxy serves as an intermediary for client requests, enhancing security by hiding backend servers, load balancing, and caching content, but it does not provide deep application-level threat detection. The primary distinction lies in WAF's targeted application-layer security versus the reverse proxy's broader role in traffic management and network security.
Security Benefits of WAF
Web Application Firewalls (WAFs) provide targeted protection by filtering and monitoring HTTP traffic to prevent common security threats such as SQL injection, cross-site scripting (XSS), and zero-day exploits. Unlike reverse proxies, WAFs offer granular rule sets tailored specifically for web application vulnerabilities, enhancing security without impacting backend server performance. Their ability to detect and block complex application-layer attacks improves overall cybersecurity posture and compliance with protection standards like OWASP Top 10.
Security Benefits of Reverse Proxy
Reverse proxies enhance security by masking the origin server's IP address, reducing exposure to direct attacks and minimizing the attack surface. They offer centralized access control and advanced threat detection, filtering malicious traffic before it reaches backend servers. Load balancing and SSL termination features further protect applications from DDoS attacks and ensure secure encrypted connections.
Common Use Cases for WAF
Web Application Firewalls (WAFs) protect web applications by filtering and monitoring HTTP traffic to block attacks such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 threats. Common use cases for WAFs include safeguarding e-commerce platforms, protecting public-facing APIs, and ensuring compliance with security standards like PCI DSS. Unlike reverse proxies that primarily handle traffic routing and load balancing, WAFs provide specialized security controls tailored to application-layer threats.
Common Use Cases for Reverse Proxy
Reverse proxies are commonly used for load balancing, SSL termination, and enhancing security by masking backend server IPs from external users. They efficiently distribute incoming traffic across multiple servers, improving website performance and availability. In security contexts, reverse proxies help mitigate DDoS attacks by filtering malicious requests before they reach the web application firewall (WAF) or backend servers.
Performance Impact: WAF vs Reverse Proxy
Web Application Firewalls (WAFs) typically introduce higher latency compared to Reverse Proxies due to deep packet inspection and complex rule evaluation processes aimed at comprehensive threat detection. Reverse Proxies primarily focus on load balancing and caching, resulting in improved response times and reduced server load without extensive security layer overhead. Performance impact assessments show that integrating a WAF can cause up to 30% slower request processing, whereas Reverse Proxies often enhance overall application speed by up to 20%.
Deployment Considerations and Challenges
WAF deployment requires careful integration with existing network architecture to avoid latency and ensure effective traffic inspection, often necessitating inline or out-of-path configurations. Reverse Proxy deployment demands robust resource allocation and secure SSL termination to handle encrypted traffic efficiently while maintaining application performance. Both solutions face challenges related to scalability, false positives, and continuous rule updates to address evolving security threats.
Choosing the Right Solution for Your Security Needs
When selecting between a Web Application Firewall (WAF) and a reverse proxy, consider the specific security threats and performance requirements of your environment. A WAF provides targeted protection by filtering and monitoring HTTP traffic to prevent attacks like SQL injection and cross-site scripting, while a reverse proxy primarily enhances load balancing and anonymity by acting as an intermediary between clients and servers. Evaluating your organization's need for advanced threat detection versus traffic management will guide the choice of the most effective security solution.
WAF vs Reverse Proxy Infographic
 difterm.com
difterm.com