Penetration testing simulates real-world cyberattacks to identify security weaknesses by actively exploiting vulnerabilities in a system. Vulnerability scanning automatically detects and reports known security flaws without exploiting them, offering a broader but less in-depth assessment. Combining both approaches provides a comprehensive security evaluation, addressing potential threats and strengthening defenses.
Table of Comparison
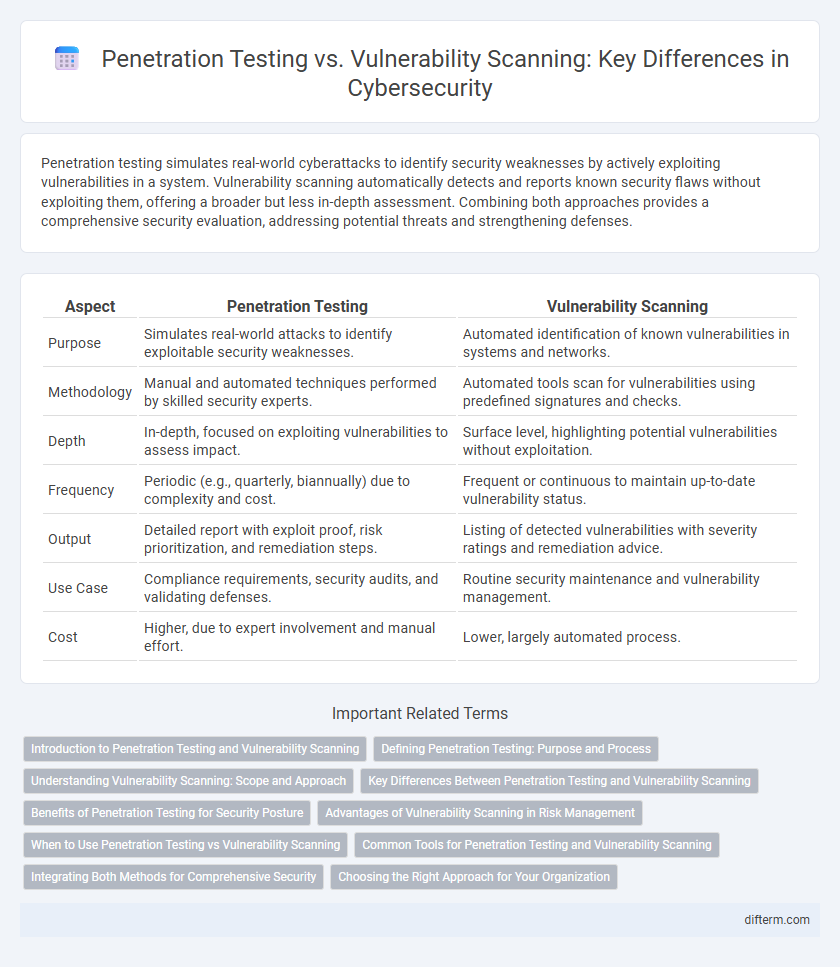
| Aspect | Penetration Testing | Vulnerability Scanning |
|---|---|---|
| Purpose | Simulates real-world attacks to identify exploitable security weaknesses. | Automated identification of known vulnerabilities in systems and networks. |
| Methodology | Manual and automated techniques performed by skilled security experts. | Automated tools scan for vulnerabilities using predefined signatures and checks. |
| Depth | In-depth, focused on exploiting vulnerabilities to assess impact. | Surface level, highlighting potential vulnerabilities without exploitation. |
| Frequency | Periodic (e.g., quarterly, biannually) due to complexity and cost. | Frequent or continuous to maintain up-to-date vulnerability status. |
| Output | Detailed report with exploit proof, risk prioritization, and remediation steps. | Listing of detected vulnerabilities with severity ratings and remediation advice. |
| Use Case | Compliance requirements, security audits, and validating defenses. | Routine security maintenance and vulnerability management. |
| Cost | Higher, due to expert involvement and manual effort. | Lower, largely automated process. |
Introduction to Penetration Testing and Vulnerability Scanning
Penetration testing involves simulating real-world cyberattacks to identify and exploit security weaknesses, providing an in-depth assessment of an organization's defenses. Vulnerability scanning uses automated tools to detect known security flaws across networks, systems, and applications, offering a broad overview of potential risks. Both methods are critical in cybersecurity strategies, with penetration testing delivering detailed insights and vulnerability scanning enabling continuous monitoring.
Defining Penetration Testing: Purpose and Process
Penetration testing is a controlled, simulated cyberattack conducted on a computer system, network, or web application to identify security weaknesses exploitable by hackers. The process involves planning, information gathering, vulnerability analysis, exploitation, and post-exploitation to assess the impact of security gaps. Unlike vulnerability scanning, penetration testing provides a deeper, hands-on evaluation of system defenses by actively attempting to breach cybersecurity measures.
Understanding Vulnerability Scanning: Scope and Approach
Vulnerability scanning systematically identifies security weaknesses across networks, systems, and applications using automated tools to detect known vulnerabilities. It provides a broad overview of potential risks by analyzing configurations, missing patches, and outdated software without exploiting vulnerabilities. This approach helps organizations prioritize remediation efforts by continuously monitoring the security posture and ensuring compliance with industry standards.
Key Differences Between Penetration Testing and Vulnerability Scanning
Penetration testing involves simulating real-world cyberattacks to exploit vulnerabilities and assess security defenses, while vulnerability scanning identifies and reports potential weaknesses in systems without exploiting them. Penetration tests provide in-depth analysis, human expertise, and prioritize risks based on impact, whereas vulnerability scans offer automated, broad coverage and generate extensive lists of possible issues. Key differences include scope, methodology, level of detail, and objectives: penetration testing emphasizes active exploitation and risk validation, while vulnerability scanning focuses on detection and continuous monitoring.
Benefits of Penetration Testing for Security Posture
Penetration testing provides an in-depth assessment of an organization's security posture by simulating real-world cyberattacks to identify exploitable vulnerabilities that automated vulnerability scanning tools might miss. It delivers actionable insights on potential attack vectors, enabling tailored remediation strategies that enhance overall defense mechanisms. This hands-on approach improves risk management by validating the effectiveness of existing security controls and uncovering complex security flaws.
Advantages of Vulnerability Scanning in Risk Management
Vulnerability scanning enables organizations to proactively identify security weaknesses across networks and systems with automated, continuous monitoring that significantly reduces manual effort and time. Its broad coverage and frequent assessments help prioritize remediation efforts by highlighting the most critical vulnerabilities, thus supporting effective risk management strategies. Leveraging vulnerability scanning tools enhances compliance with security standards and regulatory requirements by providing timely and comprehensive risk data.
When to Use Penetration Testing vs Vulnerability Scanning
Penetration testing is crucial for in-depth security assessments, simulating real-world attacks to identify exploitable vulnerabilities and assess the effectiveness of security controls. Vulnerability scanning is ideal for regular, automated identification of known security flaws across systems and networks, enabling continuous monitoring and quick remediation. Organizations should use penetration testing periodically or after major system changes, while vulnerability scanning serves as an ongoing baseline security practice.
Common Tools for Penetration Testing and Vulnerability Scanning
Common tools for penetration testing include Metasploit, Burp Suite, and Kali Linux, which provide advanced capabilities for exploiting security weaknesses and simulating real-world attacks. Vulnerability scanning primarily relies on tools like Nessus, OpenVAS, and Qualys, designed to identify and report known vulnerabilities across networks and systems efficiently. Both types of tools are critical for comprehensive security assessments, with penetration testing tools focusing on active exploitation and vulnerability scanners emphasizing automated detection.
Integrating Both Methods for Comprehensive Security
Integrating penetration testing and vulnerability scanning enhances comprehensive security by combining automated identification of vulnerabilities with manual exploitation techniques. Vulnerability scanning provides a broad overview of potential weaknesses, while penetration testing validates their exploitability and assesses real-world impact. Together, these methods ensure thorough detection, prioritization, and remediation of security gaps, strengthening an organization's defense against cyber threats.
Choosing the Right Approach for Your Organization
Penetration testing provides in-depth security assessment by simulating real-world attacks to uncover exploitable vulnerabilities, making it ideal for organizations requiring comprehensive risk evaluation. Vulnerability scanning offers automated, routine identification of known security weaknesses, suitable for maintaining ongoing awareness of system exposure with less resource investment. Choosing the right approach depends on organizational goals, risk tolerance, regulatory requirements, and available budget for cybersecurity resources.
Penetration Testing vs Vulnerability Scanning Infographic
 difterm.com
difterm.com