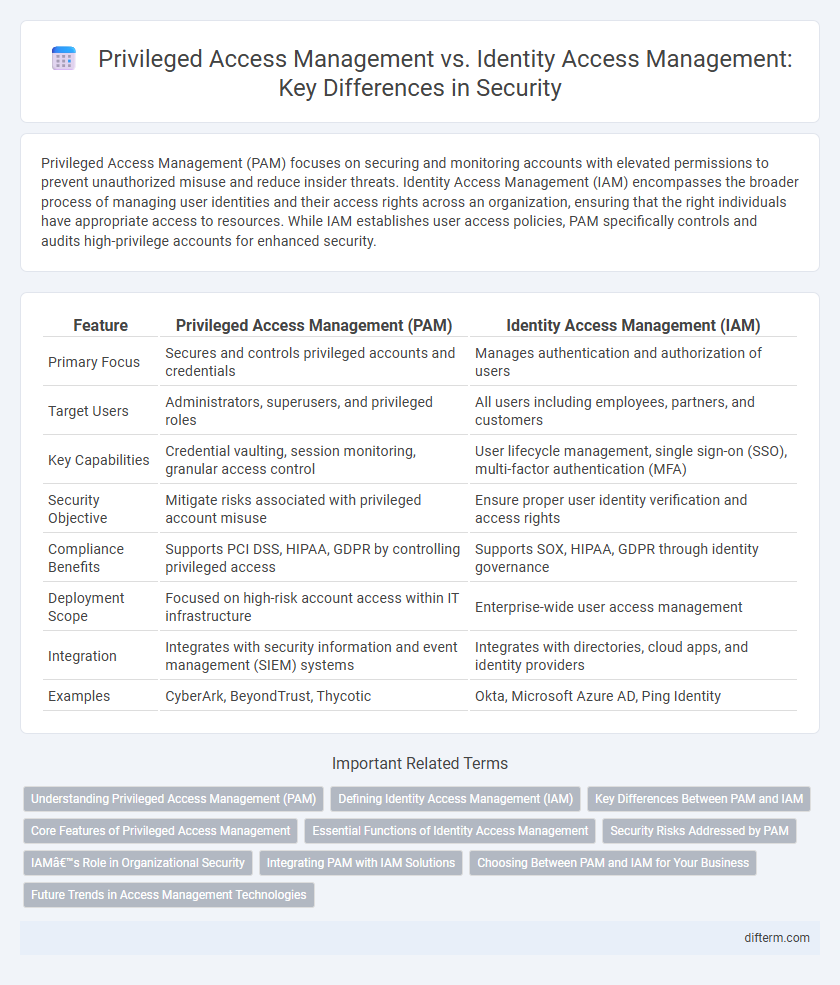
Privileged Access Management (PAM) focuses on securing and monitoring accounts with elevated permissions to prevent unauthorized misuse and reduce insider threats. Identity Access Management (IAM) encompasses the broader process of managing user identities and their access rights across an organization, ensuring that the right individuals have appropriate access to resources. While IAM establishes user access policies, PAM specifically controls and audits high-privilege accounts for enhanced security.
Table of Comparison
| Feature | Privileged Access Management (PAM) | Identity Access Management (IAM) |
|---|---|---|
| Primary Focus | Secures and controls privileged accounts and credentials | Manages authentication and authorization of users |
| Target Users | Administrators, superusers, and privileged roles | All users including employees, partners, and customers |
| Key Capabilities | Credential vaulting, session monitoring, granular access control | User lifecycle management, single sign-on (SSO), multi-factor authentication (MFA) |
| Security Objective | Mitigate risks associated with privileged account misuse | Ensure proper user identity verification and access rights |
| Compliance Benefits | Supports PCI DSS, HIPAA, GDPR by controlling privileged access | Supports SOX, HIPAA, GDPR through identity governance |
| Deployment Scope | Focused on high-risk account access within IT infrastructure | Enterprise-wide user access management |
| Integration | Integrates with security information and event management (SIEM) systems | Integrates with directories, cloud apps, and identity providers |
| Examples | CyberArk, BeyondTrust, Thycotic | Okta, Microsoft Azure AD, Ping Identity |
Understanding Privileged Access Management (PAM)
Privileged Access Management (PAM) centers on controlling and monitoring access to critical systems by users with elevated permissions, reducing the risk of insider threats and cyberattacks. PAM solutions enforce strict authentication, session recording, and real-time activity monitoring to secure administrative accounts and sensitive data. Unlike general Identity Access Management (IAM), which manages overall user identities and roles, PAM specifically targets privilege escalation and enforces least privilege principles within an organization's cybersecurity framework.
Defining Identity Access Management (IAM)
Identity Access Management (IAM) is a cybersecurity framework that ensures the right individuals access appropriate resources within an organization by managing digital identities and their permissions. IAM encompasses authentication, authorization, and user lifecycle management to enforce security policies and reduce risks associated with unauthorized access. Unlike Privileged Access Management (PAM), which specifically controls elevated permissions for critical accounts, IAM provides a broader scope for all user identities across systems and applications.
Key Differences Between PAM and IAM
Privileged Access Management (PAM) focuses on controlling and monitoring access to critical systems by privileged users, ensuring elevated permissions are tightly regulated and audited. Identity Access Management (IAM) manages general user identities and their access rights across an organization's entire IT environment, emphasizing authentication and authorization for all users. Key differences include PAM's targeted approach to high-level credentials and session monitoring versus IAM's broader scope of user access management and identity lifecycle processes.
Core Features of Privileged Access Management
Privileged Access Management (PAM) focuses on securing, managing, and monitoring accounts with elevated permissions, such as system administrators and superusers, to prevent unauthorized access and reduce security risks. Core features of PAM include credential vaulting, session recording, just-in-time access, and automated password rotation, which enhance control over privileged accounts and mitigate insider threats. Unlike Identity Access Management (IAM), which manages user identities and general access rights, PAM specifically targets high-level access to critical systems and sensitive data, ensuring tighter security for privileged activities.
Essential Functions of Identity Access Management
Identity Access Management (IAM) primarily focuses on authenticating users and managing their access rights across systems to ensure only authorized individuals gain entry. Essential IAM functions include user identity verification, role-based access control, password management, and detailed access auditing to maintain security compliance. Privileged Access Management (PAM) complements IAM by specifically securing and monitoring elevated access, but IAM remains critical for managing general user identities and permissions effectively.
Security Risks Addressed by PAM
Privileged Access Management (PAM) specifically targets security risks associated with the misuse of elevated access rights, such as insider threats, credential theft, and unauthorized privilege escalation. Unlike Identity Access Management (IAM), which governs general user access, PAM enforces strict controls on privileged accounts, reducing the attack surface and preventing lateral movement within networks. By implementing PAM, organizations mitigate risks related to privileged credential compromise, ensuring robust protection of critical systems and sensitive data.
IAM’s Role in Organizational Security
Identity Access Management (IAM) plays a critical role in organizational security by controlling and monitoring user identities and their access to resources, ensuring that only authorized individuals can perform specific actions. Unlike Privileged Access Management (PAM), which focuses on managing and securing elevated accounts with high-level privileges, IAM provides a broader scope by enforcing identity verification, authentication, and authorization across the entire user base. Effective IAM implementation reduces the risk of unauthorized access, supports compliance requirements, and enables organizations to maintain a robust security posture.
Integrating PAM with IAM Solutions
Integrating Privileged Access Management (PAM) with Identity Access Management (IAM) solutions enhances security by providing centralized control over both privileged and general user identities. This integration enables real-time monitoring, automated policy enforcement, and streamlined user provisioning, reducing the risk of insider threats and credential misuse. Combining PAM's granular privilege controls with IAM's robust authentication and authorization mechanisms creates a comprehensive security framework that supports compliance and operational efficiency.
Choosing Between PAM and IAM for Your Business
Privileged Access Management (PAM) focuses on securing, managing, and monitoring privileged accounts with elevated permissions, critical for reducing insider threats and preventing high-impact breaches. Identity Access Management (IAM) provides broader user authentication and authorization across all system users, ensuring appropriate access rights based on roles and policies. Businesses should assess the complexity of their access environment and risk profile to determine if a PAM solution is necessary for privileged accounts alongside a comprehensive IAM strategy for overall identity governance.
Future Trends in Access Management Technologies
Future trends in access management technologies emphasize enhanced Privileged Access Management (PAM) and Identity Access Management (IAM) integration, leveraging artificial intelligence and machine learning for real-time threat detection and adaptive authentication. Zero Trust models are driving the evolution of access controls, minimizing risk by enforcing least-privilege access and continuous verification across all user identities and privileged accounts. Emerging solutions focus on automation, behavioral analytics, and cloud-native architectures to secure hybrid environments and improve compliance efficiency.
Privileged Access Management vs Identity Access Management Infographic
 difterm.com
difterm.com