Implementing the principle of least privilege ensures users have only the minimal access necessary to perform their tasks, reducing potential security risks. Need-to-know complements this by restricting access to sensitive information strictly to individuals who require it for specific purposes. Together, these controls form a robust security framework that protects data confidentiality and mitigates insider threats.
Table of Comparison
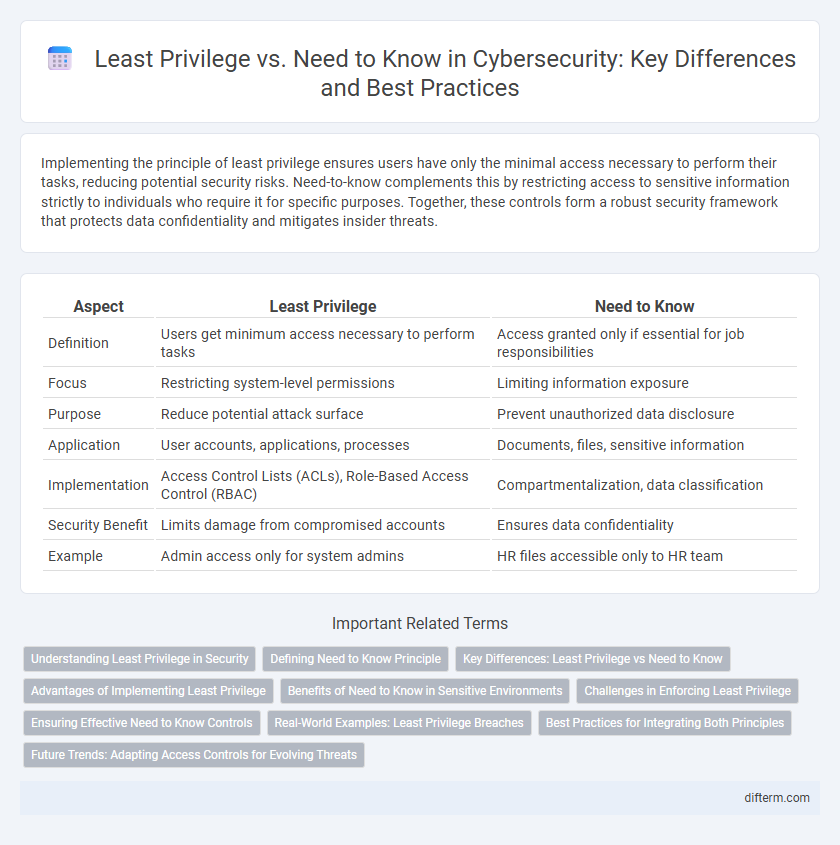
| Aspect | Least Privilege | Need to Know |
|---|---|---|
| Definition | Users get minimum access necessary to perform tasks | Access granted only if essential for job responsibilities |
| Focus | Restricting system-level permissions | Limiting information exposure |
| Purpose | Reduce potential attack surface | Prevent unauthorized data disclosure |
| Application | User accounts, applications, processes | Documents, files, sensitive information |
| Implementation | Access Control Lists (ACLs), Role-Based Access Control (RBAC) | Compartmentalization, data classification |
| Security Benefit | Limits damage from compromised accounts | Ensures data confidentiality |
| Example | Admin access only for system admins | HR files accessible only to HR team |
Understanding Least Privilege in Security
Least Privilege in security enforces users and systems to operate with the minimum permissions necessary, reducing the attack surface and limiting potential damage from breaches. This principle ensures that access rights are granted based solely on operational requirements rather than broader assumptions, enhancing containment of threats. Implementing Least Privilege controls strengthens security posture by minimizing unauthorized access and preventing privilege escalation.
Defining Need to Know Principle
The Need to Know principle restricts access to sensitive information strictly to individuals who require it to perform their job functions, enhancing data confidentiality. Unlike the broader Least Privilege approach, which limits permissions across systems and resources, Need to Know specifically governs the disclosure of classified or sensitive information. This targeted control minimizes insider threats by ensuring that sensitive data is only shared with authorized personnel based on justified necessity.
Key Differences: Least Privilege vs Need to Know
Least Privilege restricts user access rights to the minimum necessary to perform their job functions, reducing the risk of unauthorized actions or data breaches. Need to Know limits access specifically to information that is essential for an individual to complete their tasks, emphasizing confidentiality and compartmentalization. The key difference lies in scope: Least Privilege governs overall system permissions, while Need to Know targets access to sensitive information within those permissions.
Advantages of Implementing Least Privilege
Implementing the Least Privilege principle significantly reduces the attack surface by limiting user and system access to only essential resources, thereby minimizing potential exploitation. This approach enhances compliance with security regulations such as GDPR and HIPAA by ensuring data access is tightly controlled and auditable. Automated enforcement of Least Privilege policies simplifies risk management and accelerates incident response by containing credential misuse within minimal boundaries.
Benefits of Need to Know in Sensitive Environments
Need to Know access limits sensitive information to individuals who require it to perform their job functions, significantly reducing the risk of data breaches and insider threats. This principle enhances operational security by minimizing unnecessary exposure and ensuring accountability in handling classified or confidential data. Implementing Need to Know controls supports compliance with regulatory standards such as HIPAA, GDPR, and FISMA, protecting organizations from legal and financial penalties.
Challenges in Enforcing Least Privilege
Enforcing least privilege in security environments challenges organizations due to the complexity of accurately defining user roles and permissions across diverse systems. Dynamic business needs often require frequent access adjustments, increasing the risk of privilege creep and unauthorized access. Ensuring continuous monitoring and automated access reviews is essential to mitigate security risks associated with excessive privileges.
Ensuring Effective Need to Know Controls
Implementing effective Need to Know controls requires strict access limitations based on the minimum information necessary for job functions, reducing exposure of sensitive data. Combining Need to Know with the Least Privilege principle enhances security by ensuring users receive only the essential access rights relevant to their roles. Continuous monitoring and auditing of access permissions are critical to maintaining robust Need to Know enforcement and preventing unauthorized information disclosure.
Real-World Examples: Least Privilege Breaches
Least Privilege breaches often occur when employees have access rights beyond their job requirements, leading to unauthorized data exposure as seen in the 2017 Equifax breach where excessive permissions allowed attackers to exploit sensitive data. Real-world incidents highlight how over-permissioned accounts enable lateral movement within networks, exemplified by the Target data breach in 2013, where attackers accessed payment information via a third-party vendor with excessive access. Implementing strict Least Privilege controls reduces attack surfaces and limits the damage potential from compromised credentials compared to the broader access scope under Need to Know policies.
Best Practices for Integrating Both Principles
Implementing best practices for integrating Least Privilege and Need to Know principles enhances organizational security by strictly limiting user access to only the necessary resources and information required for their roles. Role-based access control (RBAC) systems and continuous monitoring ensure that permissions are regularly reviewed and adjusted based on job functions and project requirements. Combining these principles reduces the attack surface and minimizes insider threats by enforcing compartmentalization and minimizing data exposure.
Future Trends: Adapting Access Controls for Evolving Threats
Future trends in access control emphasize dynamic implementation of least privilege and need-to-know principles to counter increasingly sophisticated cyber threats. Advanced AI-driven systems enable continuous monitoring and adjustment of user privileges based on real-time risk assessments and behavioral analytics. Organizations adopting adaptive access models enhance security posture by minimizing insider threats and reducing attack surfaces through granular, context-aware permissions.
Least Privilege vs Need to Know Infographic
 difterm.com
difterm.com