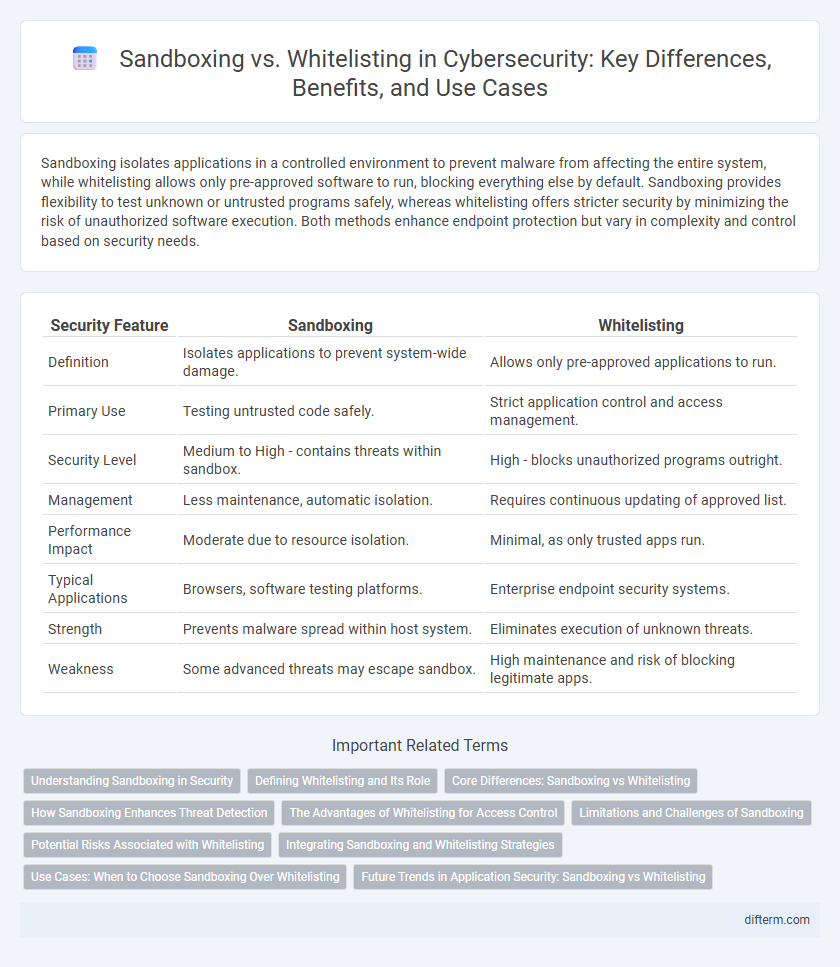
Sandboxing isolates applications in a controlled environment to prevent malware from affecting the entire system, while whitelisting allows only pre-approved software to run, blocking everything else by default. Sandboxing provides flexibility to test unknown or untrusted programs safely, whereas whitelisting offers stricter security by minimizing the risk of unauthorized software execution. Both methods enhance endpoint protection but vary in complexity and control based on security needs.
Table of Comparison
| Security Feature | Sandboxing | Whitelisting |
|---|---|---|
| Definition | Isolates applications to prevent system-wide damage. | Allows only pre-approved applications to run. |
| Primary Use | Testing untrusted code safely. | Strict application control and access management. |
| Security Level | Medium to High - contains threats within sandbox. | High - blocks unauthorized programs outright. |
| Management | Less maintenance, automatic isolation. | Requires continuous updating of approved list. |
| Performance Impact | Moderate due to resource isolation. | Minimal, as only trusted apps run. |
| Typical Applications | Browsers, software testing platforms. | Enterprise endpoint security systems. |
| Strength | Prevents malware spread within host system. | Eliminates execution of unknown threats. |
| Weakness | Some advanced threats may escape sandbox. | High maintenance and risk of blocking legitimate apps. |
Understanding Sandboxing in Security
Sandboxing in security is a technique that isolates applications or processes within a controlled, virtual environment to prevent malicious code from affecting the host system. This containment strategy effectively neutralizes threats by limiting system access and restricting interactions with critical resources. It is widely used in malware analysis, software testing, and endpoint protection to ensure that potentially harmful actions do not spread beyond the sandbox boundaries.
Defining Whitelisting and Its Role
Whitelisting is a security approach that permits only pre-approved applications, users, or IP addresses to access a system, effectively blocking all others by default. This method minimizes the risk of malware and unauthorized access by strictly controlling what is allowed to execute within the network environment. Whitelisting plays a critical role in preventing zero-day attacks and reducing the attack surface by enforcing strict access controls and ensuring only trusted entities operate within the system.
Core Differences: Sandboxing vs Whitelisting
Sandboxing isolates applications or processes within a controlled environment to prevent potential threats from affecting the broader system, while whitelisting restricts execution strictly to pre-approved software known to be safe. Sandboxing allows for dynamic analysis and testing of unknown or untrusted code by containing its activity, whereas whitelisting enforces security through a static list of trusted applications, blocking all others. The core difference lies in sandboxing's emphasis on containment and observation versus whitelisting's focus on proactive prevention through restricted software permissions.
How Sandboxing Enhances Threat Detection
Sandboxing enhances threat detection by isolating suspicious files or programs in a controlled environment, allowing security systems to analyze their behavior without risking the main network. This containment prevents malware from executing harmful actions while enabling detailed inspection of zero-day exploits and advanced persistent threats. By simulating real-world execution, sandboxing provides granular insights into malicious activities, making it a critical tool for identifying unknown threats that bypass traditional whitelisting methods.
The Advantages of Whitelisting for Access Control
Whitelisting offers precise access control by allowing only pre-approved applications or users to execute, significantly reducing the risk of unauthorized or malicious activity. This method minimizes exposure to zero-day exploits by blocking unknown or untrusted software from running. Compared to sandboxing, whitelisting provides a proactive security measure that enforces strict application confinement, enhancing overall system integrity and compliance.
Limitations and Challenges of Sandboxing
Sandboxing limits application threats by isolating processes but struggles with high resource consumption and performance overhead, impacting system efficiency. It often faces compatibility issues with complex software requiring extensive system access, reducing its effectiveness. Moreover, sophisticated threats can sometimes escape sandbox environments, making it less reliable as a standalone security strategy compared to whitelisting.
Potential Risks Associated with Whitelisting
Whitelisting enhances security by allowing only pre-approved applications to run, but it carries potential risks such as administrative overhead and the possibility of excluding legitimate software, which can disrupt business operations. Attackers may exploit vulnerabilities in whitelisted applications or use social engineering to gain approval for malicious software, bypassing whitelist protections. In contrast, sandboxing provides controlled environments for untrusted code, reducing the risk of system-wide compromise from unknown or unverified programs.
Integrating Sandboxing and Whitelisting Strategies
Integrating sandboxing and whitelisting strategies enhances endpoint security by combining proactive threat isolation with strict application control. Sandboxing contains unknown or suspicious code in a secure virtual environment to prevent malware execution, while whitelisting restricts device operations to pre-approved applications. This dual-layered approach ensures rapid threat detection and reduces the attack surface, improving overall network resilience against advanced persistent threats and zero-day exploits.
Use Cases: When to Choose Sandboxing Over Whitelisting
Sandboxing is ideal for environments requiring the execution of untrusted or unknown code, such as software development and malware analysis, because it isolates programs to prevent system-wide damage. Whitelisting is more suitable for controlled settings where only vetted applications are allowed to run, ensuring strict access and minimizing the risk of unauthorized software execution. Choose sandboxing when dynamic testing, behavioral analysis, or flexible application execution is needed, especially in threat detection and zero-day exploit mitigation scenarios.
Future Trends in Application Security: Sandboxing vs Whitelisting
Future trends in application security emphasize the integration of sandboxing and whitelisting techniques to enhance threat detection and prevention. Sandboxing offers dynamic analysis by isolating applications in virtual environments, while whitelisting ensures only trusted software runs, minimizing the attack surface. Emerging AI-driven solutions are expected to optimize the balance between these strategies, improving adaptive security measures against advanced persistent threats and zero-day vulnerabilities.
Sandboxing vs Whitelisting Infographic
 difterm.com
difterm.com