A Security Gateway acts as a checkpoint that filters and controls traffic between internal networks and external sources, enforcing security policies at the network layer. A Security Proxy operates as an intermediary server that processes requests and responses, providing content filtering, anonymization, and detailed traffic inspection at the application layer. Both tools enhance cybersecurity by preventing unauthorized access and mitigating threats, yet they serve distinct functions in network security architecture.
Table of Comparison
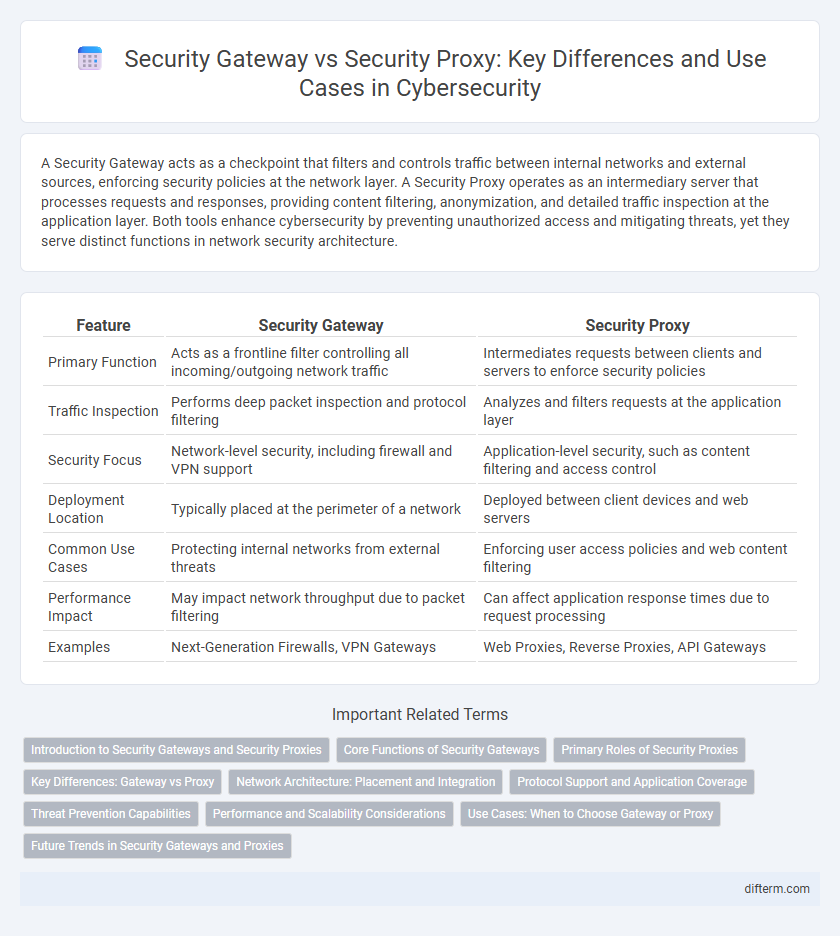
| Feature | Security Gateway | Security Proxy |
|---|---|---|
| Primary Function | Acts as a frontline filter controlling all incoming/outgoing network traffic | Intermediates requests between clients and servers to enforce security policies |
| Traffic Inspection | Performs deep packet inspection and protocol filtering | Analyzes and filters requests at the application layer |
| Security Focus | Network-level security, including firewall and VPN support | Application-level security, such as content filtering and access control |
| Deployment Location | Typically placed at the perimeter of a network | Deployed between client devices and web servers |
| Common Use Cases | Protecting internal networks from external threats | Enforcing user access policies and web content filtering |
| Performance Impact | May impact network throughput due to packet filtering | Can affect application response times due to request processing |
| Examples | Next-Generation Firewalls, VPN Gateways | Web Proxies, Reverse Proxies, API Gateways |
Introduction to Security Gateways and Security Proxies
Security gateways serve as robust barriers between internal networks and external environments by filtering traffic based on predefined security policies and providing centralized threat management. Security proxies act as intermediaries that mask client identities and enforce security measures like content filtering, authentication, and access control to regulate communication between user devices and external servers. Both mechanisms are vital for safeguarding network integrity, with gateways focusing on boundary control and proxies emphasizing secure user-to-server interactions.
Core Functions of Security Gateways
Security gateways serve as critical points of enforcement between internal networks and external connections, managing and filtering incoming and outgoing traffic to prevent unauthorized access and cyber threats. Core functions of security gateways include deep packet inspection, enforcing firewall policies, VPN management, intrusion detection and prevention, and traffic segmentation to maintain secure network boundaries. These robust security measures ensure comprehensive threat protection while maintaining network performance and integrity.
Primary Roles of Security Proxies
Security proxies primarily act as intermediaries between clients and servers, filtering requests and responses to enhance network security by preventing direct access to internal systems. They perform functions such as content filtering, traffic monitoring, and enforcing access controls to detect and block malicious activities. By masking client identities and managing encryption, security proxies protect sensitive data and reduce the risk of cyber threats like malware and unauthorized intrusions.
Key Differences: Gateway vs Proxy
A Security Gateway acts as a barrier that enforces network security policies by filtering traffic between different networks, often operating at the network or transport layer. In contrast, a Security Proxy intermediates client-server communication by inspecting and controlling application-layer data, providing more granular control and content filtering capabilities. Key differences include the Security Gateway's focus on perimeter defense and broader protocol enforcement, while the Security Proxy emphasizes deep packet inspection and user authentication within specific applications.
Network Architecture: Placement and Integration
Security gateways operate at the network perimeter, acting as a centralized control point to monitor and filter all incoming and outgoing traffic, integrating seamlessly with firewalls and intrusion detection systems for comprehensive threat management. Security proxies are positioned between clients and servers, enabling granular inspection and content filtering while enforcing authentication and data encryption policies at the application layer. Efficient network architecture places security gateways to safeguard entire network segments, whereas security proxies focus on securing specific application interactions, optimizing both traffic flow and layered defense strategies.
Protocol Support and Application Coverage
Security gateways specialize in deep protocol inspection, providing robust support for standardized network protocols like IPsec, SSL/TLS, and HTTP/S to enforce security policies across diverse applications. Security proxies operate at the application layer, offering granular control over specific protocols such as HTTP, FTP, and SMTP, enabling detailed content filtering and user authentication. While gateways deliver broad protocol coverage suitable for enterprise-wide network security, proxies offer focused application-layer protection essential for web and email security management.
Threat Prevention Capabilities
Security gateways offer integrated threat prevention capabilities such as intrusion detection, malware scanning, and real-time traffic monitoring to block malicious activities at the network perimeter. Security proxies provide granular content filtering and inspection by intermediating client-server communications, enabling advanced threat analysis on specific application-layer traffic. Combining both can enhance overall protection by leveraging the gateway's comprehensive network defense with the proxy's targeted threat mitigation.
Performance and Scalability Considerations
Security gateways provide strong performance and scalability by handling high volumes of encrypted traffic with hardware acceleration and optimized routing, ensuring minimal latency in large network environments. Security proxies, while offering deep packet inspection and advanced filtering, may introduce latency due to traffic termination and re-encryption processes, which can impact throughput under heavy load. Organizations prioritizing low latency and high scalability often prefer security gateways, especially in scenarios requiring seamless handling of bulk traffic without bottlenecks.
Use Cases: When to Choose Gateway or Proxy
Security gateways are ideal for enterprises requiring comprehensive network-level protection, inspection, and control of inbound and outbound traffic, especially in complex IT environments with diverse protocols. Security proxies are best suited for user-centric applications that demand granular content filtering, privacy, and anonymity, commonly used in web browsing and email security scenarios. Organizations should choose gateways for perimeter defense and policy enforcement across entire network segments, while proxies are preferable for isolating user sessions and managing access at the application level.
Future Trends in Security Gateways and Proxies
Emerging security gateways are increasingly integrating artificial intelligence and machine learning to proactively detect and respond to sophisticated cyber threats in real-time. Security proxies are evolving with enhanced encryption protocols and zero-trust architecture to ensure secure access amid the rise of remote and hybrid work environments. Future trends highlight the convergence of these technologies into unified platforms that offer comprehensive threat intelligence and adaptive security controls.
Security Gateway vs Security Proxy Infographic
 difterm.com
difterm.com