Authorization determines what resources a user can access within a system after their identity has been verified, while authentication is the process of verifying the user's identity through credentials such as passwords or biometric data. Effective security pet solutions implement robust authentication mechanisms to prevent unauthorized access and utilize strict authorization controls to limit user permissions based on roles. Combining both ensures that only verified users can perform actions they are permitted to, enhancing overall system security and protecting sensitive information.
Table of Comparison
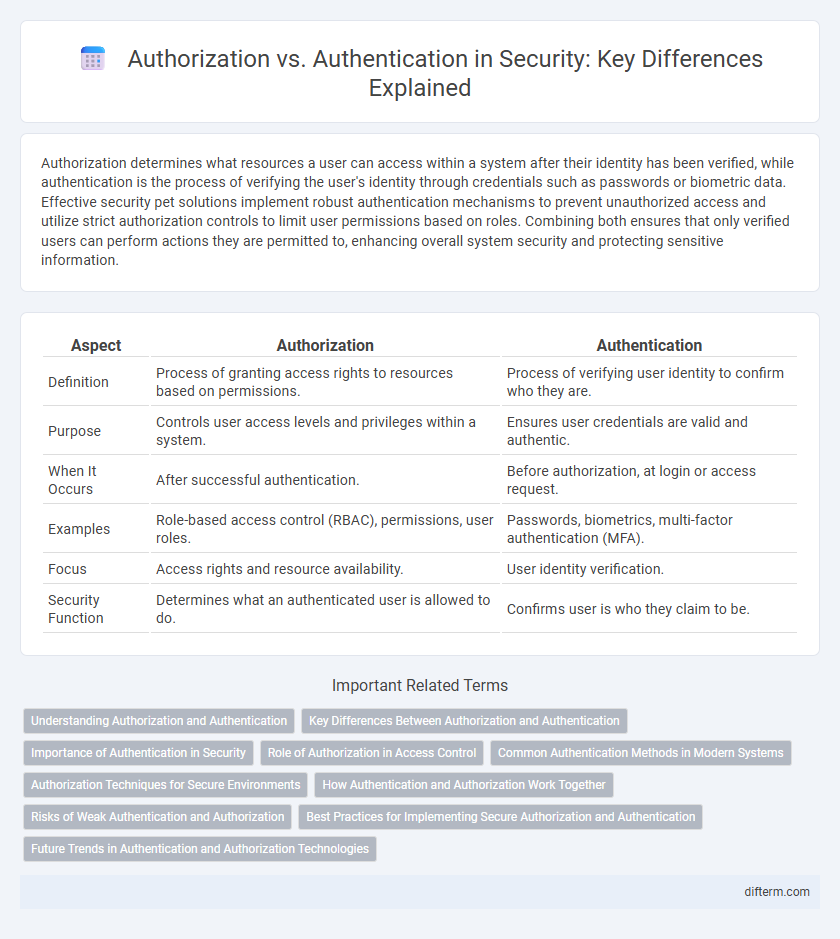
| Aspect | Authorization | Authentication |
|---|---|---|
| Definition | Process of granting access rights to resources based on permissions. | Process of verifying user identity to confirm who they are. |
| Purpose | Controls user access levels and privileges within a system. | Ensures user credentials are valid and authentic. |
| When It Occurs | After successful authentication. | Before authorization, at login or access request. |
| Examples | Role-based access control (RBAC), permissions, user roles. | Passwords, biometrics, multi-factor authentication (MFA). |
| Focus | Access rights and resource availability. | User identity verification. |
| Security Function | Determines what an authenticated user is allowed to do. | Confirms user is who they claim to be. |
Understanding Authorization and Authentication
Authentication verifies the identity of a user or system by validating credentials such as passwords, biometric data, or security tokens. Authorization determines the access level and permissions granted to an authenticated user, controlling what resources or actions they can perform within a system. Understanding the distinction between authentication and authorization is crucial for implementing robust security frameworks and ensuring proper access control.
Key Differences Between Authorization and Authentication
Authentication verifies the identity of a user or system by validating credentials such as passwords, biometrics, or tokens, while authorization determines the access level or permissions granted to the authenticated user within a system. Authentication is the initial security step, ensuring that the entity is who they claim to be; authorization occurs post-authentication, enforcing access control policies based on roles or privileges. In cybersecurity, strong authentication mechanisms combined with granular authorization policies are essential to protect sensitive data and maintain system integrity.
Importance of Authentication in Security
Authentication serves as the foundational security mechanism that verifies user identities, preventing unauthorized access to sensitive systems and data. It ensures that only legitimate users gain entry by validating credentials such as passwords, biometrics, or multi-factor authentication tokens. Robust authentication protocols significantly reduce the risk of identity theft, data breaches, and cyberattacks, reinforcing the overall security posture.
Role of Authorization in Access Control
Authorization determines user permissions and access levels within a system based on predefined roles and policies, ensuring that only authenticated users can perform actions corresponding to their privileges. It enforces access control by validating user entitlements to specific resources, preventing unauthorized data exposure or operations. Effective authorization frameworks integrate role-based access control (RBAC) to streamline permission management and enhance security across applications and networks.
Common Authentication Methods in Modern Systems
Common authentication methods in modern systems include multi-factor authentication (MFA), biometrics, and token-based authentication, which verify user identity before granting access. Passwords remain widely used but are increasingly supplemented by methods such as fingerprint scanning and facial recognition to enhance security. Authentication protocols such as OAuth, SAML, and OpenID Connect streamline secure user verification across multiple platforms and services.
Authorization Techniques for Secure Environments
Authorization techniques for secure environments rely on role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control (PBAC) to determine user permissions. RBAC assigns access rights based on predefined roles within an organization, while ABAC evaluates policies that use attributes like user characteristics, resource types, and environmental conditions. PBAC enhances security by enforcing dynamic permissions linked to organizational policies, ensuring granular control over sensitive data access.
How Authentication and Authorization Work Together
Authentication verifies a user's identity by confirming credentials such as passwords or biometrics, while authorization determines the specific resources or actions the authenticated user is allowed to access. Together, these processes enforce security by ensuring only verified users can perform approved operations within a system. Effective integration of authentication and authorization minimizes unauthorized access and protects sensitive data from exploitation.
Risks of Weak Authentication and Authorization
Weak authentication increases the risk of unauthorized access by allowing attackers to exploit stolen credentials or use brute-force attacks, compromising sensitive data and systems. Inadequate authorization controls can lead to privilege escalation, enabling users to perform actions beyond their permissions and causing significant security breaches. Both weak authentication and authorization amplify vulnerability to identity theft, data leaks, and compliance violations, increasing operational and reputational risks for organizations.
Best Practices for Implementing Secure Authorization and Authentication
Implementing secure authorization and authentication requires enforcing multi-factor authentication (MFA) to reduce the risk of credential compromise and adopting the principle of least privilege to limit user access rights strictly to necessary resources. Utilize robust identity management systems such as OAuth 2.0 and OpenID Connect for scalable and secure authentication workflows, while employing strong encryption protocols like TLS to protect credential data in transit and at rest. Regularly audit access controls and authorization policies to detect anomalies and ensure compliance with security standards such as NIST SP 800-63 and ISO/IEC 27001.
Future Trends in Authentication and Authorization Technologies
Emerging trends in authentication emphasize biometric advancements, such as facial and behavioral recognition, enhancing security beyond traditional passwords. Authorization technologies are evolving with adaptive access controls using artificial intelligence to dynamically assess user privileges based on context and risk factors. The integration of decentralized identity frameworks and zero-trust architectures is set to revolutionize secure access in cloud environments and IoT ecosystems.
Authorization vs Authentication Infographic
 difterm.com
difterm.com