White hat hackers use their skills to identify and fix security vulnerabilities ethically, protecting systems from malicious attacks. Black hat hackers exploit these vulnerabilities for personal gain, causing damage and compromising sensitive data. Understanding the difference between these roles is crucial for developing effective security measures and fostering a safer digital environment.
Table of Comparison
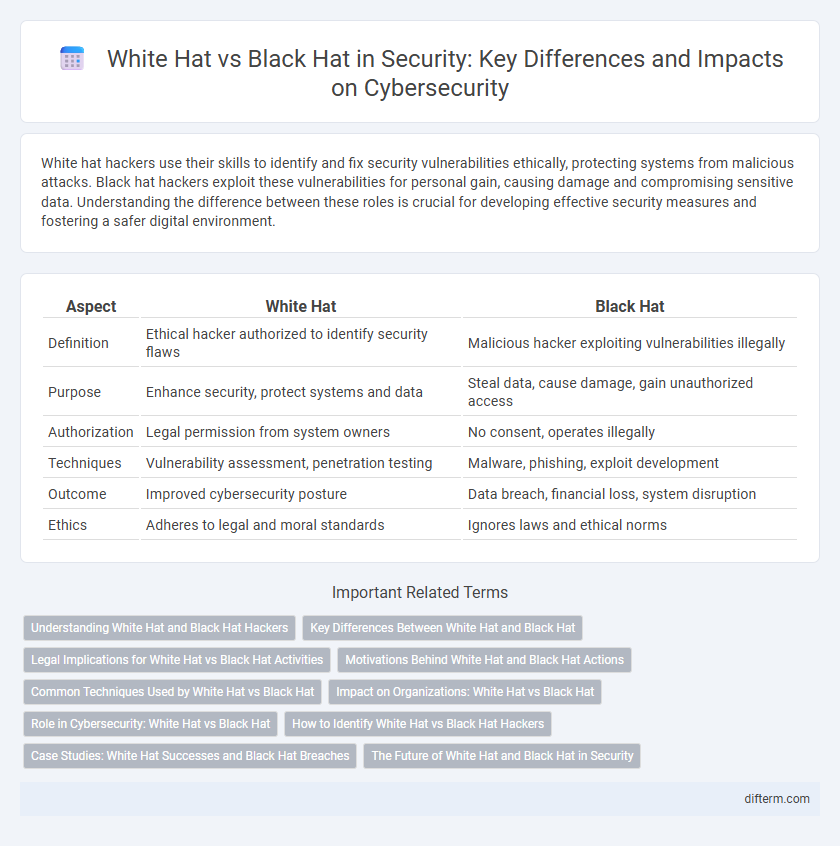
| Aspect | White Hat | Black Hat |
|---|---|---|
| Definition | Ethical hacker authorized to identify security flaws | Malicious hacker exploiting vulnerabilities illegally |
| Purpose | Enhance security, protect systems and data | Steal data, cause damage, gain unauthorized access |
| Authorization | Legal permission from system owners | No consent, operates illegally |
| Techniques | Vulnerability assessment, penetration testing | Malware, phishing, exploit development |
| Outcome | Improved cybersecurity posture | Data breach, financial loss, system disruption |
| Ethics | Adheres to legal and moral standards | Ignores laws and ethical norms |
Understanding White Hat and Black Hat Hackers
White hat hackers use their skills to identify and fix security vulnerabilities, working ethically to protect systems from cyber threats. Black hat hackers exploit these weaknesses for personal or financial gain, often causing data breaches and cybercrime. Understanding the distinct motivations and methods of white hat versus black hat hackers is crucial for developing effective cybersecurity strategies.
Key Differences Between White Hat and Black Hat
White Hat hackers operate with legal authorization to identify and fix security vulnerabilities, focusing on protecting systems and data integrity. Black Hat hackers exploit these vulnerabilities maliciously for personal gain, data theft, or system disruption without permission. The key differences lie in intent, methodology, and compliance with cybersecurity laws and ethical standards.
Legal Implications for White Hat vs Black Hat Activities
White hat hackers operate within legal boundaries by obtaining proper authorization before testing systems, ensuring compliance with cybersecurity laws and regulations. Black hat hackers engage in unauthorized access, violating statutes such as the Computer Fraud and Abuse Act (CFAA), which can lead to criminal charges and civil liabilities. Legal frameworks differentiate these activities based on intent and consent, emphasizing the importance of ethical conduct in cybersecurity practices.
Motivations Behind White Hat and Black Hat Actions
White Hat hackers are motivated by ethical goals such as identifying security vulnerabilities, improving system defenses, and protecting users from malicious attacks. In contrast, Black Hat hackers pursue personal gain, financial profit, or disruption through unauthorized access, data theft, and exploitation of system weaknesses. Understanding these differing motivations is crucial for developing effective cybersecurity strategies and mitigating potential threats.
Common Techniques Used by White Hat vs Black Hat
White hat hackers use ethical methods such as penetration testing, vulnerability assessments, and social engineering to identify and fix security flaws before malicious actors exploit them. Black hat hackers rely on techniques like malware deployment, phishing attacks, SQL injection, and zero-day exploits to breach systems and steal sensitive information. Both groups utilize similar technical skills, but white hats operate with permission and legal boundaries, while black hats violate security to achieve illicit goals.
Impact on Organizations: White Hat vs Black Hat
White Hat hackers enhance organizational security by identifying vulnerabilities before malicious actors can exploit them, reducing the risk of data breaches and financial losses. Black Hat hackers, in contrast, inflict severe damage by stealing sensitive information, disrupting operations, and damaging reputations, leading to substantial legal and recovery costs. Organizations invest heavily in white hat initiatives like penetration testing and ethical hacking to preempt black hat threats and safeguard critical assets.
Role in Cybersecurity: White Hat vs Black Hat
White Hat hackers specialize in ethical hacking to identify vulnerabilities and strengthen cybersecurity defenses through authorized testing and penetration efforts. Black Hat hackers exploit security weaknesses for malicious purposes, often causing data breaches, financial loss, or system damage. The contrasting roles underline the importance of ethical practices and legal compliance in safeguarding digital assets and infrastructure.
How to Identify White Hat vs Black Hat Hackers
White Hat hackers can be identified by their ethical approach to cybersecurity, often working with organizations to find and fix vulnerabilities legally and responsibly. Black Hat hackers operate without permission, aiming to exploit systems for personal gain or malicious intent, frequently leaving traces of unauthorized access or data breaches. Key indicators include White Hats' transparency, use of authorized testing environments, and adherence to legal frameworks, contrasting with Black Hats' covert actions and disregard for laws.
Case Studies: White Hat Successes and Black Hat Breaches
White hat hackers have demonstrated their value in numerous case studies by identifying critical vulnerabilities before malicious actors exploit them, such as the recent discovery of zero-day flaws in prominent software like Microsoft Exchange and Apple iOS. In contrast, black hat breaches have resulted in significant data losses and financial damages, exemplified by incidents like the 2017 Equifax breach that exposed sensitive information of 147 million consumers. Analyzing these cases highlights the importance of ethical hacking in strengthening cybersecurity defenses and mitigating risks from cybercriminal activities.
The Future of White Hat and Black Hat in Security
The future of white hat and black hat cybersecurity hinges on evolving technologies such as artificial intelligence and machine learning, which enhance both offensive and defensive tactics. White hat hackers will increasingly leverage advanced threat detection and ethical hacking frameworks to protect organizations against sophisticated attacks. Conversely, black hat hackers are expected to exploit AI vulnerabilities and automated attack tools, intensifying the cyber threat landscape and necessitating continuous innovation in security protocols.
White Hat vs Black Hat Infographic
 difterm.com
difterm.com