Ransomware encrypts digital files and demands a ransom for their release, causing significant operational disruption and financial loss. Spyware secretly monitors user activity, collecting sensitive data without consent, often leading to privacy breaches and identity theft. Effective cybersecurity strategies must address both threats with robust encryption, real-time monitoring, and user education to minimize risk.
Table of Comparison
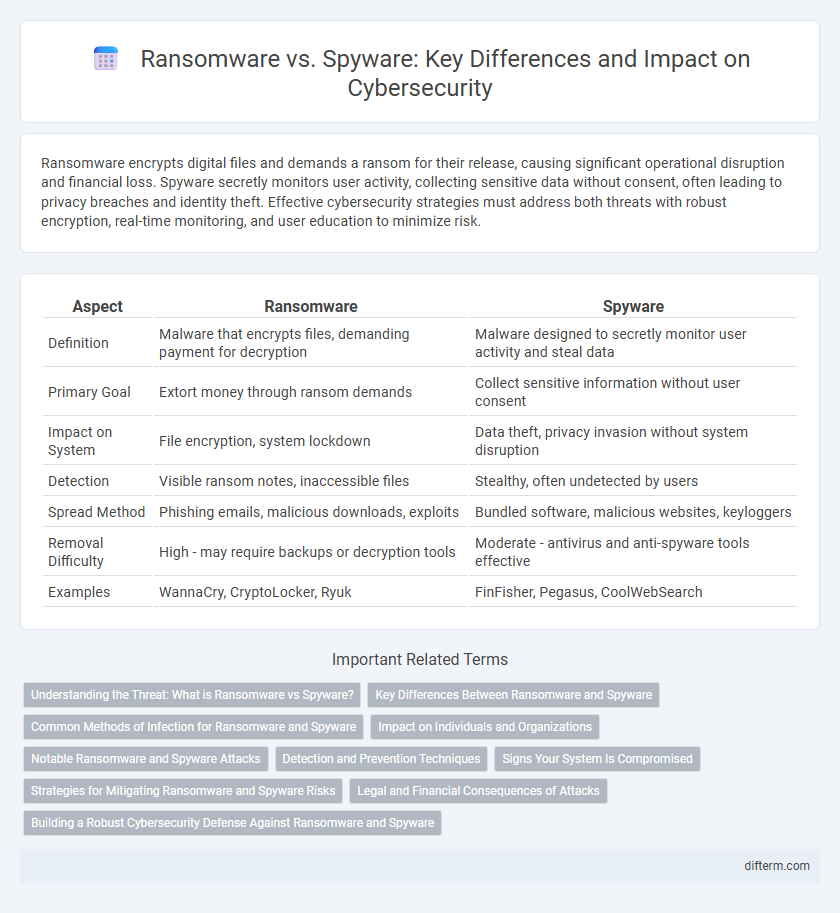
| Aspect | Ransomware | Spyware |
|---|---|---|
| Definition | Malware that encrypts files, demanding payment for decryption | Malware designed to secretly monitor user activity and steal data |
| Primary Goal | Extort money through ransom demands | Collect sensitive information without user consent |
| Impact on System | File encryption, system lockdown | Data theft, privacy invasion without system disruption |
| Detection | Visible ransom notes, inaccessible files | Stealthy, often undetected by users |
| Spread Method | Phishing emails, malicious downloads, exploits | Bundled software, malicious websites, keyloggers |
| Removal Difficulty | High - may require backups or decryption tools | Moderate - antivirus and anti-spyware tools effective |
| Examples | WannaCry, CryptoLocker, Ryuk | FinFisher, Pegasus, CoolWebSearch |
Understanding the Threat: What is Ransomware vs Spyware?
Ransomware is a type of malicious software that encrypts a victim's data, demanding payment for the decryption key, causing significant disruption to personal or organizational operations. Spyware covertly gathers sensitive information such as passwords, financial details, or browsing habits without the user's knowledge, often leading to identity theft or unauthorized access. Understanding the distinct mechanisms and objectives of ransomware and spyware is crucial for implementing effective cybersecurity strategies and threat mitigation.
Key Differences Between Ransomware and Spyware
Ransomware encrypts a victim's data and demands payment for decryption, causing immediate operational disruption and financial loss, while spyware covertly monitors and collects sensitive information without the user's knowledge. The primary impact of ransomware is data inaccessibility and extortion, whereas spyware focuses on stealthy data theft, such as login credentials and personal information. Both pose severe security threats but differ fundamentally in attack method, purpose, and visibility to the victim.
Common Methods of Infection for Ransomware and Spyware
Ransomware commonly infiltrates systems through phishing emails containing malicious attachments or links, exploiting software vulnerabilities via drive-by downloads, and using remote desktop protocol (RDP) brute force attacks. Spyware often spreads by embedding itself in legitimate software downloads, browser plugins, or through deceptive pop-up ads that trick users into installation. Both malware types leverage social engineering tactics and security loopholes to compromise systems and extract information or impose ransom.
Impact on Individuals and Organizations
Ransomware encrypts critical data, causing significant financial losses and operational downtime for both individuals and organizations by demanding payment for data decryption. Spyware covertly collects sensitive information, leading to privacy breaches, identity theft, and long-term damage to reputation and trust. Both threats require robust cybersecurity measures to mitigate their impact and protect digital assets effectively.
Notable Ransomware and Spyware Attacks
Notable ransomware attacks include the 2017 WannaCry outbreak, which affected over 200,000 computers across 150 countries, and the 2021 Colonial Pipeline attack that disrupted fuel supply in the U.S. Prominent spyware incidents involve Pegasus, developed by NSO Group, known for targeting activists and journalists globally, and FinFisher, used by governments to conduct surveillance. Both ransomware and spyware present critical risks by encrypting data or covertly harvesting personal and organizational information, emphasizing the need for robust cybersecurity measures.
Detection and Prevention Techniques
Ransomware detection relies heavily on behavioral analysis and anomaly detection systems that monitor file encryption patterns and unauthorized access to crucial data, while spyware detection focuses on identifying hidden processes and unusual network traffic indicative of data exfiltration. Prevention techniques for ransomware include regular data backups, application whitelisting, and patch management to close vulnerabilities, whereas spyware prevention emphasizes robust endpoint security, real-time malware scanning, and user education to avoid phishing attacks. Both threats require a comprehensive security strategy integrating advanced threat intelligence, multi-layered firewalls, and continuous monitoring to mitigate risks effectively.
Signs Your System Is Compromised
Unusual file extensions, encrypted files, and unresponsive applications often indicate ransomware infection, while slow device performance, unexpected pop-up ads, and unfamiliar software installations suggest spyware presence. Frequent system crashes and increased network activity can signal a compromised system by either malware type. Monitoring system logs and unusual account behavior helps in early detection and mitigation of ransomware and spyware attacks.
Strategies for Mitigating Ransomware and Spyware Risks
Implementing multi-layered security strategies, including robust endpoint protection and regular software updates, significantly reduces ransomware and spyware vulnerabilities. Employee training on phishing awareness and safe browsing habits complements technical defenses by preventing initial infection vectors. Regular data backups and network segmentation ensure rapid recovery and limit the spread of ransomware and spyware within corporate environments.
Legal and Financial Consequences of Attacks
Ransomware attacks often result in substantial financial losses due to ransom payments, business downtime, and recovery costs, alongside potential legal penalties for inadequate data protection under regulations like GDPR or HIPAA. Spyware infections can lead to legal liabilities related to privacy breaches, exposing organizations to lawsuits and fines for failing to safeguard sensitive information. Both types of attacks necessitate stringent cybersecurity measures to mitigate severe financial damage and comply with evolving legal standards.
Building a Robust Cybersecurity Defense Against Ransomware and Spyware
Implementing multi-layered security strategies, including advanced endpoint detection and response (EDR) systems, is crucial to defend against ransomware and spyware threats effectively. Regular software updates, robust encryption protocols, and comprehensive employee training on phishing and social engineering significantly reduce the risk of cyberattacks. Incorporating behavior-based detection and real-time threat intelligence enables rapid identification and mitigation of ransomware and spyware, strengthening overall cybersecurity resilience.
Ransomware vs Spyware Infographic
 difterm.com
difterm.com