Single Sign-On (SSO) allows users to access multiple applications with one set of credentials, streamlining authentication within a single organization. Federated Identity extends this concept by enabling users from different organizations to access each other's systems through shared trust frameworks. Both methods enhance security by reducing password fatigue and centralizing user management, but federated identity is crucial for cross-domain collaboration and seamless user experience across disparate domains.
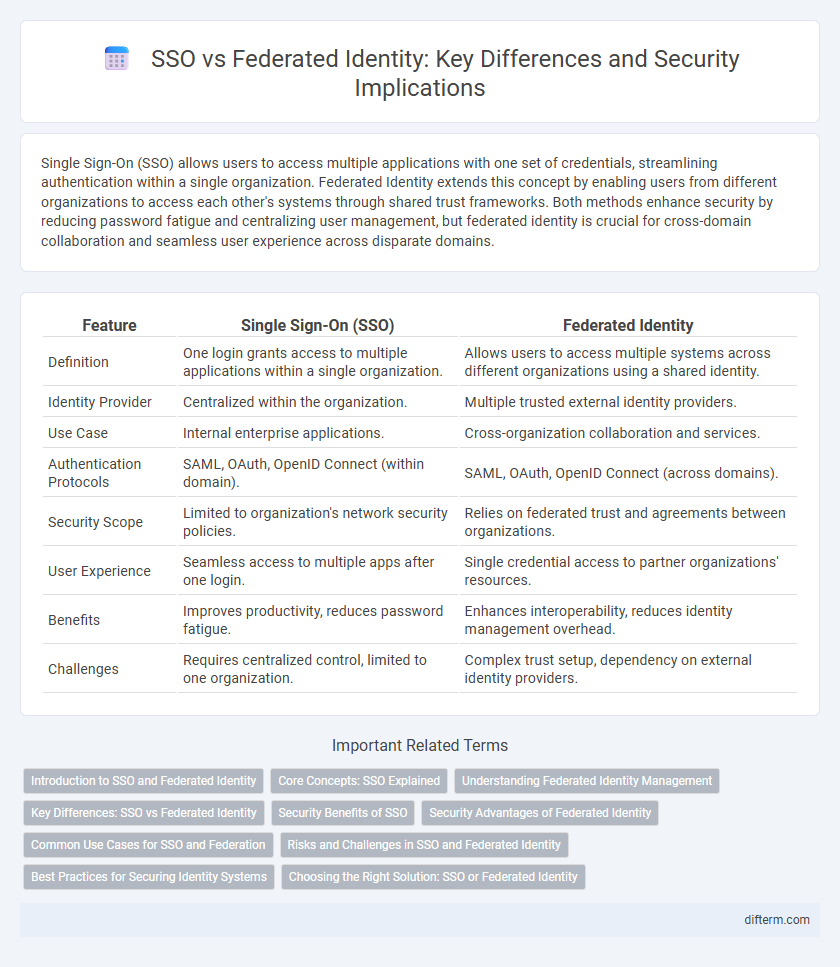
Table of Comparison
| Feature | Single Sign-On (SSO) | Federated Identity |
|---|---|---|
| Definition | One login grants access to multiple applications within a single organization. | Allows users to access multiple systems across different organizations using a shared identity. |
| Identity Provider | Centralized within the organization. | Multiple trusted external identity providers. |
| Use Case | Internal enterprise applications. | Cross-organization collaboration and services. |
| Authentication Protocols | SAML, OAuth, OpenID Connect (within domain). | SAML, OAuth, OpenID Connect (across domains). |
| Security Scope | Limited to organization's network security policies. | Relies on federated trust and agreements between organizations. |
| User Experience | Seamless access to multiple apps after one login. | Single credential access to partner organizations' resources. |
| Benefits | Improves productivity, reduces password fatigue. | Enhances interoperability, reduces identity management overhead. |
| Challenges | Requires centralized control, limited to one organization. | Complex trust setup, dependency on external identity providers. |
Introduction to SSO and Federated Identity
Single Sign-On (SSO) enables users to access multiple applications with one set of login credentials, enhancing security by reducing password fatigue and minimizing attack surfaces. Federated Identity extends this concept by allowing the sharing of authentication and authorization information across different security domains or organizations, facilitating seamless access while maintaining decentralized control. Both approaches improve user experience and strengthen security posture by streamlining identity management and reducing the risks associated with credential proliferation.
Core Concepts: SSO Explained
Single Sign-On (SSO) enables users to authenticate once and gain access to multiple applications or systems without re-entering credentials, enhancing user convenience and security. This centralized authentication mechanism relies on a trusted identity provider (IdP) to validate user credentials and issue security tokens used across connected services. SSO reduces password fatigue and lowers the risk of credential theft by minimizing the number of times users input sensitive information.
Understanding Federated Identity Management
Federated Identity Management (FIM) enables users to access multiple systems across organizational boundaries using a single set of credentials, enhancing security by centralizing authentication processes. Unlike traditional Single Sign-On (SSO), which operates within a single domain, FIM leverages trust relationships and standardized protocols like SAML, OAuth, or OpenID Connect to facilitate seamless identity sharing across diverse platforms. This approach reduces password fatigue, minimizes security risks associated with credential sprawl, and simplifies user access management in complex multi-organization ecosystems.
Key Differences: SSO vs Federated Identity
Single Sign-On (SSO) enables users to authenticate once and gain access to multiple applications within the same organization, streamlining internal user experience. Federated Identity extends this concept by allowing authentication across different organizations or domains, enabling users to use a single set of credentials across multiple trusted entities. The key difference lies in SSO's focus on centralized authentication within a single domain, while Federated Identity facilitates cross-domain identity management and resource sharing.
Security Benefits of SSO
Single Sign-On (SSO) enhances security by reducing the number of passwords users must remember and manage, thereby lowering the risk of weak or reused credentials that can lead to breaches. Centralized authentication in SSO allows for streamlined monitoring and enforcement of security policies such as multi-factor authentication and password complexity rules. This consolidated approach minimizes attack surfaces and simplifies incident response by providing a unified access control framework.
Security Advantages of Federated Identity
Federated identity enhances security by centralizing authentication processes, reducing the risk of password fatigue and credentials reuse across multiple platforms. It enables organizations to enforce consistent access policies and leverage multi-factor authentication from trusted identity providers, minimizing vulnerabilities associated with decentralized user management. Continuous monitoring and real-time threat detection are streamlined in federated systems, improving incident response and reducing the likelihood of unauthorized access.
Common Use Cases for SSO and Federation
Single Sign-On (SSO) is commonly used in enterprise environments to enable users to access multiple internal applications with one set of credentials, enhancing security and user convenience. Federated identity management is prevalent in scenarios requiring cross-organization access, such as business-to-business collaborations or accessing third-party services using corporate credentials. Both solutions improve authentication efficiency but differ in scope: SSO targets centralized access within a single domain, while federation supports trust relationships between distinct identity providers.
Risks and Challenges in SSO and Federated Identity
Single Sign-On (SSO) systems face risks such as credential theft and session hijacking, which can compromise multiple connected services after a single breach. Federated Identity introduces challenges including trust management between identity providers and service providers, and the complexity of establishing secure, standardized protocols across diverse organizations. Both approaches require robust security measures like multi-factor authentication and continuous monitoring to mitigate vulnerabilities and prevent unauthorized access.
Best Practices for Securing Identity Systems
Implement robust multi-factor authentication (MFA) for Single Sign-On (SSO) to enhance security by reducing password-related risks. Employ strict identity verification and trust frameworks in Federated Identity systems to ensure secure cross-domain access while minimizing unauthorized entry. Regularly audit and monitor authentication logs to detect anomalies and enforce least privilege access across both SSO and Federated Identity environments.
Choosing the Right Solution: SSO or Federated Identity
Choosing between Single Sign-On (SSO) and Federated Identity depends on the scope and scale of user access requirements within security architectures. SSO provides streamlined authentication within a single domain or organization, enhancing user experience and reducing password fatigue, while Federated Identity extends secure authentication across multiple organizations or domains, facilitating collaboration without compromising security. Evaluating factors such as cross-domain trust relationships, compliance demands, and integration complexity ensures the selection of the most effective identity management solution.
SSO vs Federated Identity Infographic
 difterm.com
difterm.com