Salting and peppering are security techniques used to enhance password hashing by adding unique or secret data to user passwords before hashing. Salting involves appending a unique, random value to each password, which defends against rainbow table attacks by ensuring identical passwords hash differently. Peppering adds a secret value, kept server-side and not stored with the password hash, providing an additional layer of protection even if the database is compromised.
Table of Comparison
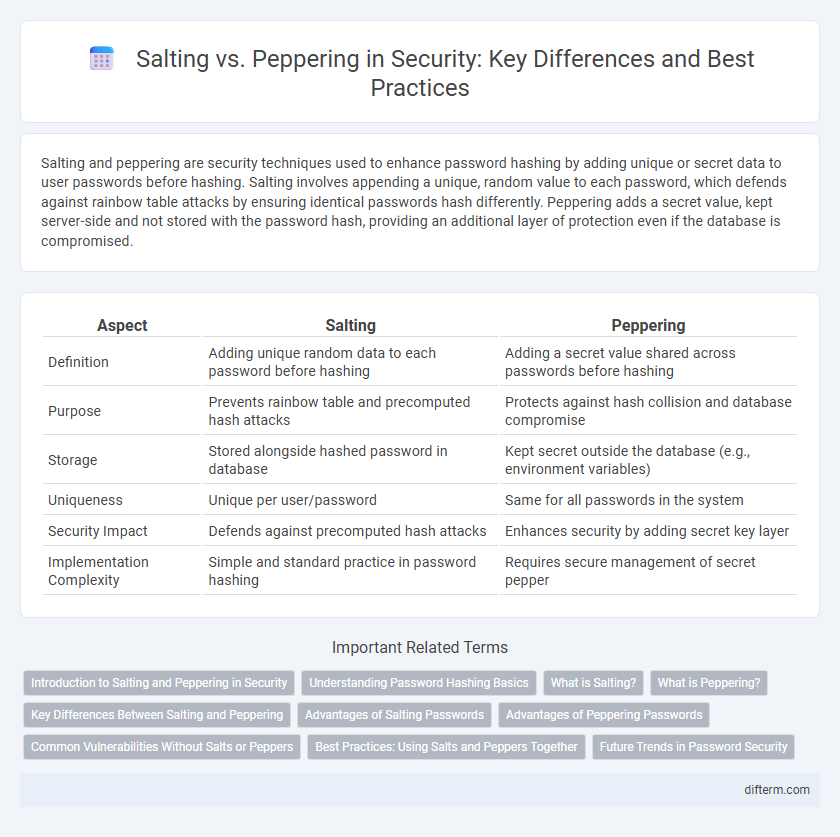
| Aspect | Salting | Peppering |
|---|---|---|
| Definition | Adding unique random data to each password before hashing | Adding a secret value shared across passwords before hashing |
| Purpose | Prevents rainbow table and precomputed hash attacks | Protects against hash collision and database compromise |
| Storage | Stored alongside hashed password in database | Kept secret outside the database (e.g., environment variables) |
| Uniqueness | Unique per user/password | Same for all passwords in the system |
| Security Impact | Defends against precomputed hash attacks | Enhances security by adding secret key layer |
| Implementation Complexity | Simple and standard practice in password hashing | Requires secure management of secret pepper |
Introduction to Salting and Peppering in Security
Salting in security involves adding a unique random value to each password before hashing, significantly enhancing protection against rainbow table attacks by ensuring that identical passwords produce different hashes. Peppering supplements this process by adding a secret value, known only to the server, to the password before hashing, increasing resistance to brute-force attacks even if the hash database is compromised. Combining salt and pepper strengthens password security by mitigating risks associated with stolen hashes and common password vulnerabilities.
Understanding Password Hashing Basics
Salting and peppering enhance password hashing security by adding unique and secret data before hashing, preventing attackers from using precomputed rainbow tables. Salts are random values stored alongside hashed passwords, ensuring each hash is unique even for identical passwords, while peppers are secret values not stored in the database, adding an extra layer of defense against database leaks. Implementing both techniques with strong hash functions like bcrypt or Argon2 significantly improves resistance against brute-force and rainbow table attacks.
What is Salting?
Salting is a security technique that involves adding a unique, random string of characters to a password before hashing to protect against rainbow table attacks. This random salt ensures that even identical passwords produce different hashes, significantly enhancing password storage security. Salts are typically stored alongside the hashed passwords in databases to be used during the verification process.
What is Peppering?
Peppering involves adding a secret value, known as a pepper, to a password before hashing, which is not stored alongside the hashed passwords, enhancing security against database breaches. Unlike salting, which uses unique, per-user random values stored in the database, peppering uses a single secret key managed securely outside of the database environment. This technique reduces the risk of attackers using precomputed hash tables, such as rainbow tables, to reverse-engineer passwords.
Key Differences Between Salting and Peppering
Salting involves adding a unique random value to each password before hashing, ensuring that identical passwords produce distinct hashes and protecting against rainbow table attacks. Peppering uses a secret, fixed value added to passwords prior to hashing, enhancing security by requiring the attacker to know the pepper value to crack the hash. The primary difference lies in salt being unique and stored with the hash, while pepper remains secret and separate from stored data.
Advantages of Salting Passwords
Salting passwords enhances security by adding unique, random data to each password before hashing, which effectively prevents attackers from using precomputed hash tables like rainbow tables. It ensures that identical passwords generate different hashes, increasing resistance against brute force and dictionary attacks. Salting also simplifies password storage and verification processes without exposing the original password or requiring secret keys.
Advantages of Peppering Passwords
Peppering passwords enhances security by adding a secret value stored separately from the password database, making it significantly harder for attackers to crack multiple passwords even if the hash database is compromised. Unlike salting, which uses unique random values per password, peppering applies a consistent secret that strengthens hash resilience against precomputed rainbow table attacks. This method reduces vulnerability to parallel cracking and adds an additional layer of defense by requiring attackers to obtain the secret pepper value before performing effective brute force attempts.
Common Vulnerabilities Without Salts or Peppers
Common vulnerabilities without salts or peppers include susceptibility to rainbow table attacks and brute-force cracking, as unhashed passwords remain vulnerable to precomputed hash lookups. Without unique salts, identical passwords generate identical hashes, enabling attackers to identify and exploit patterns across multiple user accounts. The absence of peppering deprives passwords of an additional layer of secret randomness, reducing resistance to offline attacks and making password hashes easier to reverse-engineer.
Best Practices: Using Salts and Peppers Together
Combining salts and peppers in password hashing enhances security by mitigating risks associated with hash collisions and rainbow table attacks. Salts, unique per user, ensure that identical passwords generate distinct hashes, while peppers add a secret server-side value that guards against database exposure. Best practices recommend securely storing salts with hashes but keeping peppers secret and separate, often implemented via environment variables or hardware security modules.
Future Trends in Password Security
Future trends in password security emphasize enhanced salting techniques combined with global peppering strategies to counteract increasingly sophisticated cyberattacks. Adaptive cryptographic algorithms incorporating dynamic salts and secret peppers improve resistance against rainbow table and brute-force attacks. Integration of AI-driven anomaly detection further strengthens authentication frameworks by identifying irregular access patterns in real time.
salting vs peppering Infographic
 difterm.com
difterm.com