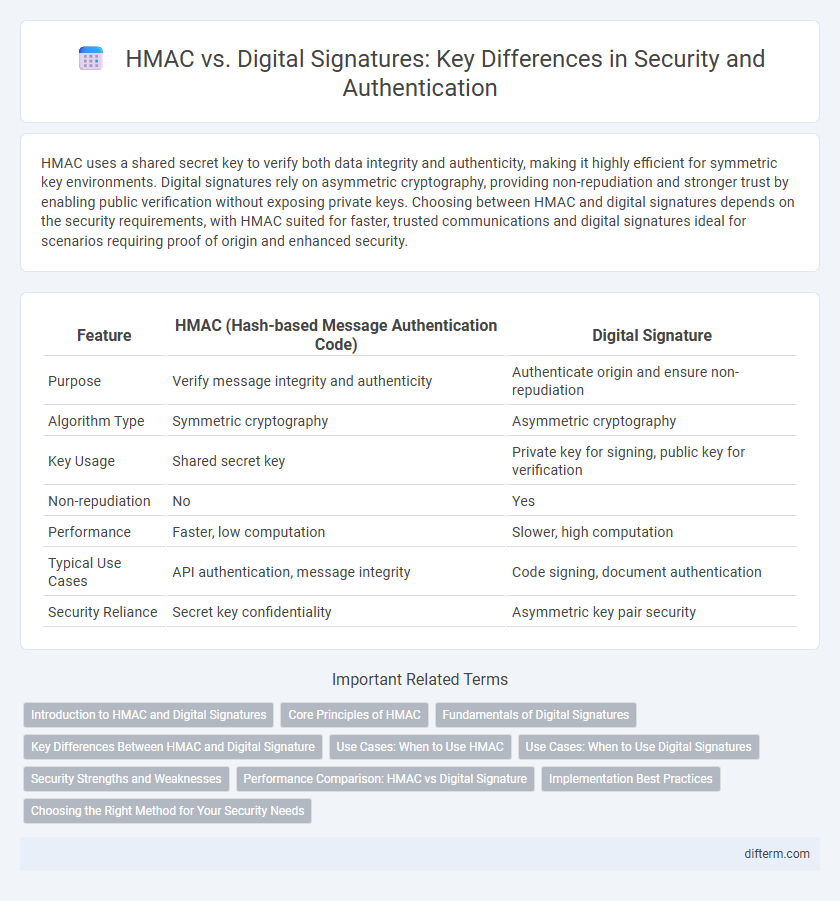
HMAC uses a shared secret key to verify both data integrity and authenticity, making it highly efficient for symmetric key environments. Digital signatures rely on asymmetric cryptography, providing non-repudiation and stronger trust by enabling public verification without exposing private keys. Choosing between HMAC and digital signatures depends on the security requirements, with HMAC suited for faster, trusted communications and digital signatures ideal for scenarios requiring proof of origin and enhanced security.
Table of Comparison
| Feature | HMAC (Hash-based Message Authentication Code) | Digital Signature |
|---|---|---|
| Purpose | Verify message integrity and authenticity | Authenticate origin and ensure non-repudiation |
| Algorithm Type | Symmetric cryptography | Asymmetric cryptography |
| Key Usage | Shared secret key | Private key for signing, public key for verification |
| Non-repudiation | No | Yes |
| Performance | Faster, low computation | Slower, high computation |
| Typical Use Cases | API authentication, message integrity | Code signing, document authentication |
| Security Reliance | Secret key confidentiality | Asymmetric key pair security |
Introduction to HMAC and Digital Signatures
HMAC (Hash-based Message Authentication Code) is a cryptographic algorithm that uses a secret key combined with a hash function to ensure message integrity and authentication. Digital signatures rely on asymmetric encryption, using a private key to sign a message and a public key for verification, providing authentication, non-repudiation, and data integrity. Both HMAC and digital signatures play crucial roles in securing communications, with HMAC favoring symmetric key environments and digital signatures enabling trust in open environments.
Core Principles of HMAC
HMAC (Hash-based Message Authentication Code) relies on a shared secret key combined with a cryptographic hash function to verify both data integrity and authentication. Its core principle involves generating a fixed-size tag from the message and key, ensuring tamper-resistance against unauthorized modifications. Unlike digital signatures that use asymmetric cryptography, HMAC provides efficient symmetric key verification suitable for secure message authentication in real-time communication.
Fundamentals of Digital Signatures
Digital signatures utilize asymmetric cryptography to provide authentication, integrity, and non-repudiation by generating a unique signature with a private key and verifying it with a public key. HMACs, based on symmetric cryptography, ensure data integrity and authenticity but lack non-repudiation since both parties share the secret key. The fundamental advantage of digital signatures lies in their ability to prove the origin of data and prevent denial of authorship in secure communications.
Key Differences Between HMAC and Digital Signature
HMAC relies on a shared secret key and uses cryptographic hash functions to ensure message integrity and authenticity, while digital signatures use asymmetric key pairs involving a private key for signing and a public key for verification, providing non-repudiation. HMAC is faster and suitable for symmetric environments, whereas digital signatures offer stronger security guarantees suitable for public key infrastructure (PKI) and legal validation. Unlike HMAC, digital signatures can also prove the origin of the message independently without prior key sharing.
Use Cases: When to Use HMAC
HMAC is ideal for message authentication in environments where both parties share a secret key, such as internal API communication and token validation within closed systems. It provides efficient integrity and authenticity verification without the computational overhead of asymmetric cryptography, making it suitable for high-throughput applications like payment processing and IoT device communication. Use HMAC when fast, symmetric key-based verification is needed and non-repudiation is not a primary concern.
Use Cases: When to Use Digital Signatures
Digital signatures are ideal for scenarios requiring non-repudiation, such as legal documents, software distribution, and financial transactions, where verifying the sender's identity and ensuring message integrity is critical. Unlike HMAC, which relies on a shared secret and is best suited for internal authentication, digital signatures use asymmetric cryptography to enable public verification without exposing private keys. This makes digital signatures the preferred choice for public communications, contract signing, and compliance with regulatory standards demanding proof of origin and tamper-evidence.
Security Strengths and Weaknesses
HMAC offers strong integrity and authenticity by combining a cryptographic hash function with a secret key, making it resilient against collision and length extension attacks, but it does not provide non-repudiation. Digital signatures, relying on asymmetric cryptography and algorithms like RSA or ECDSA, ensure data integrity, authenticity, and non-repudiation, but their security heavily depends on secure private key management and computational resources. While HMAC is faster and suitable for symmetric key environments, digital signatures provide stronger legal validity and are preferred for scenarios requiring verifiable identity proof.
Performance Comparison: HMAC vs Digital Signature
HMAC offers superior performance compared to digital signatures due to its reliance on symmetric key cryptography, resulting in faster computation and lower resource consumption. Digital signatures, based on asymmetric cryptography, require more processing power and time because of complex mathematical operations like modular exponentiation or elliptic curve computations. In high-throughput environments, HMAC is preferred for efficient message authentication, while digital signatures provide stronger non-repudiation despite slower performance.
Implementation Best Practices
HMAC implementation best practices include using a strong, unique secret key and a secure hash function like SHA-256 to ensure message integrity and authentication. Digital signature best practices emphasize using robust asymmetric key pairs, such as RSA or ECDSA, with proper key management and certificate validation to guarantee non-repudiation. Both methods require regular key rotation and secure storage to mitigate risks associated with key compromise.
Choosing the Right Method for Your Security Needs
HMAC provides efficient message authentication using a shared secret key, making it ideal for fast verification in environments where both parties securely share a key. Digital signatures offer non-repudiation and stronger security guarantees by leveraging asymmetric cryptography, suitable for scenarios demanding public verification and integrity. Selecting between HMAC and digital signatures depends on factors like key management, performance requirements, and the need for legal proof of authenticity.
HMAC vs Digital Signature Infographic
 difterm.com
difterm.com