Rootkits conceal malicious code by embedding themselves deep within an operating system, making detection and removal extremely challenging. Bootkits operate at the firmware or bootloader level, compromising the system before the OS fully loads, which allows them to bypass traditional security measures. Both threats require advanced security tools and methods for effective identification and mitigation.
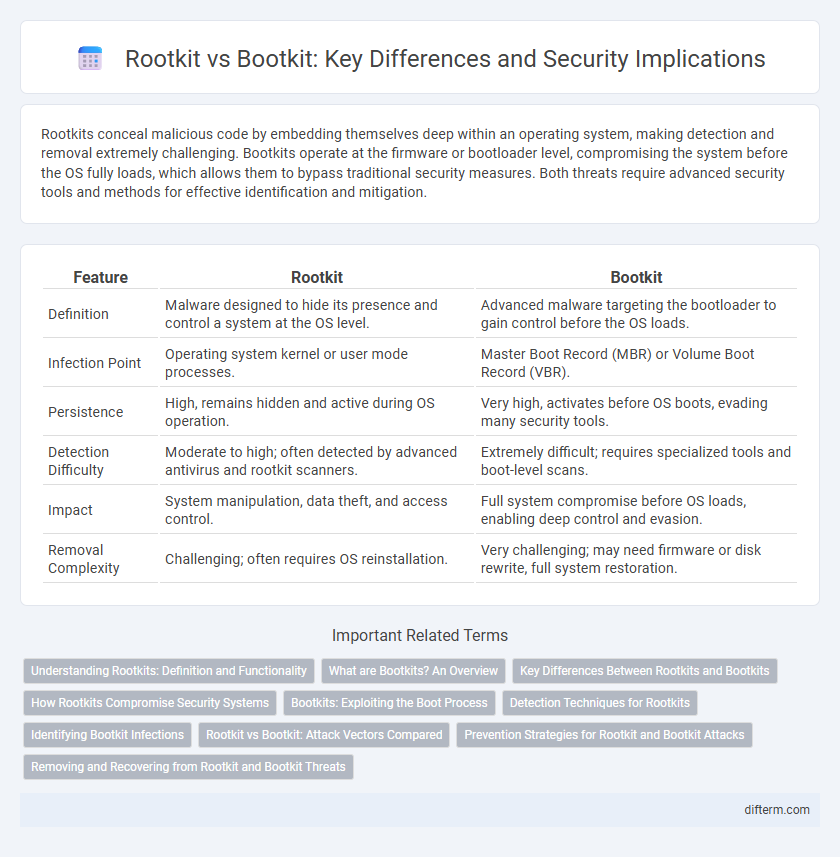
Table of Comparison
| Feature | Rootkit | Bootkit |
|---|---|---|
| Definition | Malware designed to hide its presence and control a system at the OS level. | Advanced malware targeting the bootloader to gain control before the OS loads. |
| Infection Point | Operating system kernel or user mode processes. | Master Boot Record (MBR) or Volume Boot Record (VBR). |
| Persistence | High, remains hidden and active during OS operation. | Very high, activates before OS boots, evading many security tools. |
| Detection Difficulty | Moderate to high; often detected by advanced antivirus and rootkit scanners. | Extremely difficult; requires specialized tools and boot-level scans. |
| Impact | System manipulation, data theft, and access control. | Full system compromise before OS loads, enabling deep control and evasion. |
| Removal Complexity | Challenging; often requires OS reinstallation. | Very challenging; may need firmware or disk rewrite, full system restoration. |
Understanding Rootkits: Definition and Functionality
Rootkits are malicious software designed to gain unauthorized root or administrative access to a computer while hiding their presence, enabling attackers to maintain persistent control and avoid detection. They operate by modifying the operating system or firmware to conceal processes, files, and network activity associated with the malware. Understanding rootkits involves recognizing their stealth techniques, such as hooking system calls or kernel-mode tampering, which allow them to evade traditional security measures.
What are Bootkits? An Overview
Bootkits are sophisticated malware designed to infect the master boot record (MBR) or volume boot record (VBR), allowing them to load before the operating system and evade traditional security measures. Unlike rootkits that operate within the OS, bootkits manipulate the boot process to gain persistent, low-level control over a system, often compromising firmware or bootloader integrity. These threats pose significant challenges for detection and removal, requiring specialized forensic tools and secure boot technologies to protect system trust chains.
Key Differences Between Rootkits and Bootkits
Rootkits operate by infiltrating an operating system at the kernel or user level to conceal malicious activities, whereas bootkits target the bootloader or firmware, compromising the system before the OS loads. Rootkits manipulate system processes and files to maintain stealth, while bootkits modify the boot sequence to gain persistent, low-level control over hardware and software. The critical distinction lies in bootkits' ability to remain undetectable by traditional security tools that monitor the operating system, making them more difficult to detect and remove.
How Rootkits Compromise Security Systems
Rootkits compromise security systems by gaining unauthorized root or administrative access, allowing attackers to hide malicious activities and maintain persistent control over the compromised device. They manipulate operating system processes at the kernel level, making detection difficult for traditional security software. Unlike bootkits, which target the bootloader to infect systems early in the startup sequence, rootkits primarily focus on stealth and privilege escalation within the active OS environment.
Bootkits: Exploiting the Boot Process
Bootkits exploit vulnerabilities in the boot process by injecting malicious code into the Master Boot Record (MBR) or Volume Boot Record (VBR), allowing attackers to gain control before the operating system loads. Unlike rootkits that operate within an OS, bootkits execute early during system startup, making detection and removal significantly more difficult. This pre-OS infection technique enables persistent control over the system, often evading antivirus solutions and security tools.
Detection Techniques for Rootkits
Rootkit detection techniques rely heavily on integrity checking, behavior-based analysis, and signature scanning to identify hidden malicious components within the system. Kernel-level rootkits often require memory dump analysis and specialized tools like rootkit detectors that scan for anomalous kernel modules or hook modifications. Bootkit detection involves monitoring the boot process, but rootkit detection focuses on live system analysis, leveraging anti-rootkit software and heuristics to uncover stealthy persistence mechanisms.
Identifying Bootkit Infections
Bootkit infections are often identified by abnormal boot processes, slow startup times, or unauthorized changes in the Master Boot Record (MBR). Security tools with root-level access, such as specialized boot-time scanners, can detect hidden bootloader modifications that typical antivirus software misses. Monitoring system integrity through firmware and boot sequence analysis provides crucial indicators of bootkit presence.
Rootkit vs Bootkit: Attack Vectors Compared
Rootkits primarily target the operating system by embedding malicious code within system files or processes, enabling stealthy control over the host. Bootkits compromise the master boot record or bootloader, ensuring malware execution before the OS loads, thus evading traditional security measures. Attack vectors differ in that rootkits exploit kernel vulnerabilities or user-mode programs, while bootkits manipulate firmware or boot sectors to achieve persistence at a deeper system level.
Prevention Strategies for Rootkit and Bootkit Attacks
Effective prevention strategies against rootkit and bootkit attacks include maintaining up-to-date security patches and using advanced endpoint protection solutions with behavioral analysis to detect stealthy malware activities. Implementing secure boot mechanisms in hardware ensures only verified code runs during startup, thwarting bootkit infiltration, while frequent integrity checks and system monitoring help identify unauthorized modifications by rootkits. User education on phishing threats and restricting administrative privileges further reduce the risk of initial compromise that can lead to these persistent attacks.
Removing and Recovering from Rootkit and Bootkit Threats
Removing rootkits and bootkits requires specialized tools like antivirus software with advanced scanning capabilities and offline recovery environments to detect hidden malware components. Recovery often involves restoring the system from trusted backups or performing a complete OS reinstall to ensure all compromised boot sectors and system files are clean. Regular firmware updates and bootloader verification enhance protection against re-infection from bootkits and rootkits exploiting low-level system vulnerabilities.
Rootkit vs Bootkit Infographic
 difterm.com
difterm.com