Endpoint Security protects individual devices like laptops and smartphones from malware, unauthorized access, and data breaches by implementing antivirus software, firewalls, and device encryption. Network Security focuses on safeguarding the entire network infrastructure through firewalls, intrusion detection systems, and secure access controls to prevent unauthorized data flow and cyberattacks. Combining both ensures comprehensive protection by addressing vulnerabilities at both the device level and the network level.
Table of Comparison
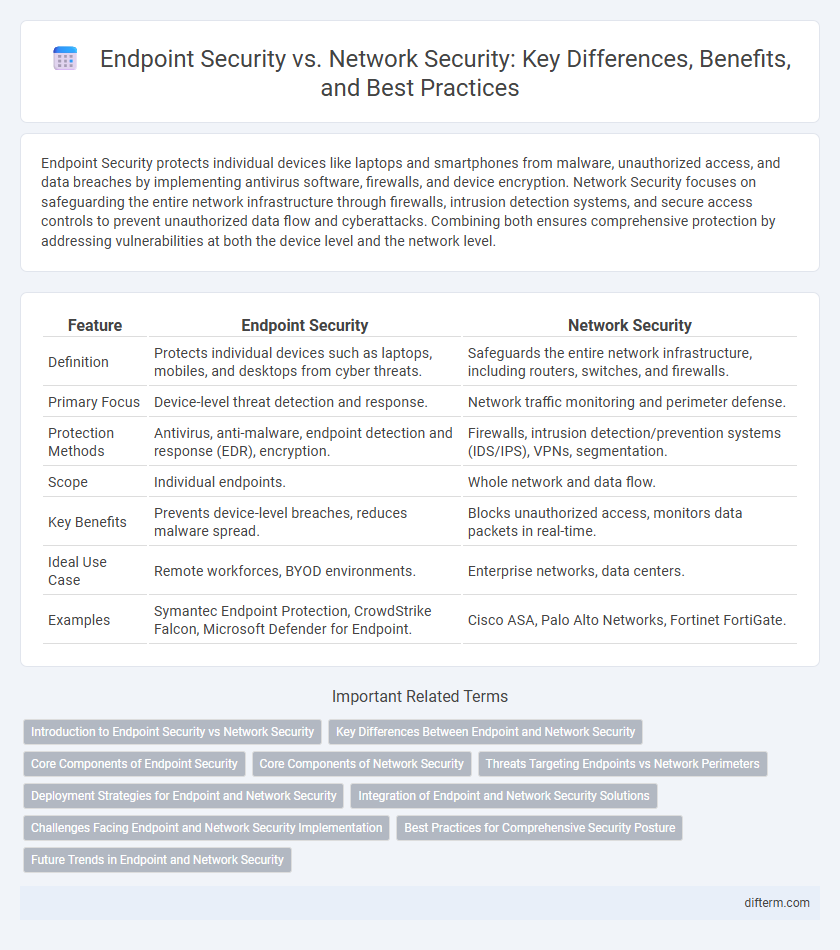
| Feature | Endpoint Security | Network Security |
|---|---|---|
| Definition | Protects individual devices such as laptops, mobiles, and desktops from cyber threats. | Safeguards the entire network infrastructure, including routers, switches, and firewalls. |
| Primary Focus | Device-level threat detection and response. | Network traffic monitoring and perimeter defense. |
| Protection Methods | Antivirus, anti-malware, endpoint detection and response (EDR), encryption. | Firewalls, intrusion detection/prevention systems (IDS/IPS), VPNs, segmentation. |
| Scope | Individual endpoints. | Whole network and data flow. |
| Key Benefits | Prevents device-level breaches, reduces malware spread. | Blocks unauthorized access, monitors data packets in real-time. |
| Ideal Use Case | Remote workforces, BYOD environments. | Enterprise networks, data centers. |
| Examples | Symantec Endpoint Protection, CrowdStrike Falcon, Microsoft Defender for Endpoint. | Cisco ASA, Palo Alto Networks, Fortinet FortiGate. |
Introduction to Endpoint Security vs Network Security
Endpoint security protects individual devices such as laptops, smartphones, and desktops from malware, ransomware, and unauthorized access by implementing antivirus software, device encryption, and behavioral monitoring. Network security safeguards the integrity, confidentiality, and availability of data as it travels across or is stored on a network, utilizing firewalls, intrusion detection systems, and virtual private networks (VPNs). Both security approaches are essential for a comprehensive cybersecurity strategy, addressing different attack vectors and ensuring multilayered defense against cyber threats.
Key Differences Between Endpoint and Network Security
Endpoint security focuses on protecting individual devices like laptops, smartphones, and desktops from malware, unauthorized access, and data breaches by deploying antivirus software, encryption, and endpoint detection and response (EDR) tools. Network security, on the other hand, safeguards the entire network infrastructure by implementing firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) to monitor and control incoming and outgoing traffic. The key difference lies in endpoint security targeting device-specific threats while network security manages broader risks across communication channels and network perimeter defenses.
Core Components of Endpoint Security
Core components of endpoint security include antivirus software, endpoint detection and response (EDR), and data encryption, which work together to protect individual devices from malware, unauthorized access, and data breaches. Endpoint security also integrates application control, device control, and user authentication to ensure comprehensive protection against evolving cyber threats. These components are crucial in maintaining secure endpoints, a foundational layer in the overall cybersecurity strategy.
Core Components of Network Security
Core components of network security include firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and virtual private networks (VPNs) that collectively protect data integrity and confidentiality across communication channels. Network access control (NAC) and secure gateways manage user permissions and filter malicious traffic to prevent unauthorized access and cyber threats. These elements work synergistically to monitor, detect, and respond to network-based vulnerabilities and attacks in real time.
Threats Targeting Endpoints vs Network Perimeters
Threats targeting endpoints typically exploit vulnerabilities in individual devices such as laptops, smartphones, and workstations by deploying malware, ransomware, and phishing attacks. Network perimeter threats focus on unauthorized access attempts, Distributed Denial of Service (DDoS) attacks, and intrusion attempts aimed at breaching firewalls or exploiting network protocols. Endpoint security solutions emphasize device-level protection and real-time monitoring to counteract localized attacks, while network security employs perimeter defenses like firewalls and intrusion detection systems to safeguard the broader network environment.
Deployment Strategies for Endpoint and Network Security
Deployment strategies for endpoint security emphasize installing antivirus, anti-malware, and endpoint detection and response (EDR) solutions directly on individual devices to provide real-time threat protection. Network security deployment focuses on implementing firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) at network perimeters and critical junctions to monitor and control traffic flow. Combining endpoint and network security deployments creates a layered defense that enhances overall organizational cybersecurity posture.
Integration of Endpoint and Network Security Solutions
Integrating endpoint and network security solutions enhances threat detection and response by providing comprehensive visibility across all access points and communication channels. Unified platforms enable real-time data sharing and automated incident response, reducing the risk of breaches caused by isolated security gaps. This synergy improves overall organizational resilience against sophisticated cyberattacks.
Challenges Facing Endpoint and Network Security Implementation
Endpoint security faces challenges in managing the diversity and scale of devices, including mobile, IoT, and remote endpoints, which creates vulnerabilities and complicates consistent policy enforcement. Network security struggles with the increasing complexity of network architectures, cloud integration, and encrypted traffic, making threat detection and real-time monitoring more difficult. Both require advanced solutions like AI-driven analytics and zero-trust frameworks to effectively mitigate evolving cyber threats and maintain robust defense postures.
Best Practices for Comprehensive Security Posture
Endpoint security focuses on protecting individual devices such as laptops, smartphones, and desktops by implementing antivirus software, encryption, and regular patch management. Network security safeguards the integrity and usability of data and services by utilizing firewalls, intrusion detection systems, and segmentation techniques. Integrating strong endpoint security protocols with robust network security measures creates a comprehensive security posture that reduces vulnerabilities and mitigates cyber threats effectively.
Future Trends in Endpoint and Network Security
Future trends in endpoint security emphasize artificial intelligence-driven threat detection and zero-trust architectures to protect increasingly diverse device environments. Network security advancements focus on integrating machine learning for real-time anomaly detection and automating response mechanisms to combat sophisticated cyberattacks. The convergence of endpoint and network security through unified threat intelligence platforms enhances overall protection against evolving cyber threats.
Endpoint Security vs Network Security Infographic
 difterm.com
difterm.com