DoS (Denial of Service) attacks overwhelm a single target system with excessive traffic, causing service disruption or complete outage. DDoS (Distributed Denial of Service) attacks amplify this effect by using multiple compromised devices to flood the target simultaneously, making mitigation more challenging. Effective defense requires robust network monitoring, traffic filtering, and scalable infrastructure to absorb and block malicious traffic surges.
Table of Comparison
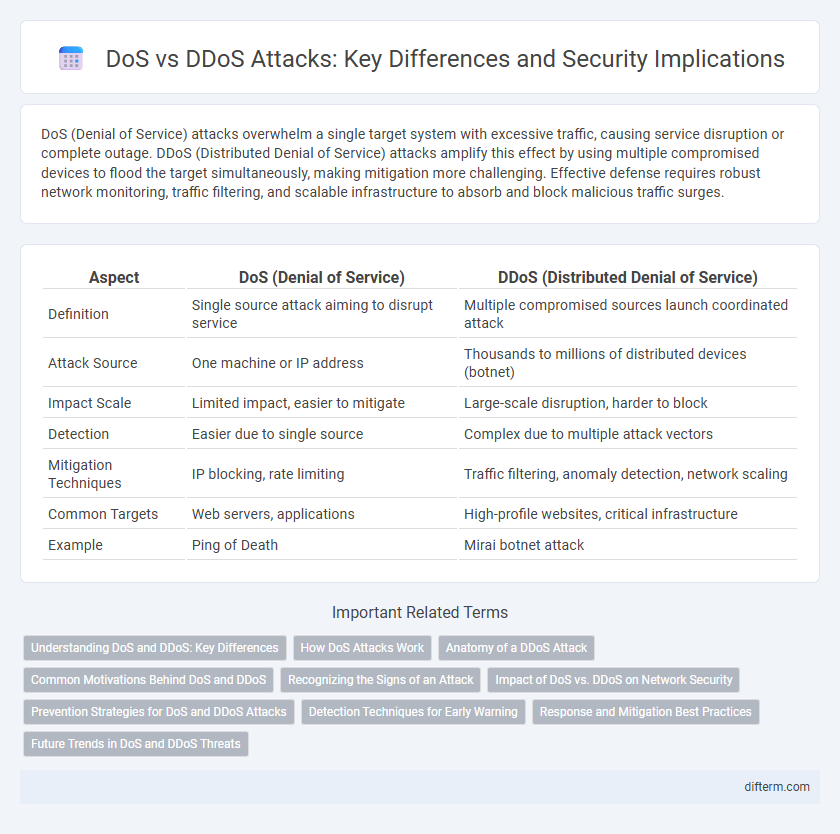
| Aspect | DoS (Denial of Service) | DDoS (Distributed Denial of Service) |
|---|---|---|
| Definition | Single source attack aiming to disrupt service | Multiple compromised sources launch coordinated attack |
| Attack Source | One machine or IP address | Thousands to millions of distributed devices (botnet) |
| Impact Scale | Limited impact, easier to mitigate | Large-scale disruption, harder to block |
| Detection | Easier due to single source | Complex due to multiple attack vectors |
| Mitigation Techniques | IP blocking, rate limiting | Traffic filtering, anomaly detection, network scaling |
| Common Targets | Web servers, applications | High-profile websites, critical infrastructure |
| Example | Ping of Death | Mirai botnet attack |
Understanding DoS and DDoS: Key Differences
DoS (Denial of Service) attacks target a single system or network, flooding it with excessive traffic to exhaust resources and disrupt services. DDoS (Distributed Denial of Service) attacks leverage multiple compromised devices, often forming a botnet, to amplify traffic volume and complicate mitigation efforts. The primary difference lies in scale and source distribution, with DDoS posing a more formidable challenge due to its distributed nature and ability to overwhelm defenses more effectively.
How DoS Attacks Work
DoS attacks work by overwhelming a single target system, server, or network with excessive traffic or requests, causing it to become slow or completely unavailable to legitimate users. Attackers exploit vulnerabilities by sending large volumes of data packets or malformed requests, exhausting resources such as CPU, memory, or bandwidth. This disruption denies service, preventing authorized users from accessing critical online services or networks.
Anatomy of a DDoS Attack
A Distributed Denial of Service (DDoS) attack involves multiple compromised systems, often part of a botnet, flooding a target with massive volumes of traffic to overwhelm its resources and disrupt service availability. Unlike a basic Denial of Service (DoS) attack, which originates from a single source, a DDoS attack utilizes diverse attack vectors such as UDP floods, SYN floods, and application-layer attacks to exploit vulnerabilities and evade traditional security defenses. Key components of a DDoS attack include the command and control (C&C) infrastructure, compromised devices acting as bots, and the overwhelmed target server or network infrastructure.
Common Motivations Behind DoS and DDoS
DoS and DDoS attacks typically stem from motivations such as financial gain, where attackers aim to extort businesses via ransom demands, or hacktivism, driven by political or social agendas to disrupt targeted organizations. Cybercriminals often seek to damage reputations by causing prolonged downtime, impacting customer trust and operational continuity. Competitors may also employ these attacks to sabotage rival services, leading to lost revenue and market share.
Recognizing the Signs of an Attack
Recognizing the signs of a DoS attack includes unusually slow network performance, unavailability of a particular website, or an inability to access any network services. In contrast, a DDoS attack often results in widespread disruption, with multiple sources flooding the network, leading to a complete shutdown of systems and services. Monitoring traffic patterns and identifying abnormal spikes from diverse IP addresses is crucial for differentiating between DoS and DDoS attacks.
Impact of DoS vs. DDoS on Network Security
DoS attacks overwhelm a single network resource, causing temporary service disruption, while DDoS attacks leverage multiple compromised systems, amplifying attack scale and making mitigation more complex. The distributed nature of DDoS significantly increases network congestion, leading to extended downtime and greater risk to network integrity compared to the localized effect of DoS. Organizations face higher operational costs and more sophisticated defense requirements against DDoS due to its broader impact on network security and availability.
Prevention Strategies for DoS and DDoS Attacks
Effective prevention strategies for DoS and DDoS attacks include implementing robust firewall rules, rate limiting, and traffic filtering to block malicious traffic before it reaches critical infrastructure. Deploying intrusion detection and prevention systems (IDPS) combined with cloud-based DDoS mitigation services enhances real-time response and absorbs attack traffic. Regularly updating software, conducting vulnerability assessments, and establishing incident response plans further minimize the risk and impact of both DoS and DDoS threats.
Detection Techniques for Early Warning
Detecting DoS and DDoS attacks early relies on monitoring abnormal traffic patterns such as sudden spikes in packet rates or unusual IP address distributions. Advanced techniques include anomaly-based detection using machine learning models that analyze network behavior in real-time to identify deviations from baseline metrics. Signature-based methods complement this by recognizing known attack vectors through pattern matching, enabling quicker response to early warning signals.
Response and Mitigation Best Practices
Effective response to DoS and DDoS attacks involves immediate traffic analysis to identify malicious patterns and filter out attack traffic using firewalls and intrusion prevention systems. Mitigation best practices highlight deploying scalable solutions like cloud-based scrubbing centers and rate limiting to manage traffic spikes without disrupting legitimate users. Continuous monitoring, timely updates to signatures, and incident response plans are critical for minimizing downtime and maintaining network integrity during attacks.
Future Trends in DoS and DDoS Threats
Emerging future trends in DoS and DDoS threats highlight the increasing use of AI-driven attack automation, enabling more sophisticated and adaptive disruption methods. Botnets leveraging IoT devices are expected to multiply, significantly expanding attack surfaces and amplifying the scale and frequency of DDoS campaigns. Advances in cloud-based mitigation strategies and AI-powered detection systems are critical to counter evolving threats in this rapidly changing cybersecurity landscape.
DoS vs DDoS Infographic
 difterm.com
difterm.com