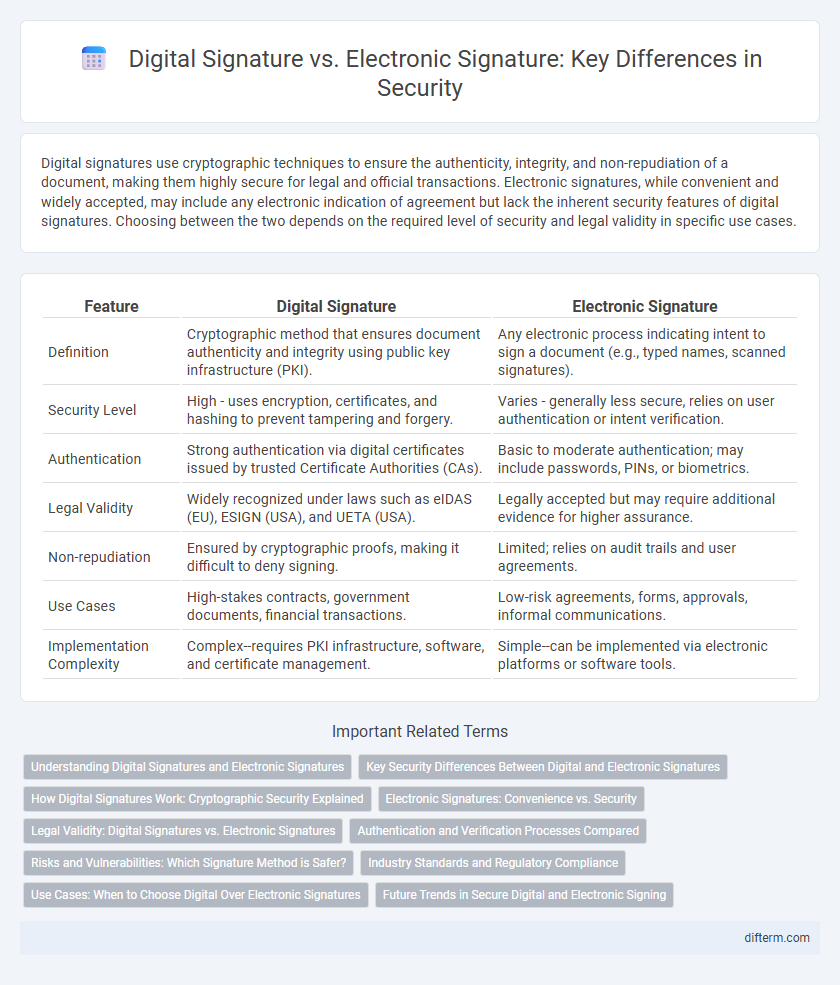
Digital signatures use cryptographic techniques to ensure the authenticity, integrity, and non-repudiation of a document, making them highly secure for legal and official transactions. Electronic signatures, while convenient and widely accepted, may include any electronic indication of agreement but lack the inherent security features of digital signatures. Choosing between the two depends on the required level of security and legal validity in specific use cases.
Table of Comparison
| Feature | Digital Signature | Electronic Signature |
|---|---|---|
| Definition | Cryptographic method that ensures document authenticity and integrity using public key infrastructure (PKI). | Any electronic process indicating intent to sign a document (e.g., typed names, scanned signatures). |
| Security Level | High - uses encryption, certificates, and hashing to prevent tampering and forgery. | Varies - generally less secure, relies on user authentication or intent verification. |
| Authentication | Strong authentication via digital certificates issued by trusted Certificate Authorities (CAs). | Basic to moderate authentication; may include passwords, PINs, or biometrics. |
| Legal Validity | Widely recognized under laws such as eIDAS (EU), ESIGN (USA), and UETA (USA). | Legally accepted but may require additional evidence for higher assurance. |
| Non-repudiation | Ensured by cryptographic proofs, making it difficult to deny signing. | Limited; relies on audit trails and user agreements. |
| Use Cases | High-stakes contracts, government documents, financial transactions. | Low-risk agreements, forms, approvals, informal communications. |
| Implementation Complexity | Complex--requires PKI infrastructure, software, and certificate management. | Simple--can be implemented via electronic platforms or software tools. |
Understanding Digital Signatures and Electronic Signatures
Digital signatures use cryptographic algorithms to provide a secure, tamper-evident method of verifying the authenticity and integrity of digital documents, ensuring non-repudiation. Electronic signatures are broader in scope, encompassing any electronic process that signifies intent to sign, such as typed names, scanned images, or click-to-sign methods, but may lack strong security features. Understanding the distinctions highlights digital signatures' role in legal compliance and data protection compared to electronic signatures' convenience and varied security levels.
Key Security Differences Between Digital and Electronic Signatures
Digital signatures use cryptographic keys to create a secure, unique signature that verifies the signer's identity and ensures document integrity through public key infrastructure (PKI). Electronic signatures, while legally binding, often lack the robust encryption and key management systems, making them more vulnerable to tampering or fraud. The primary key security difference lies in digital signatures' reliance on private and public keys for verification, providing higher authenticity and non-repudiation compared to the simpler authentication methods used by electronic signatures.
How Digital Signatures Work: Cryptographic Security Explained
Digital signatures use public key infrastructure (PKI) to create a unique cryptographic hash linked to the signer's private key, ensuring data integrity and authenticity. When a document is signed, the hash is encrypted with the private key and can be verified by anyone using the corresponding public key, confirming the signature's validity and the document's unchanged state. This process provides stronger security compared to electronic signatures, which may lack cryptographic proof and are often limited to basic verification methods.
Electronic Signatures: Convenience vs. Security
Electronic signatures offer unparalleled convenience by enabling quick, remote signing without the need for physical documents, making them ideal for fast-paced digital transactions. However, their security can vary significantly depending on the technology used, with some electronic signatures being more vulnerable to forgery and unauthorized access compared to digital signatures, which rely on cryptographic methods. Ensuring robust authentication protocols and compliance with standards like eIDAS or ESIGN Act is critical to balancing ease of use with strong security in electronic signature implementations.
Legal Validity: Digital Signatures vs. Electronic Signatures
Digital signatures use cryptographic techniques to provide a unique, tamper-evident seal, ensuring high legal validity under regulations like eIDAS in the EU and ESIGN Act in the US. Electronic signatures encompass a broader range of methods, including scanned images or typed names, which may have variable legal acceptance depending on jurisdiction and context. Courts often favor digital signatures for their enhanced security and verifiability, making them more reliable for legally binding agreements.
Authentication and Verification Processes Compared
Digital signatures use cryptographic algorithms to authenticate the signer's identity and ensure data integrity through a unique private key, providing a robust verification process. Electronic signatures may rely on various methods such as typed names, scanned images, or simple click-to-sign actions, offering less secure authentication and easier forgery risks. The cryptographic verification in digital signatures enables non-repudiation, whereas electronic signatures often require supplementary measures for reliable validation.
Risks and Vulnerabilities: Which Signature Method is Safer?
Digital signatures employ cryptographic algorithms that provide authentication, integrity, and non-repudiation, significantly reducing risks like forgery and tampering. Electronic signatures, while convenient, often lack robust encryption and are more vulnerable to impersonation, alteration, and unauthorized access. Evaluating security protocols reveals that digital signatures offer superior protection against cyberattacks and data breaches compared to electronic signatures.
Industry Standards and Regulatory Compliance
Digital signatures comply with industry standards such as ISO/IEC 14533 and eIDAS regulation, ensuring cryptographic security and legal validity for electronic transactions. Electronic signatures, while easier to implement, often lack standardized cryptographic methods and may not meet stringent regulatory requirements like HIPAA or GDPR. Organizations must select digital signatures to achieve higher assurance of authenticity, integrity, and non-repudiation in regulated environments.
Use Cases: When to Choose Digital Over Electronic Signatures
Digital signatures provide higher security and legal authenticity, making them ideal for contracts, government documents, and financial transactions requiring non-repudiation and tamper-proof verification. Electronic signatures offer convenience for low-risk agreements like internal approvals or consent forms where speed and ease of use are prioritized over stringent authentication. Selecting digital signatures is crucial when compliance with regulations such as eIDAS or UETA is mandatory or when the integrity and origin of the document must be indisputably verified.
Future Trends in Secure Digital and Electronic Signing
Future trends in secure digital and electronic signing emphasize enhanced cryptographic algorithms such as quantum-resistant keys to safeguard against emerging cyber threats. Integration of blockchain technology ensures immutability and transparent audit trails, boosting trust and compliance in digital transactions. Biometric authentication combined with AI-powered anomaly detection further strengthens identity verification and prevents fraudulent signatures.
Digital Signature vs Electronic Signature Infographic
 difterm.com
difterm.com