Risk assessment evaluates the potential impact and likelihood of threats exploiting vulnerabilities within an organization's assets, helping prioritize security measures based on overall risk levels. Vulnerability assessment identifies and catalogs weaknesses or gaps in systems, networks, and applications but does not consider the probability or impact of exploitation on its own. Combining both assessments provides a comprehensive security strategy, balancing technical flaws with risk prioritization to strengthen defenses effectively.
Table of Comparison
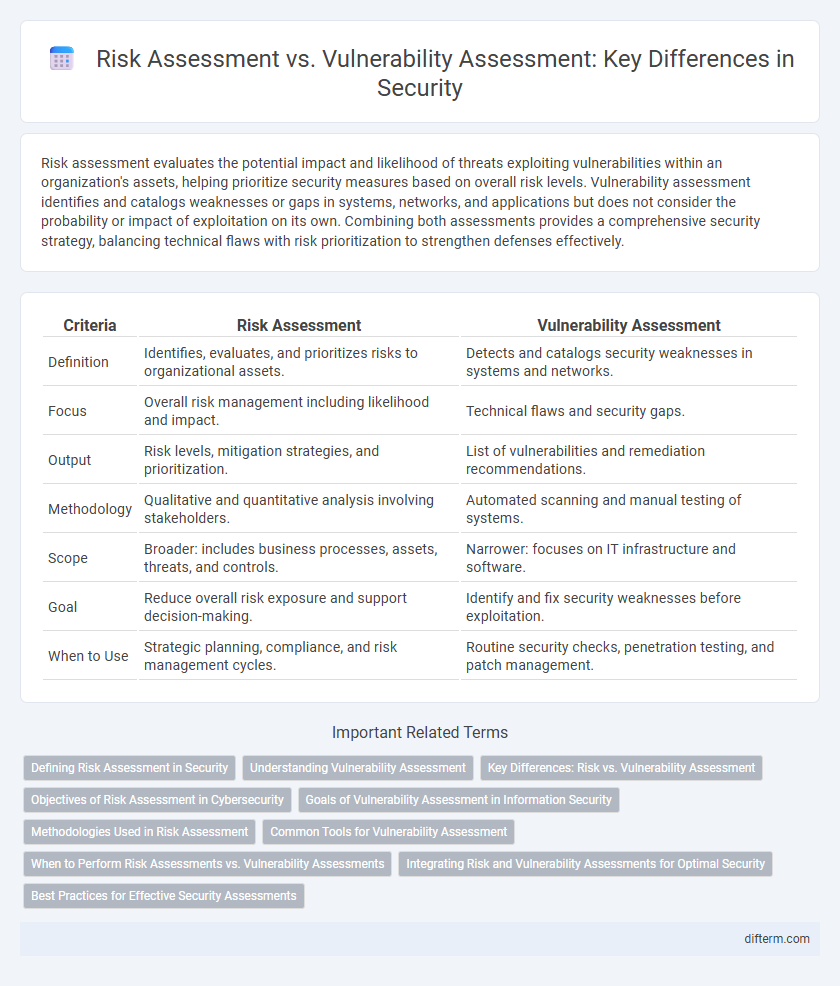
| Criteria | Risk Assessment | Vulnerability Assessment |
|---|---|---|
| Definition | Identifies, evaluates, and prioritizes risks to organizational assets. | Detects and catalogs security weaknesses in systems and networks. |
| Focus | Overall risk management including likelihood and impact. | Technical flaws and security gaps. |
| Output | Risk levels, mitigation strategies, and prioritization. | List of vulnerabilities and remediation recommendations. |
| Methodology | Qualitative and quantitative analysis involving stakeholders. | Automated scanning and manual testing of systems. |
| Scope | Broader: includes business processes, assets, threats, and controls. | Narrower: focuses on IT infrastructure and software. |
| Goal | Reduce overall risk exposure and support decision-making. | Identify and fix security weaknesses before exploitation. |
| When to Use | Strategic planning, compliance, and risk management cycles. | Routine security checks, penetration testing, and patch management. |
Defining Risk Assessment in Security
Risk assessment in security involves systematically identifying, evaluating, and prioritizing potential threats and their impacts on organizational assets. This process quantifies the likelihood and consequences of security incidents, guiding decision-makers in implementing appropriate controls to minimize risk exposure. Unlike vulnerability assessment, which focuses on discovering specific system weaknesses, risk assessment provides a broader analysis of overall security posture and potential business impact.
Understanding Vulnerability Assessment
Vulnerability Assessment systematically identifies, quantifies, and prioritizes security weaknesses within an organization's IT infrastructure, focusing on detecting potential points of exploitation before threats materialize. Tools like automated scanners, penetration testing, and configuration reviews are employed to uncover vulnerabilities in software, hardware, and network components. Understanding vulnerability assessment enables organizations to proactively implement remediation strategies and strengthen defenses against cyberattacks and data breaches.
Key Differences: Risk vs. Vulnerability Assessment
Risk assessment evaluates the likelihood and impact of potential security threats to prioritize mitigation efforts, focusing on the overall risk posed to an organization. Vulnerability assessment identifies and catalogs specific weaknesses in systems, applications, or networks that could be exploited by attackers. The key difference lies in risk assessment's emphasis on risk prioritization based on probability and impact, while vulnerability assessment concentrates on detecting security flaws without directly assessing their potential consequences.
Objectives of Risk Assessment in Cybersecurity
Risk assessment in cybersecurity focuses on identifying, evaluating, and prioritizing potential threats to an organization's information assets, enabling informed decision-making for risk mitigation strategies. It quantifies the likelihood and impact of cyber threats to determine acceptable risk levels and allocate resources effectively. The primary objective is to protect data confidentiality, integrity, and availability by addressing risks that could hinder business operations or cause financial loss.
Goals of Vulnerability Assessment in Information Security
Vulnerability Assessment in information security aims to identify, quantify, and prioritize vulnerabilities in systems, networks, and applications to prevent potential exploitation by attackers. It focuses on systematically scanning and analyzing security weaknesses such as misconfigurations, outdated software, and exposed services. The primary goal is to provide actionable insights that enable organizations to strengthen their security posture and reduce the risk of breaches.
Methodologies Used in Risk Assessment
Risk assessment methodologies primarily involve identifying assets, evaluating threats, and quantifying potential impacts to determine overall risk levels. Techniques such as qualitative analysis, quantitative analysis, and hybrid approaches help prioritize risks based on likelihood and consequences. Frameworks like NIST SP 800-30 and ISO 31000 guide structured processes for systematic risk evaluation and mitigation planning.
Common Tools for Vulnerability Assessment
Common tools for vulnerability assessment include Nessus, OpenVAS, and QualysGuard, which scan systems and networks for security weaknesses. These tools identify vulnerabilities such as outdated software, misconfigurations, and missing patches, helping organizations prioritize remediation efforts. Regular use of automated vulnerability scanners enhances the security posture by providing continuous monitoring and reporting of potential threats.
When to Perform Risk Assessments vs. Vulnerability Assessments
Perform risk assessments during the initial stages of security planning to identify potential threats, impacts, and prioritize controls based on business risk. Conduct vulnerability assessments more frequently, especially after system changes or security incidents, to detect and remediate specific security weaknesses or exposures. Combining regular vulnerability scans with periodic risk assessments ensures a comprehensive understanding of both risks and vulnerabilities within an organization's security posture.
Integrating Risk and Vulnerability Assessments for Optimal Security
Integrating risk assessment and vulnerability assessment enhances overall security by combining threat prioritization with identification of system weaknesses, allowing organizations to allocate resources efficiently and address the most critical vulnerabilities that pose real business risks. Risk assessment evaluates the likelihood and impact of threats against assets, while vulnerability assessment identifies technical flaws and exposures, making their integration essential for a comprehensive security posture. This combined approach supports proactive risk management, enabling targeted mitigation strategies that reduce potential attack surfaces and improve organizational resilience.
Best Practices for Effective Security Assessments
Risk assessment prioritizes identifying potential threats and their impact to allocate resources effectively, while vulnerability assessment focuses on detecting and evaluating security weaknesses within systems. Best practices for effective security assessments include combining both approaches regularly, leveraging automated tools for comprehensive scanning, and involving cross-functional teams to ensure a holistic view of organizational security posture. Maintaining up-to-date threat intelligence and continuous monitoring enhances the accuracy and relevance of assessment findings.
Risk Assessment vs Vulnerability Assessment Infographic
 difterm.com
difterm.com