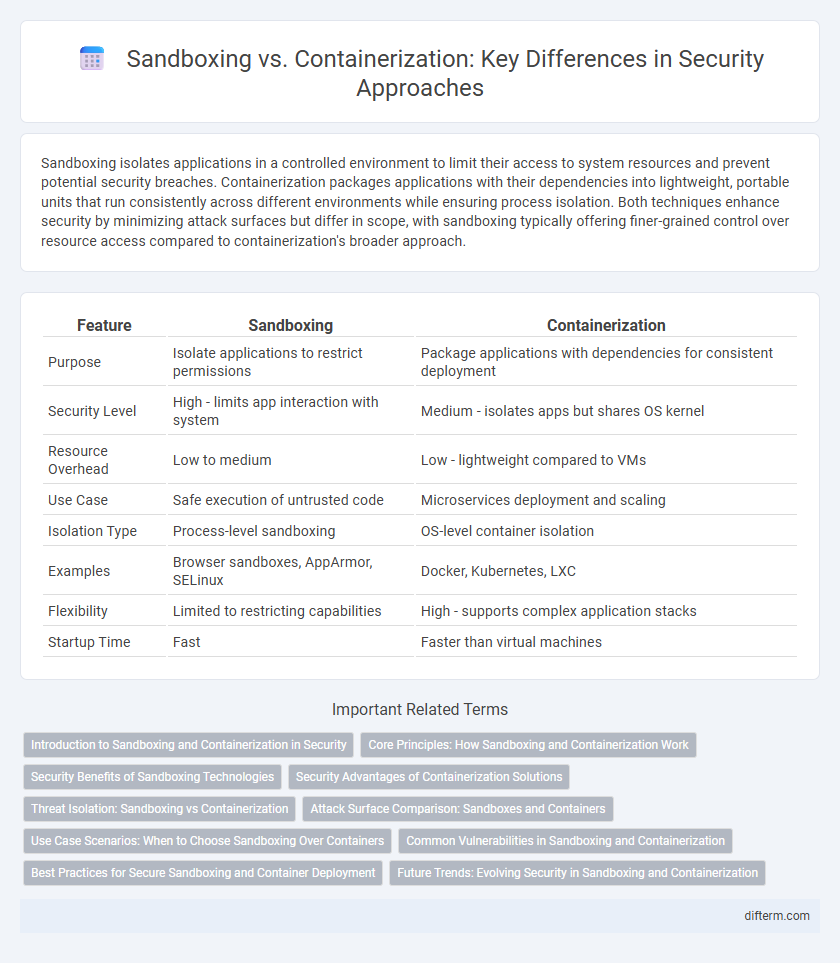
Sandboxing isolates applications in a controlled environment to limit their access to system resources and prevent potential security breaches. Containerization packages applications with their dependencies into lightweight, portable units that run consistently across different environments while ensuring process isolation. Both techniques enhance security by minimizing attack surfaces but differ in scope, with sandboxing typically offering finer-grained control over resource access compared to containerization's broader approach.
Table of Comparison
| Feature | Sandboxing | Containerization |
|---|---|---|
| Purpose | Isolate applications to restrict permissions | Package applications with dependencies for consistent deployment |
| Security Level | High - limits app interaction with system | Medium - isolates apps but shares OS kernel |
| Resource Overhead | Low to medium | Low - lightweight compared to VMs |
| Use Case | Safe execution of untrusted code | Microservices deployment and scaling |
| Isolation Type | Process-level sandboxing | OS-level container isolation |
| Examples | Browser sandboxes, AppArmor, SELinux | Docker, Kubernetes, LXC |
| Flexibility | Limited to restricting capabilities | High - supports complex application stacks |
| Startup Time | Fast | Faster than virtual machines |
Introduction to Sandboxing and Containerization in Security
Sandboxing isolates applications by creating virtual environments that restrict code execution and prevent malicious activity from affecting the host system. Containerization packages applications with their dependencies in lightweight, portable units that ensure consistent operation and enhance security through process isolation. Both technologies improve security posture by limiting attack surfaces and enabling controlled execution of untrusted code.
Core Principles: How Sandboxing and Containerization Work
Sandboxing isolates applications by running them in restricted environments with limited system access to minimize security risks and contain potential threats. Containerization packages applications and their dependencies into lightweight, portable units that share the host OS kernel but maintain isolated user spaces for consistent performance across environments. Both techniques rely on resource isolation and access control policies to enforce boundaries, though sandboxing emphasizes strict environment restrictions while containerization focuses on modular application deployment.
Security Benefits of Sandboxing Technologies
Sandboxing technologies enhance security by isolating applications and processes within controlled environments, preventing malicious code from affecting the host system. This containment limits the attack surface, mitigating risks of data breaches and unauthorized access. Sandboxing also enables safe testing of untrusted software, reducing the likelihood of system compromise in enterprise and development settings.
Security Advantages of Containerization Solutions
Containerization solutions provide enhanced security by isolating applications within lightweight, portable environments that share the host OS kernel without exposing it directly, reducing the attack surface compared to sandboxing techniques. Containers enforce stricter access controls and resource limitations through namespaces and cgroups, preventing unauthorized interactions and enhancing containment of potential security breaches. This approach also facilitates faster patching and consistent security updates across distributed systems, strengthening overall infrastructure resilience against vulnerabilities.
Threat Isolation: Sandboxing vs Containerization
Threat isolation in sandboxing involves running applications in restricted environments with limited access to the host system, preventing malicious code from affecting other processes or system components. Containerization provides process-level isolation by encapsulating applications and their dependencies in lightweight, portable units while sharing the host OS kernel, offering efficient but less strict isolation compared to sandboxing. Sandboxing typically offers stronger security boundaries against threats, whereas containerization balances isolation with performance and scalability.
Attack Surface Comparison: Sandboxes and Containers
Sandboxes provide a highly isolated environment by restricting application access to system resources, significantly reducing the attack surface through minimal permissions and strict control policies. Containers share the underlying host OS kernel, resulting in a larger attack surface due to kernel exploits and container escape vulnerabilities. Effective security requires assessing the trade-offs, as sandboxes offer stronger isolation while containers provide greater flexibility with a comparatively increased attack surface.
Use Case Scenarios: When to Choose Sandboxing Over Containers
Sandboxing excels in scenarios requiring strict isolation for running untrusted code or analyzing malware by containing potential threats within a controlled environment. It is ideal for secure browsing, application testing, and executing unknown scripts without risking the host system. Containers suit consistent deployment and microservices but lack the granular isolation needed for high-risk code execution, making sandboxing the preferred choice for security-critical use cases.
Common Vulnerabilities in Sandboxing and Containerization
Common vulnerabilities in sandboxing include escape attacks where malicious code breaks isolation, relying heavily on flawed policy enforcement and kernel exploits that undermine containment. Containerization faces risks from misconfigured namespaces, enabling privilege escalation, and shared kernel vulnerabilities that affect all containers on a host. Both techniques require rigorous security measures and regular patching to address inherent weaknesses and prevent breaches.
Best Practices for Secure Sandboxing and Container Deployment
Implement strict access controls and use minimal privilege principles to enhance secure sandboxing, isolating applications effectively from the host system. Employ container image scanning for vulnerabilities and enforce runtime security policies to maintain integrity during container deployment. Regularly update sandbox and container environments to patch security flaws and mitigate potential attack vectors.
Future Trends: Evolving Security in Sandboxing and Containerization
Future trends in sandboxing and containerization emphasize enhanced isolation techniques using lightweight virtualization and hardware-assisted security features to mitigate evolving cyber threats. Integration of AI-driven behavioral analysis improves real-time threat detection and response within containers and sandboxes, bolstering proactive defense mechanisms. Advances in orchestration platforms will enable seamless scalability and automated security compliance, ensuring robust protection in increasingly complex cloud-native environments.
Sandboxing vs Containerization Infographic
 difterm.com
difterm.com