A DMZ (Demilitarized Zone) is a separate network segment that isolates external-facing services from the internal network, minimizing the risk of internal exposure if compromised. A Bastion Host is a hardened server specifically designed to withstand attacks, often positioned on the edge of the network to provide controlled access to critical resources. Both enhance security by limiting direct access to internal systems, but the DMZ serves as a buffer zone while the Bastion Host acts as a fortified gateway.
Table of Comparison
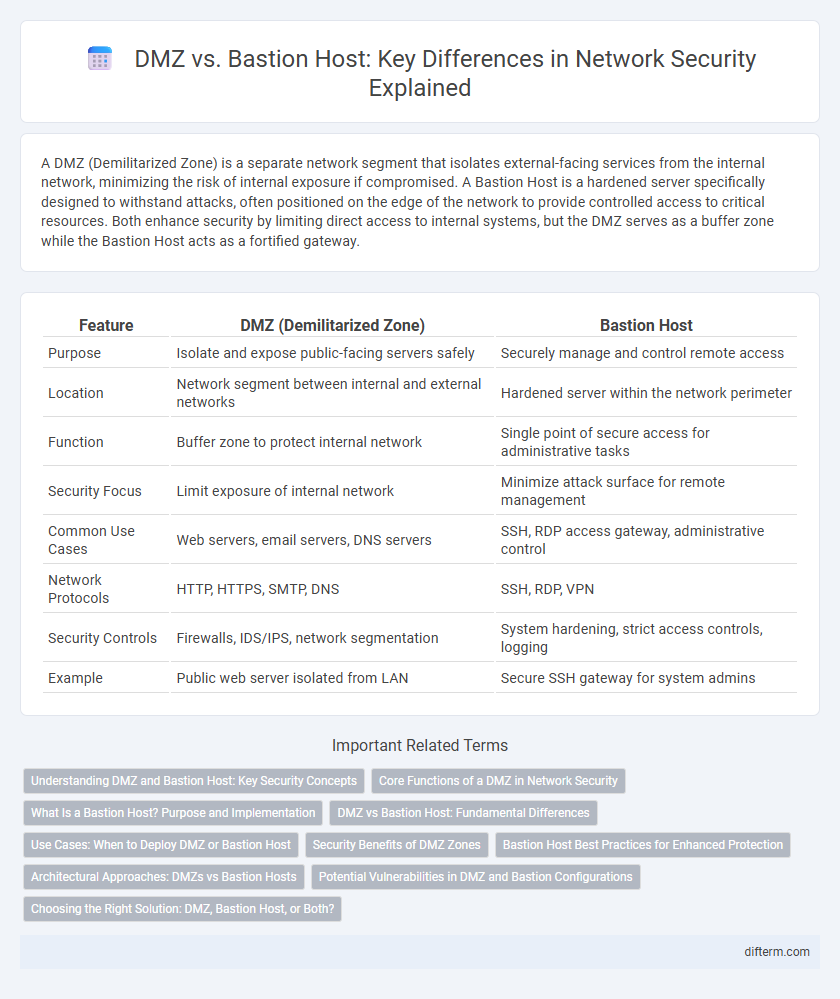
| Feature | DMZ (Demilitarized Zone) | Bastion Host |
|---|---|---|
| Purpose | Isolate and expose public-facing servers safely | Securely manage and control remote access |
| Location | Network segment between internal and external networks | Hardened server within the network perimeter |
| Function | Buffer zone to protect internal network | Single point of secure access for administrative tasks |
| Security Focus | Limit exposure of internal network | Minimize attack surface for remote management |
| Common Use Cases | Web servers, email servers, DNS servers | SSH, RDP access gateway, administrative control |
| Network Protocols | HTTP, HTTPS, SMTP, DNS | SSH, RDP, VPN |
| Security Controls | Firewalls, IDS/IPS, network segmentation | System hardening, strict access controls, logging |
| Example | Public web server isolated from LAN | Secure SSH gateway for system admins |
Understanding DMZ and Bastion Host: Key Security Concepts
A DMZ (Demilitarized Zone) is a network segment that acts as a buffer zone between an organization's internal network and untrusted external networks, hosting public-facing services while preventing direct access to internal systems. A Bastion Host is a highly fortified server located within the DMZ, designed to withstand attacks and control access to internal resources by providing a secure gateway for external traffic. Understanding the roles of DMZ and Bastion Hosts is essential for implementing layered security architectures that minimize attack surfaces and protect critical assets.
Core Functions of a DMZ in Network Security
A DMZ (Demilitarized Zone) functions as a critical buffer zone in network security, isolating internal networks from untrusted external access and limiting exposure to potential cyber threats. It hosts public-facing services such as web servers, mail servers, and DNS servers, ensuring that attackers cannot directly penetrate the internal network. By controlling incoming and outgoing traffic through firewalls, the DMZ enables secure communication between external users and hosted services while protecting sensitive internal systems.
What Is a Bastion Host? Purpose and Implementation
A bastion host is a specialized server designed to withstand attacks and provide a critical security checkpoint between an internal network and external threats, commonly deployed within a demilitarized zone (DMZ). Its primary purpose is to serve as a hardened gateway, allowing authorized access while minimizing vulnerabilities by limiting services and applying stringent security controls. Implementation involves configuring the bastion host with minimal software, robust firewalls, logging mechanisms, and strict access policies to protect sensitive internal systems from unauthorized or malicious external connections.
DMZ vs Bastion Host: Fundamental Differences
A DMZ (Demilitarized Zone) acts as a separate network segment designed to expose external-facing services while protecting the internal network from direct exposure. A bastion host is a specialized, hardened server placed within the DMZ or another network segment to withstand attacks and provide controlled access to critical resources. Unlike a DMZ that functions as a buffer zone containing multiple systems, a bastion host represents a single fortified point of defense with strict security configurations.
Use Cases: When to Deploy DMZ or Bastion Host
A DMZ is ideal for organizations needing to expose multiple public-facing services like web servers and email gateways while maintaining a strict separation from the internal network to mitigate risks. Bastion hosts are best deployed for secure access scenarios where a single hardened device provides controlled entry points, typically for remote administrative access or SSH gateways. Deploying a DMZ suits environments with diverse external interfaces, whereas bastion hosts fit targeted security needs for critical access control.
Security Benefits of DMZ Zones
DMZ zones enhance network security by isolating external-facing services from the internal network, reducing the attack surface and limiting the exposure of critical assets. They enable stringent access control policies and monitoring, preventing direct access to sensitive systems while allowing controlled interaction with public networks. This segmentation minimizes the risk of lateral movement by attackers, safeguarding internal resources more effectively than a single bastion host setup.
Bastion Host Best Practices for Enhanced Protection
Implementing bastion host best practices involves deploying hardened systems with minimal services to reduce attack surfaces and applying strict access controls through multi-factor authentication and IP whitelisting. Regular patching and continuous monitoring using intrusion detection systems ensure vulnerabilities are addressed promptly while suspicious activities are identified early. Segregating bastion hosts within isolated network segments and enforcing encrypted connections like SSH further strengthens protection against unauthorized access and lateral movement.
Architectural Approaches: DMZs vs Bastion Hosts
DMZs (Demilitarized Zones) create a segregated network layer between internal networks and untrusted external sources, enabling controlled access to public-facing services while protecting internal assets. Bastion hosts function as a hardened gateway server exposed to the internet, specifically designed to withstand attacks and filter traffic before reaching internal systems. Architectural approaches differ as DMZs rely on network segmentation and multiple devices for layered defense, whereas bastion hosts focus on securing a single point of entry with robust configuration and strict access controls.
Potential Vulnerabilities in DMZ and Bastion Configurations
Potential vulnerabilities in DMZ configurations include exposure to external threats due to multiple services hosted in the zone, making it a prime target for attackers aiming to breach internal networks. Bastion hosts, while hardened and focused on a single or limited set of services, may become single points of failure if not properly maintained or updated, leading to escalated risks in case of compromise. Both configurations require rigorous access controls, regular patching, and continuous monitoring to mitigate risks associated with unpatched vulnerabilities and misconfigurations.
Choosing the Right Solution: DMZ, Bastion Host, or Both?
Choosing the right security architecture depends on the specific network requirements and threat landscape; a DMZ (Demilitarized Zone) provides a segregated subnetwork to isolate external-facing services, while a Bastion Host serves as a fortified gateway controlling access between internal and external networks. Implementing both a DMZ and Bastion Host can enhance defense in depth by combining perimeter isolation with hardened access points, but this requires more complex configuration and maintenance. Evaluating risks, performance needs, and administrative capabilities is crucial to determine whether a DMZ, Bastion Host, or an integrated approach best mitigates vulnerabilities and protects critical assets.
DMZ vs Bastion Host Infographic
 difterm.com
difterm.com