Forward Secrecy ensures that session keys cannot be compromised even if the server's private key is exposed later, protecting past communications from decryption. Perfect Forward Secrecy (PFS) takes this further by generating unique session keys for each session without relying on long-term keys, enhancing security in encrypted pet monitoring systems. Implementing PFS in security pet devices strengthens privacy by preventing attackers from accessing historical data even if the device is compromised.
Table of Comparison
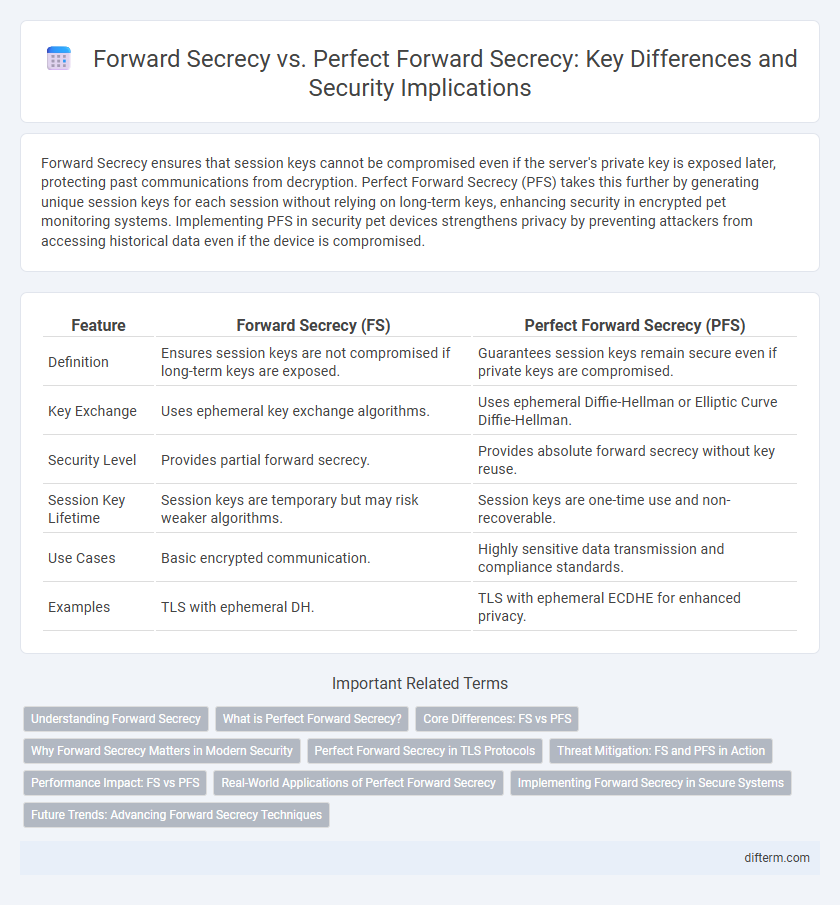
| Feature | Forward Secrecy (FS) | Perfect Forward Secrecy (PFS) |
|---|---|---|
| Definition | Ensures session keys are not compromised if long-term keys are exposed. | Guarantees session keys remain secure even if private keys are compromised. |
| Key Exchange | Uses ephemeral key exchange algorithms. | Uses ephemeral Diffie-Hellman or Elliptic Curve Diffie-Hellman. |
| Security Level | Provides partial forward secrecy. | Provides absolute forward secrecy without key reuse. |
| Session Key Lifetime | Session keys are temporary but may risk weaker algorithms. | Session keys are one-time use and non-recoverable. |
| Use Cases | Basic encrypted communication. | Highly sensitive data transmission and compliance standards. |
| Examples | TLS with ephemeral DH. | TLS with ephemeral ECDHE for enhanced privacy. |
Understanding Forward Secrecy
Forward Secrecy ensures that session keys remain secure even if the server's long-term private key is compromised, preventing past communications from being decrypted retroactively. It achieves this by generating unique, ephemeral session keys for each communication session, which are not stored or reused. Understanding Forward Secrecy is crucial for enhancing data confidentiality in secure protocols such as TLS and HTTPS, particularly in environments vulnerable to key exposure.
What is Perfect Forward Secrecy?
Perfect Forward Secrecy (PFS) is a cryptographic property ensuring that session keys remain secure even if the server's private key is compromised in the future. By generating unique ephemeral session keys for each communication, PFS prevents attackers from decrypting past sessions retrospectively. This technique is commonly implemented using Diffie-Hellman or Elliptic Curve Diffie-Hellman key exchanges to enhance data confidentiality in TLS protocols.
Core Differences: FS vs PFS
Forward Secrecy (FS) ensures that session keys cannot be derived from long-term keys, protecting past communications if a private key is compromised. Perfect Forward Secrecy (PFS) extends this by generating unique session keys that are never stored or reused, guaranteeing that even if current keys are exposed, previous sessions remain secure. The core difference lies in PFS's strict elimination of key reuse and storage, providing stronger safeguards against retrospective decryption compared to standard FS.
Why Forward Secrecy Matters in Modern Security
Forward Secrecy (FS) ensures that session keys remain secure even if long-term keys are compromised, preventing attackers from decrypting past communications. This property is critical in modern security because it limits the damage of data breaches and enhances privacy against mass surveillance and future cryptographic attacks. Implementing Forward Secrecy in protocols like TLS significantly improves resilience by safeguarding historical data confidentiality.
Perfect Forward Secrecy in TLS Protocols
Perfect Forward Secrecy (PFS) in TLS protocols ensures that session keys cannot be compromised even if the server's long-term private key is exposed, enhancing security during encrypted communications. PFS uses ephemeral key exchanges, such as Diffie-Hellman Ephemeral (DHE) or Elliptic Curve Diffie-Hellman Ephemeral (ECDHE), to generate unique session keys for each connection. Implementing PFS mitigates risks of retrospective data decryption and is essential for maintaining confidentiality in modern security architectures.
Threat Mitigation: FS and PFS in Action
Forward Secrecy (FS) ensures that session keys are not compromised if long-term keys are exposed, reducing the risk of decrypted past communications. Perfect Forward Secrecy (PFS) enhances this by generating unique ephemeral keys for every session, making it impossible to decrypt previous sessions even if current keys are compromised. Both FS and PFS mitigate threats by minimizing the impact of key leakage on historical data confidentiality in secure communications.
Performance Impact: FS vs PFS
Forward Secrecy (FS) and Perfect Forward Secrecy (PFS) both enhance security by ensuring session key protection against future key compromises, but PFS offers a stronger guarantee by generating unique session keys independent of the server's long-term private key. The performance impact of PFS is generally higher than FS due to its reliance on more complex key exchange mechanisms like Diffie-Hellman ephemeral (DHE) or Elliptic Curve Diffie-Hellman ephemeral (ECDHE), which require additional computational resources. Despite the increased overhead, modern hardware and optimized implementations minimize latency, making PFS viable for high-security environments without significant performance degradation.
Real-World Applications of Perfect Forward Secrecy
Perfect Forward Secrecy (PFS) ensures that session keys cannot be compromised even if the server's long-term private key is exposed, making it essential for secure communications in real-world applications such as HTTPS, VPNs, and messaging platforms like Signal and WhatsApp. Unlike general forward secrecy, PFS employs ephemeral key exchanges, typically using protocols like Diffie-Hellman or Elliptic Curve Diffie-Hellman, which create unique session keys that are never reused. This cryptographic guarantee protects sensitive user data and maintains privacy against future key compromises in critical security infrastructures.
Implementing Forward Secrecy in Secure Systems
Implementing Forward Secrecy in secure systems ensures that session keys are not compromised even if long-term private keys are exposed, enhancing confidentiality in encrypted communications. Perfect Forward Secrecy (PFS) is a stricter standard where every session key is ephemeral and independently generated, preventing decryption of past sessions if current keys are compromised. Utilizing key exchange protocols like Diffie-Hellman Ephemeral (DHE) or Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) supports Forward Secrecy by generating temporary keys for each session, reinforcing data security against future attacks.
Future Trends: Advancing Forward Secrecy Techniques
Future trends in advancing Forward Secrecy techniques emphasize integrating quantum-resistant algorithms to safeguard encrypted communications against emerging computational threats. Enhanced cryptographic protocols are being developed to ensure that session keys remain secure even if long-term keys are compromised, reinforcing Perfect Forward Secrecy (PFS) standards. Adoption of hybrid encryption models combining classical and post-quantum cryptographic methods is expected to dominate next-generation secure communication frameworks.
Forward Secrecy vs Perfect Forward Secrecy Infographic
 difterm.com
difterm.com