Remediation involves identifying and fixing security vulnerabilities to eliminate threats permanently, whereas mitigation focuses on reducing the impact of potential security incidents without resolving the underlying issue. Effective security strategies prioritize remediation to address root causes, while mitigation serves as a tactical response to minimize damage during active threats. Balancing both approaches ensures comprehensive protection for security pets and their data.
Table of Comparison
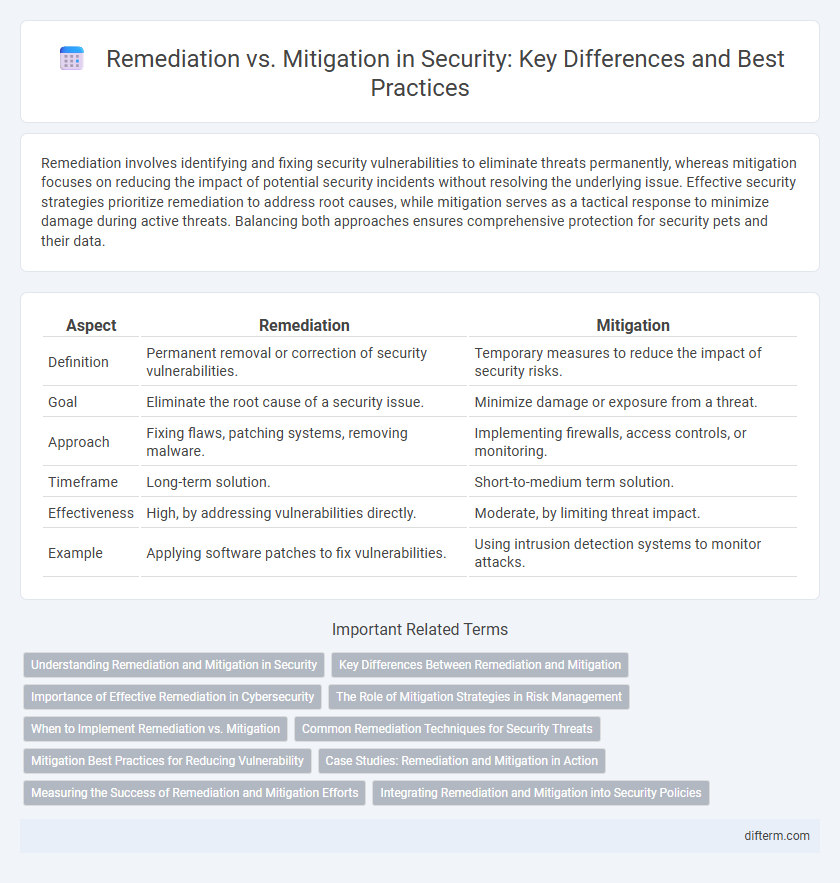
| Aspect | Remediation | Mitigation |
|---|---|---|
| Definition | Permanent removal or correction of security vulnerabilities. | Temporary measures to reduce the impact of security risks. |
| Goal | Eliminate the root cause of a security issue. | Minimize damage or exposure from a threat. |
| Approach | Fixing flaws, patching systems, removing malware. | Implementing firewalls, access controls, or monitoring. |
| Timeframe | Long-term solution. | Short-to-medium term solution. |
| Effectiveness | High, by addressing vulnerabilities directly. | Moderate, by limiting threat impact. |
| Example | Applying software patches to fix vulnerabilities. | Using intrusion detection systems to monitor attacks. |
Understanding Remediation and Mitigation in Security
Remediation in security involves identifying, addressing, and eliminating vulnerabilities or threats to restore systems to a secure state, ensuring long-term protection. Mitigation focuses on reducing the impact or likelihood of security incidents without necessarily resolving the root cause, often through temporary controls or safeguards. Understanding the distinction between remediation and mitigation is crucial for developing effective security strategies that balance immediate risk reduction with permanent solutions.
Key Differences Between Remediation and Mitigation
Remediation involves identifying and fixing vulnerabilities to eliminate security risks, while mitigation focuses on reducing the impact or likelihood of a threat without fully resolving the underlying issue. Remediation typically requires patching software or updating configurations, whereas mitigation employs controls like firewalls, access restrictions, or temporary workarounds. The key difference lies in remediation's goal to permanently remove risks, contrasting with mitigation's aim to minimize damage or exposure when immediate fixes are not feasible.
Importance of Effective Remediation in Cybersecurity
Effective remediation in cybersecurity addresses the root cause of security vulnerabilities, preventing recurrence and minimizing long-term risk exposure. Unlike mitigation, which only reduces the immediate impact of threats, remediation ensures comprehensive resolution through system patches, configuration updates, and removal of malicious artifacts. Prioritizing remediation strengthens overall security posture, enhancing resilience against future cyberattacks and reducing potential damage and recovery costs.
The Role of Mitigation Strategies in Risk Management
Mitigation strategies play a critical role in risk management by reducing the potential impact and likelihood of security threats without completely eliminating the underlying vulnerabilities. These strategies include implementing firewalls, intrusion detection systems, and regular patch management to minimize damage during a cyberattack. Effective mitigation ensures continuous protection and operational resilience while remediation addresses the root cause after an incident occurs.
When to Implement Remediation vs. Mitigation
Implement remediation when vulnerabilities can be fully resolved to eliminate security risks, such as patching software bugs or removing malicious code. Opt for mitigation strategies in scenarios requiring immediate risk reduction where full remediation is not yet feasible, like implementing firewall rules or network segmentation to limit threat exposure. Prioritize remediation for long-term security, while mitigation provides temporary protection during incident response or resource constraints.
Common Remediation Techniques for Security Threats
Common remediation techniques for security threats include patch management, which involves regularly updating software to fix vulnerabilities, and incident response procedures designed to identify, contain, and eradicate threats quickly. Implementing robust access controls and multi-factor authentication reduces the risk of unauthorized access as part of the remediation process. Data backup and recovery plans ensure business continuity by restoring systems affected by security breaches, effectively addressing the root causes rather than just the symptoms.
Mitigation Best Practices for Reducing Vulnerability
Mitigation best practices for reducing vulnerability include implementing multi-layered security controls such as firewalls, intrusion detection systems, and regular patch management to minimize attack surfaces. Employing network segmentation, strong access controls, and continuous monitoring helps detect and contain threats early, reducing potential damage. Educating employees on cybersecurity awareness and enforcing strict security policies further strengthens defenses against exploitation.
Case Studies: Remediation and Mitigation in Action
Case studies in cybersecurity highlight the distinct roles of remediation and mitigation in managing threats effectively. Remediation involves identifying vulnerabilities, eradicating threats, and restoring affected systems to their secure state, as demonstrated in the Equifax 2017 data breach response where comprehensive patching and system updates were implemented. Mitigation efforts focus on reducing impact and exposure, exemplified by the 2013 Target breach where improved network segmentation and enhanced monitoring limited the attack's scope and prevented further damage.
Measuring the Success of Remediation and Mitigation Efforts
Measuring the success of remediation efforts involves tracking the complete resolution of vulnerabilities and ensuring that security gaps are fully closed through validated patching or configuration changes. Mitigation success is evaluated by assessing the reduction in risk exposure and the effectiveness of controls in minimizing the impact of potential threats without necessarily eliminating the root cause. Key performance indicators (KPIs) such as time to remediate, incident recurrence rates, and residual risk levels provide quantifiable metrics to gauge the effectiveness of both remediation and mitigation strategies.
Integrating Remediation and Mitigation into Security Policies
Integrating remediation and mitigation into security policies ensures a comprehensive approach to threat management by addressing vulnerabilities and reducing risk exposure simultaneously. Remediation focuses on eliminating the root cause of security issues, while mitigation minimizes potential damage when immediate resolution is not feasible. Embedding both strategies into security frameworks enhances organizational resilience and compliance with industry standards such as NIST and ISO 27001.
Remediation vs Mitigation Infographic
 difterm.com
difterm.com