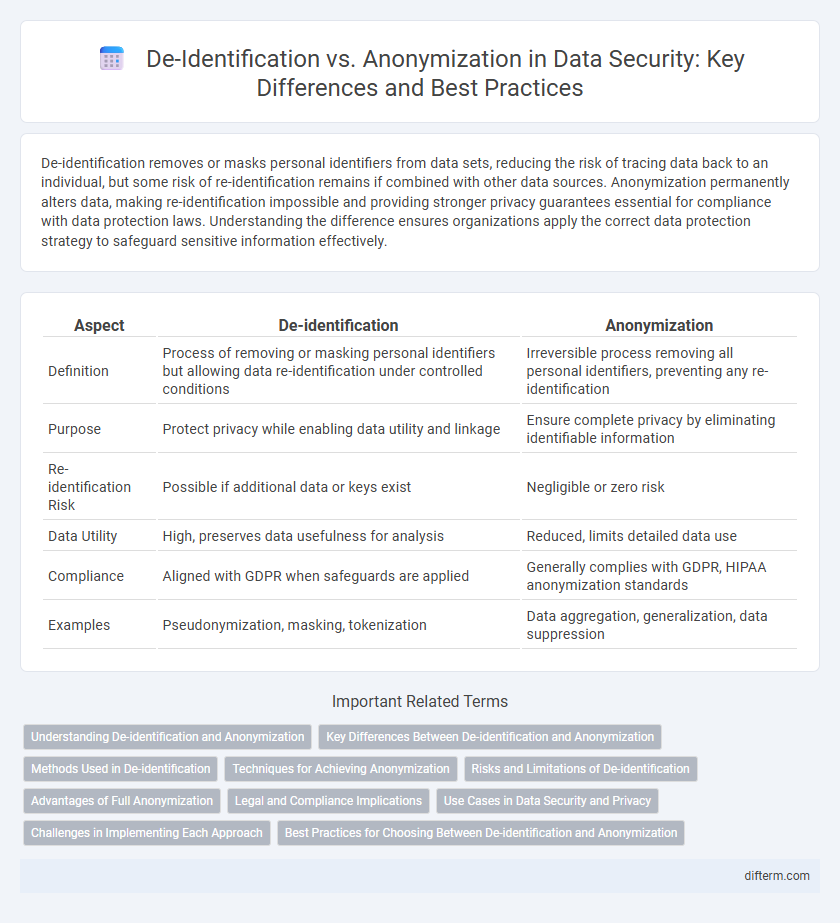
De-identification removes or masks personal identifiers from data sets, reducing the risk of tracing data back to an individual, but some risk of re-identification remains if combined with other data sources. Anonymization permanently alters data, making re-identification impossible and providing stronger privacy guarantees essential for compliance with data protection laws. Understanding the difference ensures organizations apply the correct data protection strategy to safeguard sensitive information effectively.
Table of Comparison
| Aspect | De-identification | Anonymization |
|---|---|---|
| Definition | Process of removing or masking personal identifiers but allowing data re-identification under controlled conditions | Irreversible process removing all personal identifiers, preventing any re-identification |
| Purpose | Protect privacy while enabling data utility and linkage | Ensure complete privacy by eliminating identifiable information |
| Re-identification Risk | Possible if additional data or keys exist | Negligible or zero risk |
| Data Utility | High, preserves data usefulness for analysis | Reduced, limits detailed data use |
| Compliance | Aligned with GDPR when safeguards are applied | Generally complies with GDPR, HIPAA anonymization standards |
| Examples | Pseudonymization, masking, tokenization | Data aggregation, generalization, data suppression |
Understanding De-identification and Anonymization
De-identification involves removing or masking personal identifiers from data sets to reduce the risk of identifying individuals, while anonymization permanently eliminates all identifying information to ensure data cannot be traced back to an individual. Effective de-identification strategies include techniques like pseudonymization, data masking, and generalization, whereas anonymization requires irreversible processes such as data aggregation or suppression. Understanding these distinctions is critical for compliance with data protection regulations like GDPR and HIPAA, balancing data utility with privacy protection.
Key Differences Between De-identification and Anonymization
De-identification involves removing or masking personal identifiers from data to reduce the risk of re-identification, while anonymization permanently eliminates all identifiable information, making re-identification impossible. De-identified data can sometimes be re-linked to individuals through additional information, but anonymized data lacks any link back to the original subject. The key distinction lies in the reversibility of identity removal--de-identification is reversible under certain conditions, whereas anonymization ensures irreversible data transformation.
Methods Used in De-identification
De-identification methods primarily involve data masking, pseudonymization, and generalization to protect personal information while preserving data utility. Techniques such as tokenization replace sensitive data with unique identifiers that can be reversed under controlled conditions, enhancing security for re-identification when necessary. Aggregation and suppression further reduce the risk of identity disclosure by eliminating or modifying identifiable attributes within datasets.
Techniques for Achieving Anonymization
Techniques for achieving anonymization include data masking, generalization, and suppression, each reducing the risk of re-identification by altering or removing personally identifiable information. Differential privacy introduces statistical noise to datasets, ensuring individual data points remain indistinguishable while preserving overall data utility. K-anonymity groups data entries to make each individual indistinguishable from at least k-1 others, enhancing privacy protection in large datasets.
Risks and Limitations of De-identification
De-identification reduces the risk of personal data exposure by removing identifiers but remains vulnerable to re-identification attacks when combined with auxiliary data sources. Risks include residual data linkability, incomplete removal of indirect identifiers, and insufficient data transformation techniques. Limitations also arise from evolving data mining methods and the potential compromise of de-identified datasets through advanced analytics or cross-referencing databases.
Advantages of Full Anonymization
Full anonymization ensures robust data privacy by irreversibly removing personally identifiable information, significantly reducing the risk of re-identification in security breaches. It enhances compliance with stringent data protection regulations such as GDPR and HIPAA by eliminating the need for ongoing data safeguarding measures. Organizations benefit from increased trust and reduced liability, enabling safer data sharing and analytics without compromising individual privacy.
Legal and Compliance Implications
De-identification reduces data linkage risks by removing direct identifiers while potentially allowing re-identification under specific conditions, impacting compliance with regulations like HIPAA and GDPR. Anonymization ensures irreversible data transformation, minimizing legal liabilities but limiting data utility for analytical purposes under frameworks such as the EU GDPR's Recital 26. Organizations must evaluate the balance between data protection standards and operational needs to align with jurisdiction-specific data privacy laws and maintain regulatory compliance.
Use Cases in Data Security and Privacy
De-identification and anonymization both enhance data security by reducing personal identifier risks, but differ in use cases: de-identification is suited for controlled environments where data can be re-identified under strict protocols, important in healthcare research for patient follow-ups, while anonymization is ideal for public data releases, ensuring irreversible data protection in compliance with privacy regulations like GDPR. Organizations implement de-identification to balance data usability and privacy, enabling analytical insights without exposing identities. In contrast, anonymization is applied when data sharing requires maximum privacy, preventing re-identification to protect individual rights in open datasets or third-party collaborations.
Challenges in Implementing Each Approach
Implementing de-identification challenges include balancing data utility with privacy risk, as improperly masked identifiers can lead to re-identification threats in datasets. Anonymization faces difficulties in ensuring irreversible data transformation while maintaining dataset accuracy for analytics, often requiring complex algorithms like k-anonymity or differential privacy. Both approaches demand rigorous compliance with regulations such as GDPR and HIPAA to avoid legal vulnerabilities and protect sensitive information effectively.
Best Practices for Choosing Between De-identification and Anonymization
Choosing between de-identification and anonymization depends on the intended use, data sensitivity, and compliance requirements. De-identification allows data to retain some utility by masking personal identifiers while preserving data linkability under strict controls, making it ideal for internal research and analytics. Anonymization ensures irreversible removal of identifiable information, offering stronger privacy protection suitable for public data releases and compliance with regulations like GDPR and HIPAA.
De-identification vs Anonymization Infographic
 difterm.com
difterm.com