Mandatory Access Control (MAC) enforces strict security policies based on predefined rules set by an administrator, preventing users from altering access permissions, which enhances protection in sensitive environments. Discretionary Access Control (DAC) allows users to control access to their own resources by granting permissions, offering flexibility but increased risk of unauthorized access. Choosing between MAC and DAC depends on the required security level and the need for user autonomy in managing resource permissions.
Table of Comparison
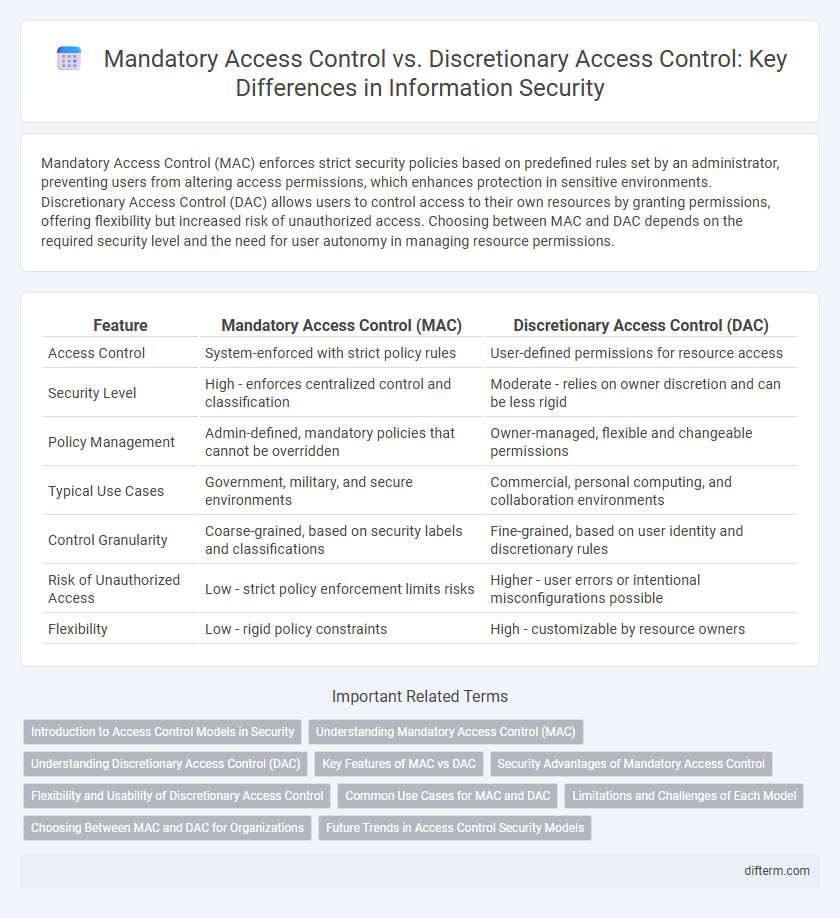
| Feature | Mandatory Access Control (MAC) | Discretionary Access Control (DAC) |
|---|---|---|
| Access Control | System-enforced with strict policy rules | User-defined permissions for resource access |
| Security Level | High - enforces centralized control and classification | Moderate - relies on owner discretion and can be less rigid |
| Policy Management | Admin-defined, mandatory policies that cannot be overridden | Owner-managed, flexible and changeable permissions |
| Typical Use Cases | Government, military, and secure environments | Commercial, personal computing, and collaboration environments |
| Control Granularity | Coarse-grained, based on security labels and classifications | Fine-grained, based on user identity and discretionary rules |
| Risk of Unauthorized Access | Low - strict policy enforcement limits risks | Higher - user errors or intentional misconfigurations possible |
| Flexibility | Low - rigid policy constraints | High - customizable by resource owners |
Introduction to Access Control Models in Security
Mandatory Access Control (MAC) enforces access policies based on fixed security labels assigned by a central authority, ensuring strict regulation of resources according to predefined classifications. Discretionary Access Control (DAC) allows resource owners to determine access permissions, providing more flexibility but increased risk of unauthorized access. Both models serve critical roles in securing systems by defining how users and processes gain authorization to sensitive information and resources.
Understanding Mandatory Access Control (MAC)
Mandatory Access Control (MAC) enforces strict security policies by assigning access rights based on fixed classifications and labels, preventing users from altering permissions. This model ensures that access decisions are governed by a central authority, which dictates permissions according to predetermined rules, enhancing protection in high-security environments. MAC is commonly used in government and military systems where data sensitivity and compliance require rigid enforcement of access controls.
Understanding Discretionary Access Control (DAC)
Discretionary Access Control (DAC) grants resource owners the ability to determine access permissions, enabling flexible and user-driven security management. Unlike Mandatory Access Control (MAC), DAC policies allow individual users to control access to their files, which can lead to varied permission settings based on user discretion. This model is commonly implemented in operating systems where owners can share resources by assigning read, write, or execute privileges to other users.
Key Features of MAC vs DAC
Mandatory Access Control (MAC) enforces policy-driven access restrictions based on defined security labels and classifications, ensuring users cannot alter access permissions. Discretionary Access Control (DAC) allows resource owners to grant or revoke access at their discretion, offering flexibility but increasing risk of unauthorized access. Key features of MAC include strict policy enforcement and centralized control, while DAC is characterized by user autonomy and decentralized permission management.
Security Advantages of Mandatory Access Control
Mandatory Access Control (MAC) enforces strict security policies by restricting access based on fixed rules defined by system administrators, significantly reducing the risk of unauthorized data exposure. Unlike Discretionary Access Control (DAC), MAC prevents users from altering access permissions, enhancing protection against insider threats and accidental data leaks. The inherent rigidity of MAC ensures consistent enforcement of security classifications, making it ideal for environments with high confidentiality requirements such as government and military systems.
Flexibility and Usability of Discretionary Access Control
Discretionary Access Control (DAC) offers greater flexibility by allowing users to define and modify access permissions for resources they own, unlike Mandatory Access Control (MAC) which enforces strict, system-wide policies. This user-centric model enhances usability by enabling tailored access management based on individual needs and collaborative environments. However, the inherent flexibility of DAC can lead to increased security risks if users misconfigure permissions or lack awareness of best practices.
Common Use Cases for MAC and DAC
Mandatory Access Control (MAC) is commonly used in high-security environments such as government and military organizations where strict data confidentiality and integrity are crucial, enforcing policies that prevent unauthorized data access based on predefined security levels. Discretionary Access Control (DAC) is frequently applied in commercial and enterprise settings, allowing users to control access to their own data and share resources flexibly, making it ideal for collaboration and dynamic work environments. Both MAC and DAC provide essential frameworks for access management, with MAC prioritizing rigid enforcement and DAC offering user-level flexibility in protecting sensitive information.
Limitations and Challenges of Each Model
Mandatory Access Control (MAC) presents challenges such as inflexibility, as it strictly enforces policies that cannot be altered by users or owners, leading to potential operational bottlenecks in dynamic environments. Discretionary Access Control (DAC) faces limitations in security due to its reliance on users to manage permissions, increasing the risk of accidental or malicious access breaches. Both models struggle with scalability and fine-grained control in complex systems, requiring careful implementation to balance security and usability.
Choosing Between MAC and DAC for Organizations
Organizations selecting between Mandatory Access Control (MAC) and Discretionary Access Control (DAC) must consider security requirements and operational flexibility. MAC enforces strict, centrally managed policies ideal for high-security environments, preventing users from altering access permissions. DAC allows owners to control access, offering greater adaptability but potentially increasing vulnerability risks due to user discretion.
Future Trends in Access Control Security Models
Mandatory Access Control (MAC) is expected to integrate more artificial intelligence and machine learning algorithms to enhance automated policy enforcement and anomaly detection, significantly improving security in dynamic environments. Discretionary Access Control (DAC) models will evolve to incorporate blockchain technology for decentralized permission management, increasing transparency and reducing insider threat risks. Future access control security models will emphasize hybrid approaches combining MAC's strict policy controls with DAC's flexibility, optimizing both security and usability across cloud and IoT infrastructures.
Mandatory Access Control vs Discretionary Access Control Infographic
 difterm.com
difterm.com