Zero-day exploits target previously unknown vulnerabilities, leaving systems defenseless until patches are developed. Known exploits take advantage of vulnerabilities with available fixes, making timely updates critical for protection. Effective security strategies prioritize rapid patch management and threat intelligence to minimize risks from both types of exploits.
Table of Comparison
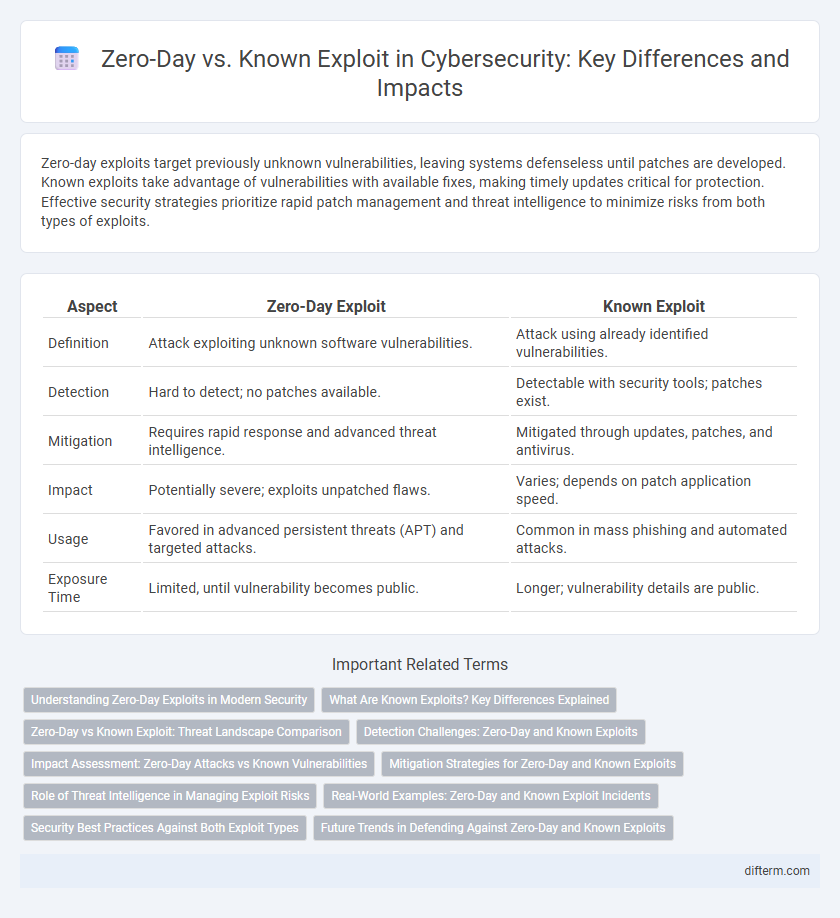
| Aspect | Zero-Day Exploit | Known Exploit |
|---|---|---|
| Definition | Attack exploiting unknown software vulnerabilities. | Attack using already identified vulnerabilities. |
| Detection | Hard to detect; no patches available. | Detectable with security tools; patches exist. |
| Mitigation | Requires rapid response and advanced threat intelligence. | Mitigated through updates, patches, and antivirus. |
| Impact | Potentially severe; exploits unpatched flaws. | Varies; depends on patch application speed. |
| Usage | Favored in advanced persistent threats (APT) and targeted attacks. | Common in mass phishing and automated attacks. |
| Exposure Time | Limited, until vulnerability becomes public. | Longer; vulnerability details are public. |
Understanding Zero-Day Exploits in Modern Security
Zero-day exploits target undisclosed software vulnerabilities unknown to developers and security teams, making detection and defense extremely challenging in modern security environments. These exploits are highly valuable for attackers as they can bypass traditional security measures before patches or updates are released. Understanding the lifecycle and indicators of zero-day attacks is crucial for developing proactive threat intelligence and adaptive cybersecurity strategies.
What Are Known Exploits? Key Differences Explained
Known exploits refer to security vulnerabilities that have been identified, documented, and publicly disclosed, allowing organizations to develop and implement patches or mitigations. Unlike zero-day exploits, which are unknown to vendors and have no immediate fixes, known exploits pose a risk primarily when systems remain unpatched or outdated. Understanding the distinction helps prioritize vulnerability management and cybersecurity defenses to reduce exposure to exploitation.
Zero-Day vs Known Exploit: Threat Landscape Comparison
Zero-day exploits pose a higher security risk than known exploits due to their undisclosed nature, allowing attackers to breach systems before patches are developed. Known exploits target vulnerabilities with publicly available information, enabling faster detection and remediation by security teams. The threat landscape shows zero-day attacks often result in more severe damage and longer exposure times compared to known exploits, highlighting the critical need for proactive threat intelligence and behavior-based anomaly detection.
Detection Challenges: Zero-Day and Known Exploits
Zero-day exploits pose significant detection challenges due to their unknown nature and absence of signature-based identifiers, making traditional security tools ineffective. Known exploits benefit from established detection patterns and threat intelligence, allowing for quicker identification and remediation. Security teams must leverage behavior-based analysis and real-time monitoring to address the stealth and unpredictability of zero-day vulnerabilities.
Impact Assessment: Zero-Day Attacks vs Known Vulnerabilities
Zero-day attacks pose a greater risk due to the absence of available patches, allowing attackers to exploit vulnerabilities before detection and mitigation. In contrast, known vulnerabilities have documented exploits and established remediation strategies, reducing their impact when addressed promptly. Effective impact assessment prioritizes identifying zero-day threats for immediate response while maintaining vigilance on known vulnerabilities through timely updates and security controls.
Mitigation Strategies for Zero-Day and Known Exploits
Mitigation strategies for zero-day exploits emphasize proactive threat hunting, real-time behavioral analysis, and endpoint detection and response (EDR) systems due to the absence of known signatures. Known exploits benefit from signature-based antivirus updates, patch management, and vulnerability scanning to close identified security gaps. Organizations should integrate both approaches, combining automated patching and threat intelligence feeds with advanced anomaly detection to enhance overall cyber resilience.
Role of Threat Intelligence in Managing Exploit Risks
Threat intelligence plays a crucial role in managing risks associated with zero-day and known exploits by providing timely data on emerging vulnerabilities and attack patterns. It enhances proactive defense strategies through continuous monitoring, enabling rapid identification and mitigation before exploits cause significant damage. Leveraging enriched threat intelligence feeds helps organizations prioritize patching and implement tailored security measures to minimize exploit-driven breaches.
Real-World Examples: Zero-Day and Known Exploit Incidents
The 2017 Equifax breach exploited a known vulnerability in Apache Struts, demonstrating the severe impact of failing to patch known exploits promptly. In contrast, the Stuxnet worm leveraged multiple zero-day vulnerabilities to sabotage Iran's nuclear program, illustrating the stealth and sophistication of zero-day attacks. Both types of exploits highlight the critical need for continuous vulnerability management and advanced threat detection systems.
Security Best Practices Against Both Exploit Types
Security best practices against zero-day and known exploits include implementing robust patch management systems to quickly address known vulnerabilities and deploying advanced threat detection tools such as behavior-based analytics and endpoint detection and response (EDR) to identify and mitigate zero-day threats. Employing network segmentation, continuous monitoring, and multi-factor authentication significantly reduces the attack surface and limits lateral movement in case of exploitation. Regular employee training on phishing and social engineering attacks further strengthens security posture against exploitation attempts targeting both zero-day and known vulnerabilities.
Future Trends in Defending Against Zero-Day and Known Exploits
Emerging security frameworks emphasize advanced machine learning models to detect anomalous behaviors indicative of zero-day exploits, enhancing proactive threat identification. Integration of threat intelligence platforms accelerates response times against known vulnerabilities by automating patch management and vulnerability assessments. Future defense strategies increasingly prioritize adaptive cybersecurity architectures combining real-time analytics and automated incident remediation to address both zero-day and known exploit threats effectively.
Zero-Day vs Known Exploit Infographic
 difterm.com
difterm.com