File Integrity Monitoring (FIM) tracks changes in critical system files to detect unauthorized modifications, ensuring data remains unaltered and secure. Log Monitoring continuously analyzes system and application logs to identify suspicious activities and potential security breaches through real-time event correlation. Combining FIM and Log Monitoring enhances overall security posture by providing comprehensive visibility into both file changes and system behavior.
Table of Comparison
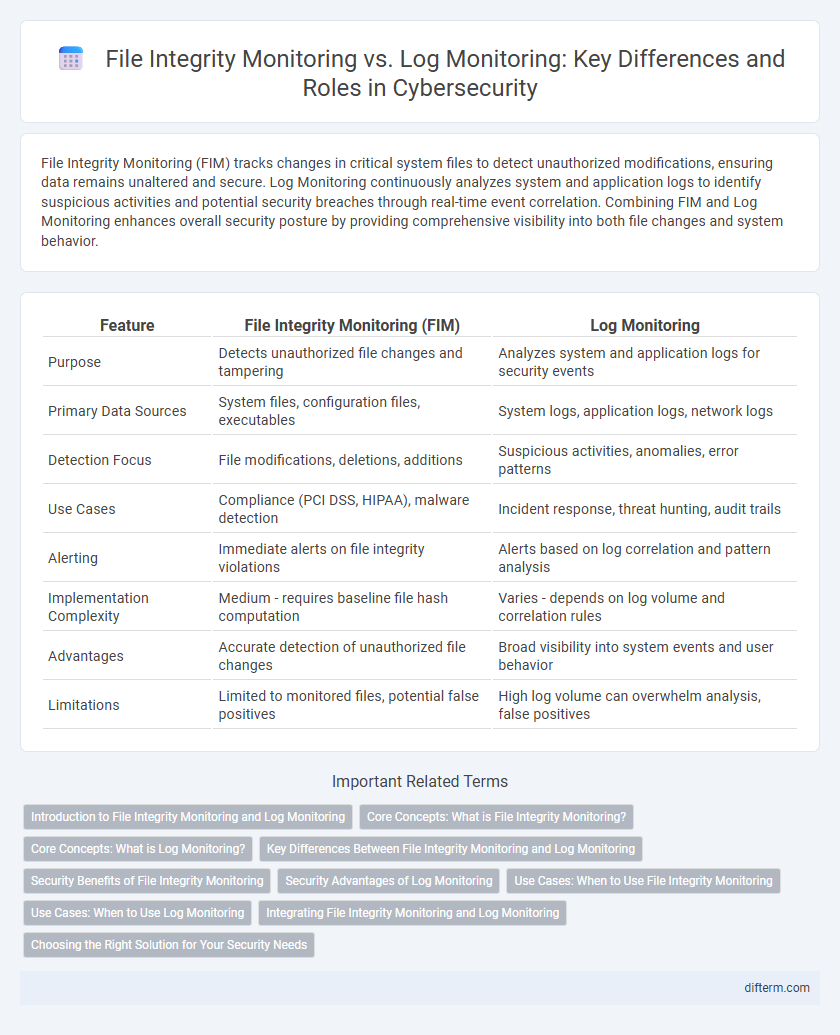
| Feature | File Integrity Monitoring (FIM) | Log Monitoring |
|---|---|---|
| Purpose | Detects unauthorized file changes and tampering | Analyzes system and application logs for security events |
| Primary Data Sources | System files, configuration files, executables | System logs, application logs, network logs |
| Detection Focus | File modifications, deletions, additions | Suspicious activities, anomalies, error patterns |
| Use Cases | Compliance (PCI DSS, HIPAA), malware detection | Incident response, threat hunting, audit trails |
| Alerting | Immediate alerts on file integrity violations | Alerts based on log correlation and pattern analysis |
| Implementation Complexity | Medium - requires baseline file hash computation | Varies - depends on log volume and correlation rules |
| Advantages | Accurate detection of unauthorized file changes | Broad visibility into system events and user behavior |
| Limitations | Limited to monitored files, potential false positives | High log volume can overwhelm analysis, false positives |
Introduction to File Integrity Monitoring and Log Monitoring
File Integrity Monitoring (FIM) continuously tracks changes to critical system files and configurations, ensuring unauthorized modifications are detected in real time to prevent security breaches. Log Monitoring systematically collects and analyzes event logs from various systems and applications, providing comprehensive visibility into suspicious activities and potential threats. Both tools are essential components of a robust security framework, enhancing breach detection and compliance adherence.
Core Concepts: What is File Integrity Monitoring?
File Integrity Monitoring (FIM) continuously tracks changes to critical system files, configurations, and directories to detect unauthorized modifications that could indicate security breaches. It compares current file states against known baselines using cryptographic checksums, alerting security teams to potential tampering or policy violations. FIM is essential for maintaining data integrity, regulatory compliance, and early threat detection in cybersecurity frameworks.
Core Concepts: What is Log Monitoring?
Log monitoring involves the continuous analysis of log files generated by operating systems, applications, and security devices to detect unauthorized activities or anomalies that indicate security threats. It collects and reviews event data in real time, enabling early identification of potential breaches, system errors, or policy violations through pattern recognition and alerting mechanisms. Effective log monitoring supports compliance requirements such as PCI DSS, HIPAA, and GDPR by maintaining detailed audit trails essential for forensic investigations and incident response.
Key Differences Between File Integrity Monitoring and Log Monitoring
File Integrity Monitoring (FIM) focuses on detecting unauthorized changes to critical system files by creating baselines and alerting on discrepancies, whereas Log Monitoring analyzes system and application logs to identify suspicious activities or anomalies. FIM provides real-time alerts on file tampering, ensuring the integrity of files, while Log Monitoring offers broader visibility into security events through continuous log analysis. Key differences include FIM's emphasis on file state verification versus Log Monitoring's focus on event correlation and behavioral insights.
Security Benefits of File Integrity Monitoring
File Integrity Monitoring (FIM) enhances security by ensuring real-time detection of unauthorized changes to critical system files, configuration files, and executables, which helps prevent breaches and data tampering. Unlike log monitoring, which provides insight into user activities and system events, FIM directly monitors file modifications, enabling faster response to malicious alterations and compliance with regulatory standards such as PCI DSS and HIPAA. This proactive approach strengthens overall cybersecurity posture by maintaining data integrity and supporting forensic investigations.
Security Advantages of Log Monitoring
Log Monitoring provides real-time visibility into system activities, enabling rapid detection of anomalous behavior and potential security breaches. It enhances threat intelligence by correlating events across multiple sources, facilitating early identification of cyberattacks and insider threats. Continuous log analysis supports compliance requirements and forensic investigations by maintaining a comprehensive audit trail of user actions and system changes.
Use Cases: When to Use File Integrity Monitoring
File Integrity Monitoring (FIM) is essential for detecting unauthorized changes to critical system files, configuration files, and application binaries, making it ideal for preventing data breaches and insider threats. FIM is best used in environments with strict compliance requirements such as PCI DSS, HIPAA, and SOX, where maintaining a detailed audit trail of file modifications is mandatory. Organizations should deploy FIM to ensure the integrity of sensitive files in real-time, enabling rapid response to ransomware attacks and zero-day exploits.
Use Cases: When to Use Log Monitoring
Log monitoring is essential for real-time threat detection and incident response by continuously analyzing system and application logs for suspicious activities or anomalies. It is particularly useful in environments requiring compliance with regulations like PCI DSS or HIPAA, where detailed audit trails and event correlations are necessary. Organizations leverage log monitoring to detect unauthorized access, configuration changes, and potential insider threats across diverse IT infrastructures.
Integrating File Integrity Monitoring and Log Monitoring
Integrating File Integrity Monitoring (FIM) and Log Monitoring enhances security by providing comprehensive visibility into system changes and user activities. FIM detects unauthorized modifications to critical files, while Log Monitoring analyzes event logs to identify suspicious patterns and potential breaches. Combining these tools enables real-time threat detection, improved incident response, and stronger compliance with regulatory requirements such as PCI DSS and HIPAA.
Choosing the Right Solution for Your Security Needs
File Integrity Monitoring (FIM) detects unauthorized changes to critical files, providing real-time alerts on potential security breaches, while Log Monitoring analyzes system and application logs to identify suspicious activities and patterns. Selecting the right solution depends on your organization's risk profile, regulatory requirements, and existing security infrastructure, with FIM offering precise change detection and Log Monitoring delivering comprehensive event visibility. Integrating both can enhance overall security posture by combining file-level integrity assurance with detailed event analysis.
File Integrity Monitoring vs Log Monitoring Infographic
 difterm.com
difterm.com