Security posture refers to the overall defense strength and readiness of an organization's IT environment against cyber threats, encompassing the technologies, processes, and controls in place. Security policy defines the formal rules and guidelines established by an organization to manage and protect information assets, shaping how security is implemented and maintained. Understanding the distinction improves risk management by aligning technical defenses with strategic governance.
Table of Comparison
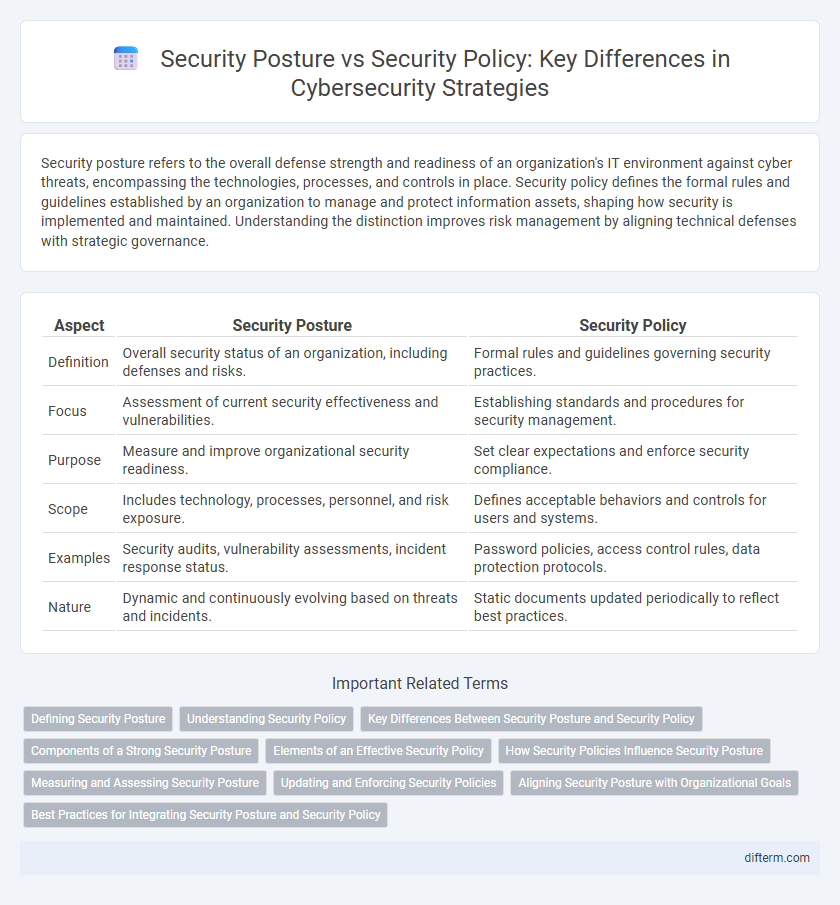
| Aspect | Security Posture | Security Policy |
|---|---|---|
| Definition | Overall security status of an organization, including defenses and risks. | Formal rules and guidelines governing security practices. |
| Focus | Assessment of current security effectiveness and vulnerabilities. | Establishing standards and procedures for security management. |
| Purpose | Measure and improve organizational security readiness. | Set clear expectations and enforce security compliance. |
| Scope | Includes technology, processes, personnel, and risk exposure. | Defines acceptable behaviors and controls for users and systems. |
| Examples | Security audits, vulnerability assessments, incident response status. | Password policies, access control rules, data protection protocols. |
| Nature | Dynamic and continuously evolving based on threats and incidents. | Static documents updated periodically to reflect best practices. |
Defining Security Posture
Security posture refers to the overall cybersecurity strength and readiness of an organization, encompassing the effectiveness of policies, controls, and practices in place to defend against threats. It includes the assessment of vulnerabilities, risk management strategies, and the organization's ability to detect, respond to, and recover from cyber incidents. Understanding security posture is critical for measuring the current security state beyond the documentation found in a security policy.
Understanding Security Policy
Security policy is a comprehensive set of rules and guidelines developed to protect an organization's information assets and govern user behavior. It defines security objectives, roles, responsibilities, and acceptable use to reduce risks and ensure regulatory compliance. Effective security policies serve as the foundation for establishing a strong security posture by guiding consistent implementation and incident response strategies.
Key Differences Between Security Posture and Security Policy
Security posture refers to an organization's overall cybersecurity strength, encompassing the tools, processes, and practices deployed to protect data and networks. In contrast, security policy defines the formal rules and guidelines governing how security measures should be implemented and maintained. Key differences include security posture being an assessment of current defenses and risk levels, while security policy acts as the documented framework that directs security behavior and compliance.
Components of a Strong Security Posture
A strong security posture integrates multiple components including risk management, continuous monitoring, robust incident response, and comprehensive employee training to identify and mitigate vulnerabilities effectively. It requires regular assessment and updating of security policies, ensuring alignment with evolving threats, compliance standards, and organizational goals. Endpoint protection, network security, access control, and encryption technologies are critical elements that collectively reinforce the organization's overall defense strategy.
Elements of an Effective Security Policy
Elements of an effective security policy include clear definitions of roles and responsibilities, comprehensive guidelines for risk management, and detailed procedures for incident response. It must align with organizational objectives while ensuring compliance with relevant regulations and standards such as ISO 27001 or NIST frameworks. Regular reviews and employee training are critical to maintain policy relevance and promote a strong security posture.
How Security Policies Influence Security Posture
Security policies establish the foundational rules and guidelines that govern an organization's approach to cybersecurity, directly shaping its security posture by defining how risks are managed and mitigated. A well-crafted security policy ensures consistent implementation of protections, compliance with regulations, and roles for incident response, thereby strengthening the overall security posture. Tight alignment between security policies and operational security practices results in a resilient security posture capable of adapting to emerging threats.
Measuring and Assessing Security Posture
Measuring and assessing security posture involves evaluating an organization's overall cybersecurity effectiveness through continuous monitoring, risk assessments, and vulnerability scans. Unlike security policy, which defines the rules and guidelines for protecting assets, security posture provides a real-time, data-driven snapshot of an organization's defensive capabilities against threats. Key metrics for security posture assessment include incident response times, patch management efficiency, and compliance adherence, enabling proactive risk mitigation and informed decision-making.
Updating and Enforcing Security Policies
Updating security policies regularly is crucial to maintaining a robust security posture, as it ensures policies address evolving threats and compliance requirements. Enforcing security policies effectively requires integration with automated monitoring tools and employee training programs to minimize human error and detect violations promptly. A dynamic approach to policy management strengthens organizational resilience against cyber risks and supports clear accountability frameworks.
Aligning Security Posture with Organizational Goals
Aligning security posture with organizational goals ensures that security measures effectively support business objectives by identifying and mitigating risks that could impact critical assets. A well-defined security posture provides a dynamic framework reflecting the organization's current threat landscape and operational priorities, while security policies establish specific rules and guidelines to enforce this posture. Integrating these elements enhances risk management, drives compliance, and fosters a proactive security culture aligned with strategic aims.
Best Practices for Integrating Security Posture and Security Policy
Integrating security posture and security policy requires continuous risk assessment to align policies with current threat landscapes and organizational objectives. Organizations should implement automated monitoring tools to ensure real-time visibility into security posture, enabling timely updates to policies based on evolving vulnerabilities. Establishing clear communication channels between IT and security teams enhances policy enforcement and fosters a proactive security culture.
Security Posture vs Security Policy Infographic
 difterm.com
difterm.com