Logic bombs and time bombs are malicious software triggered by specific conditions; a logic bomb activates when particular actions or behaviors occur, while a time bomb detonates at a predetermined date or time. Both types pose significant security threats by causing damage or unauthorized access when triggered, making detection and prevention crucial for protecting systems. Understanding their differences aids in developing targeted cybersecurity strategies to mitigate these risks effectively.
Table of Comparison
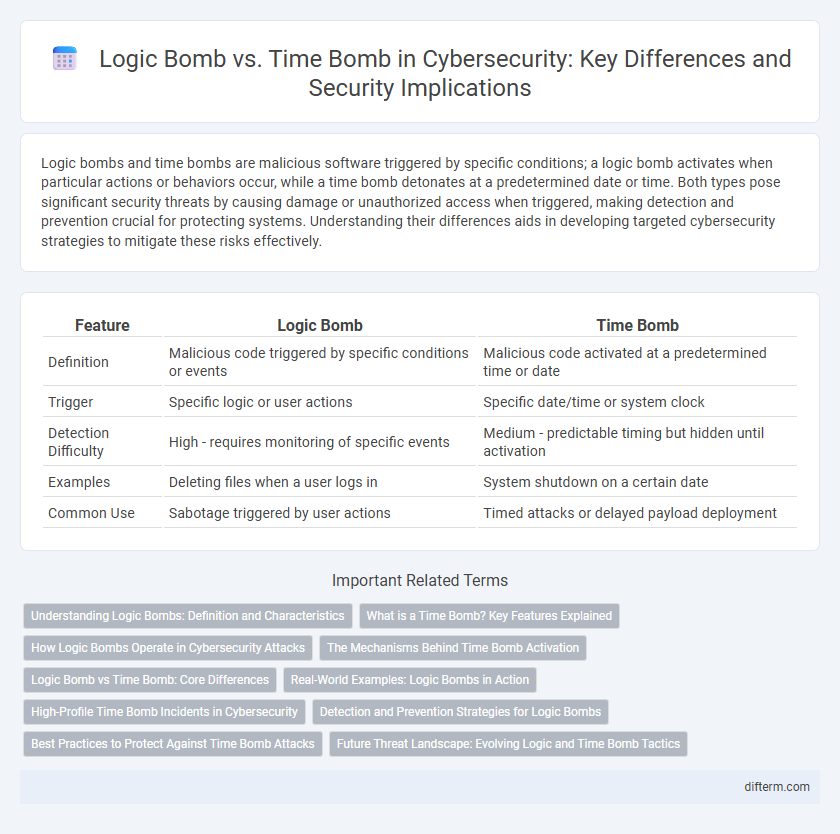
| Feature | Logic Bomb | Time Bomb |
|---|---|---|
| Definition | Malicious code triggered by specific conditions or events | Malicious code activated at a predetermined time or date |
| Trigger | Specific logic or user actions | Specific date/time or system clock |
| Detection Difficulty | High - requires monitoring of specific events | Medium - predictable timing but hidden until activation |
| Examples | Deleting files when a user logs in | System shutdown on a certain date |
| Common Use | Sabotage triggered by user actions | Timed attacks or delayed payload deployment |
Understanding Logic Bombs: Definition and Characteristics
Logic bombs are malicious code segments deliberately embedded within software to trigger harmful actions when specific conditions are met, such as a particular date, user action, or system event. Unlike viruses or worms, logic bombs remain dormant until activated, making them difficult to detect during regular security scans. Their characteristics include conditional triggers, stealthy nature, and potential to cause data corruption, system crashes, or unauthorized access depending on the programmed payload.
What is a Time Bomb? Key Features Explained
A time bomb is a type of malicious software programmed to activate at a specific date or time, causing unauthorized actions or damage when triggered. Key features include delayed execution, stealthiness, and precise activation schedules, which make detection and prevention challenging for security systems. Unlike logic bombs that rely on specific conditions, time bombs operate purely based on a predefined timeline, posing significant risks in cybersecurity environments.
How Logic Bombs Operate in Cybersecurity Attacks
Logic bombs operate by embedding malicious code within legitimate software, activating only when specific conditions or triggers are met, such as a date, user action, or system event. Unlike time bombs that execute based solely on a predetermined time, logic bombs remain dormant until their precise logical criteria are satisfied, making them difficult to detect through regular security scans. This conditional activation allows attackers to cause targeted damage, data corruption, or unauthorized access while evading immediate detection in cybersecurity environments.
The Mechanisms Behind Time Bomb Activation
Time bombs in cybersecurity activate based on a predetermined temporal trigger, such as a specific date, time, or system uptime threshold. This mechanism relies on embedded code that continuously checks the system clock or internal timers to initiate malicious actions once the set temporal condition is met. Unlike logic bombs that depend on specific user actions or system events, time bombs execute payloads strictly through time-based triggers, making detection challenging until the activation moment arrives.
Logic Bomb vs Time Bomb: Core Differences
Logic bombs and time bombs are both types of malicious code designed to trigger harmful actions, but logic bombs activate based on specific conditions or events within a system, while time bombs are programmed to trigger at a predetermined time or date. Logic bombs rely on system states or user actions, such as file access or system login, to execute their payload, whereas time bombs remain dormant until the internal clock matches the specified trigger. Understanding these core differences is crucial for implementing targeted detection and prevention strategies in cybersecurity.
Real-World Examples: Logic Bombs in Action
Logic bombs have been used in numerous high-profile cyberattacks, including the 2008 incident where a disgruntled employee inserted malicious code into a financial company's system, triggering data deletion upon specific conditions. The 2019 attack on a major software vendor involved a logic bomb embedded in updates, which activated to disrupt client operations after a set period. These real-world examples demonstrate the stealthy nature of logic bombs and their potential to cause significant damage when activated under defined circumstances.
High-Profile Time Bomb Incidents in Cybersecurity
High-profile time bomb incidents in cybersecurity have targeted major corporations and government agencies, causing widespread disruption by activating malicious code at predetermined times. Notable cases include the 2008 attack on a leading financial institution, where the time bomb triggered data corruption during peak transaction hours, and the 2013 breach of an energy sector company that resulted in prolonged system outages. These incidents highlight the critical need for advanced detection techniques and timely response strategies to mitigate the risks posed by time bombs in critical infrastructure.
Detection and Prevention Strategies for Logic Bombs
Logic bombs are malicious code triggered by specific conditions, making detection challenging without behavioral analysis tools that monitor abnormal system activity patterns. Prevention strategies include implementing strict access controls, regular code reviews, and deploying endpoint security solutions with heuristic scanning capabilities to identify suspicious scripts before execution. Organizations should also enforce continuous monitoring and anomaly detection frameworks to promptly identify and mitigate logic bomb activation attempts.
Best Practices to Protect Against Time Bomb Attacks
Implement strict access controls and continuous monitoring to detect unusual system activities that may indicate a time bomb activation. Regularly update and patch software to eliminate vulnerabilities that attackers could exploit for embedding malicious timers. Employ comprehensive data backup and incident response plans to minimize damage and ensure rapid recovery from time bomb attacks.
Future Threat Landscape: Evolving Logic and Time Bomb Tactics
Logic bombs and time bombs are increasingly sophisticated threats in the evolving cybersecurity landscape, targeting systems through stealthy execution triggered by specific conditions or timeframes. Future threat tactics involve more adaptive logic bombs that exploit artificial intelligence to detect system changes before activating, while time bombs leverage precise time synchronization across global networks to launch coordinated attacks. Anticipating these threats requires advanced behavioral analytics and predictive security models to identify subtle indicators of pre-activation phases.
Logic bomb vs Time bomb Infographic
 difterm.com
difterm.com