A botnet is a network of compromised computers controlled by a hacker to launch coordinated cyber attacks, while zombies are the individual infected machines within that network. Zombies operate silently under the command of the botnet controller, executing tasks such as sending spam, stealing data, or participating in distributed denial-of-service (DDoS) attacks. Protecting systems with updated antivirus software and monitoring unusual network activity can help detect and prevent botnet infections.
Table of Comparison
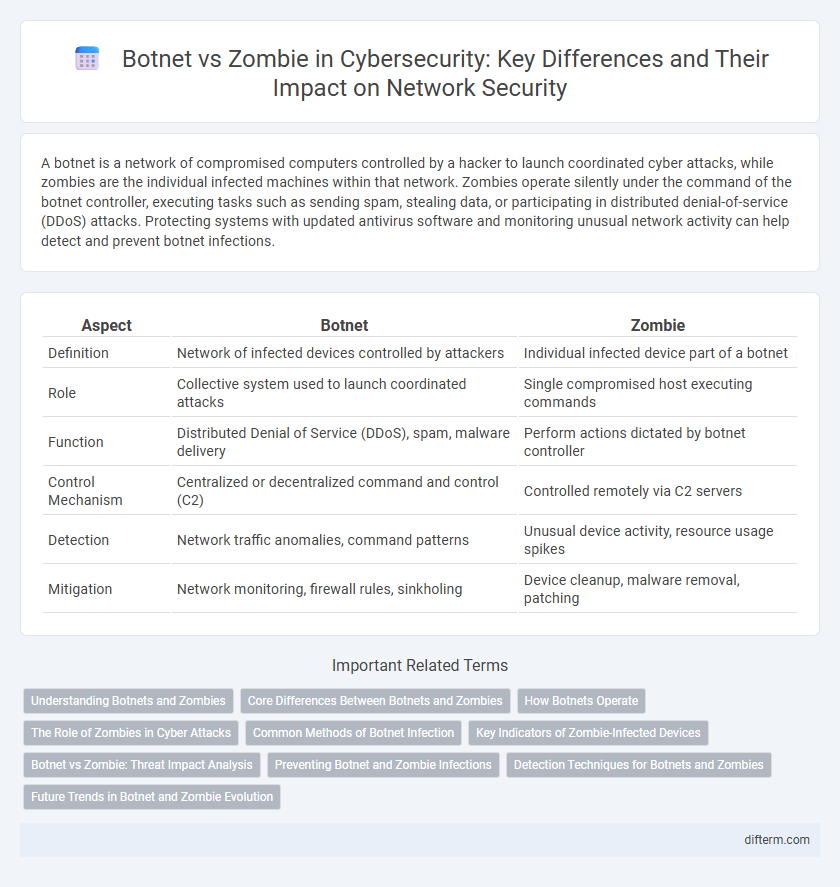
| Aspect | Botnet | Zombie |
|---|---|---|
| Definition | Network of infected devices controlled by attackers | Individual infected device part of a botnet |
| Role | Collective system used to launch coordinated attacks | Single compromised host executing commands |
| Function | Distributed Denial of Service (DDoS), spam, malware delivery | Perform actions dictated by botnet controller |
| Control Mechanism | Centralized or decentralized command and control (C2) | Controlled remotely via C2 servers |
| Detection | Network traffic anomalies, command patterns | Unusual device activity, resource usage spikes |
| Mitigation | Network monitoring, firewall rules, sinkholing | Device cleanup, malware removal, patching |
Understanding Botnets and Zombies
Botnets consist of a network of compromised computers, known as zombies, controlled remotely by cybercriminals to perform coordinated malicious activities like DDoS attacks and data theft. Zombies are individual infected devices within the botnet that operate under the malware author's commands without the user's knowledge. Understanding the distinction between botnets as orchestrated systems and zombies as their components is crucial for effective network defense and cybersecurity measures.
Core Differences Between Botnets and Zombies
Botnets consist of a network of compromised computers controlled by a single entity to perform coordinated cyberattacks, while zombies refer specifically to individual infected machines within that network. Botnets leverage the collective power of multiple zombies to execute large-scale operations such as Distributed Denial of Service (DDoS) attacks or mass spam campaigns. The core difference lies in scale and control: botnets operate as organized systems under centralized control, whereas zombies are singular infected hosts acting as components of the botnet infrastructure.
How Botnets Operate
Botnets operate through a network of compromised computers, known as zombies, which are remotely controlled by cybercriminals to execute coordinated attacks such as DDoS, spam distribution, or data theft. Each zombie device is infected with malware that connects back to a command-and-control (C&C) server, allowing attackers to issue commands and manage the botnet efficiently. The decentralized structure and stealthy communication protocols enable botnets to evade detection, making mitigation and takedown complex for cybersecurity professionals.
The Role of Zombies in Cyber Attacks
Zombies in cyber attacks refer to compromised computers controlled remotely by hackers to perform malicious activities as part of a botnet. These infected machines enable large-scale distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft without the knowledge of the device owner. The network of zombies amplifies the attack power by coordinating simultaneous actions, making mitigation and attribution challenging for security professionals.
Common Methods of Botnet Infection
Botnet infection commonly occurs through phishing emails, malicious downloads, and exploiting software vulnerabilities, leading to the infiltration of numerous zombie devices. These compromised zombies become part of a botnet, allowing cybercriminals to execute coordinated attacks like DDoS or spam distribution. Understanding these infection methods is crucial for developing effective cybersecurity defenses and mitigating botnet threats.
Key Indicators of Zombie-Infected Devices
Zombie-infected devices typically exhibit unusual network behavior such as unexplained outbound traffic spikes, consistent communication with suspicious command-and-control (C&C) servers, and degraded system performance due to unauthorized resource consumption. Key indicators include frequent, automated network connections at odd hours, increased CPU usage without user activity, and unexplained changes in system files or configurations. Monitoring these signs within botnet detection frameworks enables early identification and mitigation of compromised "zombie" devices.
Botnet vs Zombie: Threat Impact Analysis
Botnets consist of networks of compromised devices controlled remotely by cybercriminals, enabling large-scale attacks such as DDoS, spam campaigns, and data theft. Zombies refer to individual infected computers within a botnet, acting as pawns that execute malicious commands without user consent. The threat impact of botnets is significantly higher than individual zombies due to their collective ability to amplify attack scale, persistence, and stealth, making botnet takedowns critical in cybersecurity defense strategies.
Preventing Botnet and Zombie Infections
Effective prevention of botnet and zombie infections relies on robust cybersecurity measures such as deploying advanced firewalls, regularly updating antivirus software, and conducting comprehensive network monitoring to detect suspicious activities early. Implementing strict access controls, educating users about phishing attacks, and applying timely security patches across all devices significantly reduce the risk of malware infiltration that converts systems into zombies for botnet operations. Continuous threat intelligence analysis and proactive incident response strategies are essential for minimizing botnet propagation and maintaining overall network integrity.
Detection Techniques for Botnets and Zombies
Effective detection techniques for botnets and zombies rely on analyzing network traffic patterns and identifying abnormal communication behaviors such as command and control (C&C) signaling. Machine learning algorithms enhance detection accuracy by classifying suspicious activities based on features like IP reputation, traffic volume anomalies, and protocol deviations. Behavioral analysis tools and honeypots further expose botnet operations by simulating vulnerable endpoints to capture and study malware-infected zombie hosts.
Future Trends in Botnet and Zombie Evolution
Emerging trends indicate botnets and zombies will increasingly leverage artificial intelligence and machine learning to enhance their stealth and adaptive capabilities, complicating detection and mitigation efforts. The integration of Internet of Things (IoT) devices into botnet networks is expected to expand, significantly increasing the scale and impact of distributed denial-of-service (DDoS) attacks. Advances in decentralized botnet architectures, such as peer-to-peer (P2P) models, will facilitate more resilient and evasive zombie networks, challenging future cybersecurity defenses.
Botnet vs Zombie Infographic
 difterm.com
difterm.com