Exploit kits are malicious software toolkits designed to identify and leverage vulnerabilities in applications or systems to deliver payloads such as malware or ransomware. Rootkits, on the other hand, operate by gaining unauthorized root or administrative access to a target system, remaining hidden while enabling persistent control and evasion of detection. Understanding the distinct mechanisms and objectives of exploit kits and rootkits is crucial for developing effective cybersecurity defenses and incident response strategies.
Table of Comparison
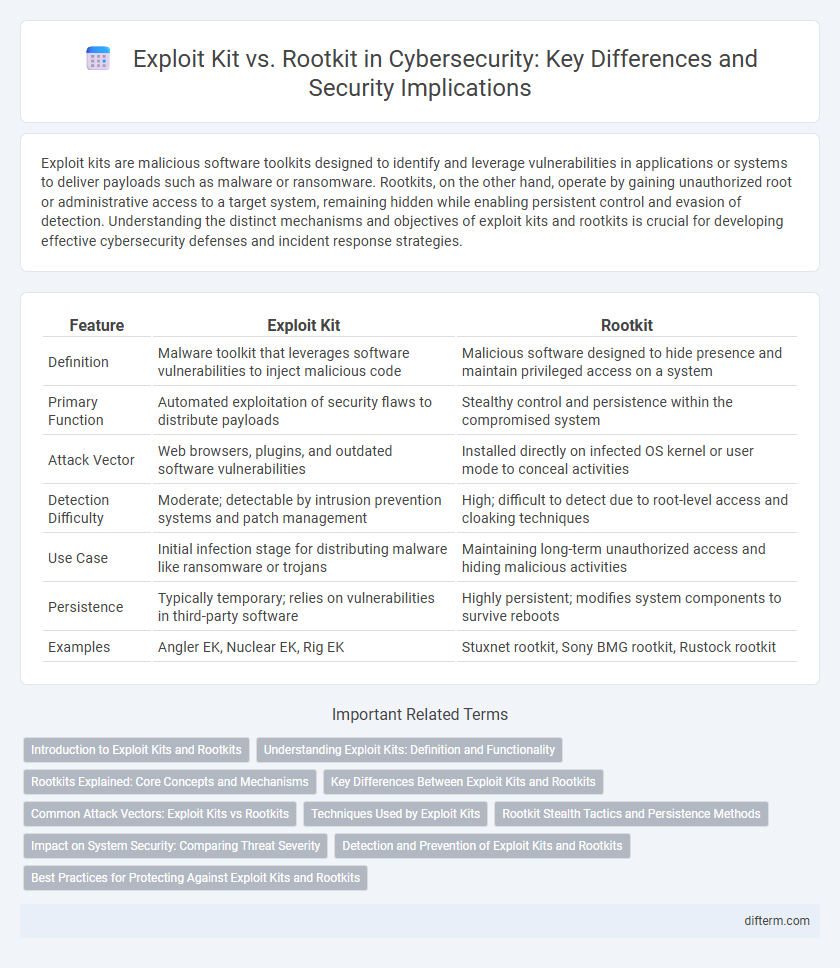
| Feature | Exploit Kit | Rootkit |
|---|---|---|
| Definition | Malware toolkit that leverages software vulnerabilities to inject malicious code | Malicious software designed to hide presence and maintain privileged access on a system |
| Primary Function | Automated exploitation of security flaws to distribute payloads | Stealthy control and persistence within the compromised system |
| Attack Vector | Web browsers, plugins, and outdated software vulnerabilities | Installed directly on infected OS kernel or user mode to conceal activities |
| Detection Difficulty | Moderate; detectable by intrusion prevention systems and patch management | High; difficult to detect due to root-level access and cloaking techniques |
| Use Case | Initial infection stage for distributing malware like ransomware or trojans | Maintaining long-term unauthorized access and hiding malicious activities |
| Persistence | Typically temporary; relies on vulnerabilities in third-party software | Highly persistent; modifies system components to survive reboots |
| Examples | Angler EK, Nuclear EK, Rig EK | Stuxnet rootkit, Sony BMG rootkit, Rustock rootkit |
Introduction to Exploit Kits and Rootkits
Exploit kits are automated tools used by cybercriminals to identify and target vulnerabilities in software, enabling the delivery of malware without user interaction. Rootkits, in contrast, are stealthy malware designed to gain and maintain privileged access to a system while hiding their presence from security software. Understanding the roles of exploit kits in initial infection and rootkits in persistent control is crucial for effective cybersecurity defenses.
Understanding Exploit Kits: Definition and Functionality
Exploit kits are automated tools designed to identify and leverage vulnerabilities in software applications, enabling the execution of malicious code on a target system. They typically operate by scanning for security flaws in browsers, plugins, or operating systems and delivering payloads like ransomware or spyware without user consent. Understanding exploit kits is crucial for developing effective defenses against automated cyberattacks and minimizing unauthorized access risks.
Rootkits Explained: Core Concepts and Mechanisms
Rootkits are stealthy malware designed to gain unauthorized root or administrative access while concealing their presence within a system by manipulating core operating system functions and kernel modules. They operate at a low level, often hooking into system calls, modifying kernel data structures, and intercepting system processes to hide files, processes, or network activity from detection tools. Unlike exploit kits, which are frameworks for delivering exploits, rootkits focus on long-term persistence and invisibility, making them particularly dangerous for maintaining control over compromised systems.
Key Differences Between Exploit Kits and Rootkits
Exploit kits are automated tools designed to identify and exploit vulnerabilities in software to deliver malware, often used in drive-by download attacks, whereas rootkits are stealthy malicious programs that gain unauthorized root or administrative access to a system, maintaining persistent control while hiding their presence. Exploit kits primarily target vulnerabilities to initiate infection, while rootkits focus on maintaining long-term, covert access and evading detection by security mechanisms. Understanding these key differences is critical for cybersecurity defenses, as exploit kits necessitate patch management and vulnerability scanning, whereas rootkits require advanced detection techniques such as behavioral analysis and integrity checking.
Common Attack Vectors: Exploit Kits vs Rootkits
Exploit kits typically target vulnerabilities in web browsers, plugins, and software to deliver malware through drive-by downloads or malicious ads, leveraging social engineering and compromised websites as common attack vectors. Rootkits often infiltrate systems via trojans, phishing emails, or software exploits to gain stealthy, persistent access and hide malicious activities at the kernel or firmware level. Both exploit kits and rootkits exploit initial system weaknesses but differ in delivery methods and persistence techniques within compromised environments.
Techniques Used by Exploit Kits
Exploit kits leverage automated scanning, vulnerability detection, and payload delivery techniques to infiltrate systems by exploiting software flaws. These kits often use drive-by downloads, social engineering, and obfuscation to evade detection and compromise target devices rapidly. In contrast, rootkits primarily focus on stealth and persistence by modifying system files and kernel processes to maintain unauthorized access.
Rootkit Stealth Tactics and Persistence Methods
Rootkits employ advanced stealth tactics such as kernel-level hooks and direct manipulation of system APIs to remain undetected by traditional security tools, enabling persistent control over the compromised system. They use methods like hiding files, processes, and registry entries, alongside employing techniques such as code injection and root-level access to maintain long-term persistence. Unlike exploit kits that leverage vulnerabilities for initial infection, rootkits focus on concealment and continuous presence within the system, making detection and removal significantly more challenging.
Impact on System Security: Comparing Threat Severity
Exploit kits actively target system vulnerabilities to deliver malware, often resulting in rapid compromise and data breaches, thus posing an immediate and widespread security threat. Rootkits operate stealthily to maintain persistent unauthorized access, allowing attackers to manipulate system processes and evade detection, which leads to long-term control and difficult forensic analysis. The severity of impact depends on the attack vector: exploit kits enable initial infiltration, while rootkits ensure sustained exploitation, both critically undermining system security.
Detection and Prevention of Exploit Kits and Rootkits
Exploit kits frequently use browser vulnerabilities to deliver malware and are detected through web traffic analysis, intrusion detection systems, and behavior-based antivirus solutions, while rootkits embed deeply into the operating system, requiring advanced rootkit detection tools and kernel integrity checkers for identification. Prevention of exploit kits relies heavily on patch management, updated antivirus signatures, and web filtering technologies, whereas rootkit prevention focuses on secure boot processes, limiting administrative access, and employing hardware-based security measures like TPM. Regular system scanning with specialized anti-rootkit utilities and continuous monitoring of system behavior enhance early detection and reduce the risk posed by both exploit kits and rootkits.
Best Practices for Protecting Against Exploit Kits and Rootkits
Implementing multi-layered security measures, including regular software patching and system updates, effectively reduces vulnerabilities exploited by exploit kits and rootkits. Employing advanced endpoint detection and response (EDR) tools with behavioral analysis enhances identification and removal of rootkits embedded deep within operating systems. Regularly backing up data and using application whitelisting restrict unauthorized code execution, minimizing the risk posed by both exploit kits and stealthy rootkits.
Exploit Kit vs Rootkit Infographic
 difterm.com
difterm.com