Viruses require user interaction to spread by attaching themselves to executable files or documents, causing damage or unauthorized actions on infected systems. Worms replicate independently through networks, exploiting vulnerabilities to propagate rapidly without user intervention, often leading to widespread disruptions. Effective security measures include updated antivirus software, network monitoring, and timely patching to prevent the spread of both viruses and worms.
Table of Comparison
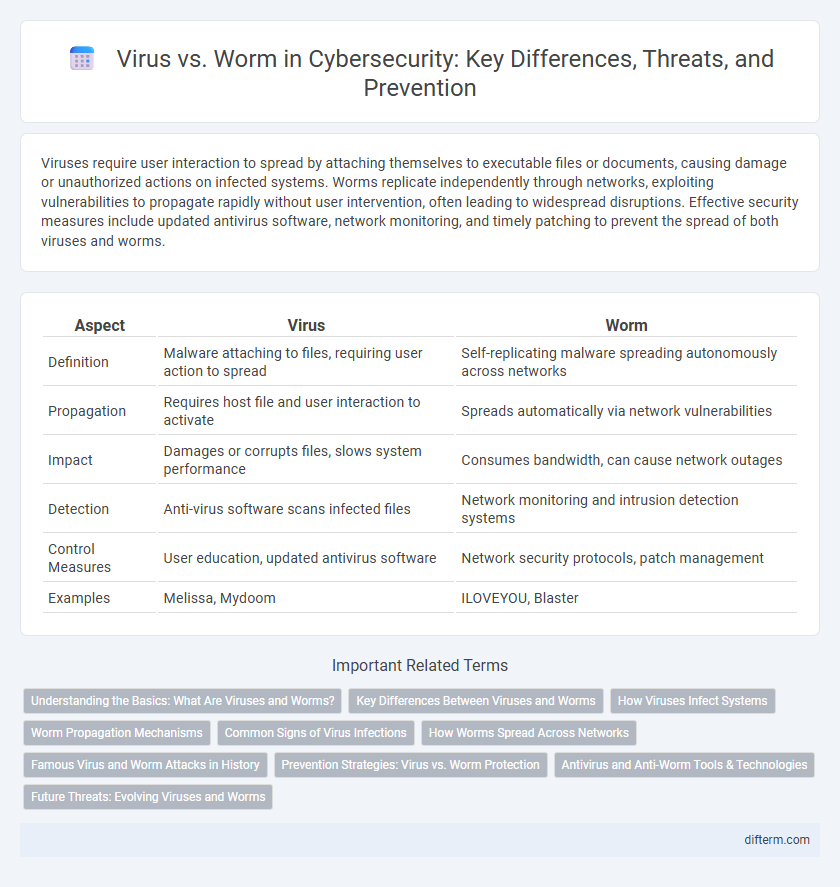
| Aspect | Virus | Worm |
|---|---|---|
| Definition | Malware attaching to files, requiring user action to spread | Self-replicating malware spreading autonomously across networks |
| Propagation | Requires host file and user interaction to activate | Spreads automatically via network vulnerabilities |
| Impact | Damages or corrupts files, slows system performance | Consumes bandwidth, can cause network outages |
| Detection | Anti-virus software scans infected files | Network monitoring and intrusion detection systems |
| Control Measures | User education, updated antivirus software | Network security protocols, patch management |
| Examples | Melissa, Mydoom | ILOVEYOU, Blaster |
Understanding the Basics: What Are Viruses and Worms?
Viruses are malicious programs that attach themselves to legitimate files or software, requiring user interaction to spread and cause damage by corrupting or deleting data. Worms, in contrast, are self-replicating malware that exploit network vulnerabilities to spread autonomously across connected systems, often overwhelming networks with traffic. Understanding their distinct propagation methods and impact is crucial for implementing effective cybersecurity defenses.
Key Differences Between Viruses and Worms
Viruses require a host file or program to spread, attaching themselves to executable files, whereas worms are standalone malicious software that propagate independently across networks. Viruses spread through user actions like opening infected files, while worms exploit network vulnerabilities to replicate rapidly without user intervention. The impact of worms typically includes network congestion and fast widespread infection, while viruses often lead to file corruption and targeted damage.
How Viruses Infect Systems
Viruses infect systems by attaching themselves to legitimate executable files or documents, activating when the host file is run, which allows them to replicate and spread to other files on the same device. They often require user action, such as opening an infected email attachment or running a compromised program, to initiate the infection process. Once active, viruses can corrupt data, steal sensitive information, and disrupt system operations by modifying or deleting crucial files.
Worm Propagation Mechanisms
Worms propagate through network vulnerabilities by exploiting software flaws to replicate and spread autonomously without user intervention. They often use methods like email attachments, file-sharing networks, and unsecured network ports to infiltrate systems rapidly. Unlike viruses, worms do not need to attach themselves to host files, enabling faster and more extensive distribution across computer networks.
Common Signs of Virus Infections
Common signs of virus infections include unexpected system slowdowns, frequent crashes, and corrupted or missing files. Users may notice unusual pop-ups, altered file names, or unauthorized changes to system settings. Persistent antivirus alerts and abnormal network activity often indicate the presence of a virus spreading through infected files or executables.
How Worms Spread Across Networks
Worms rapidly propagate across networks by exploiting vulnerabilities in operating systems and software, often using automated scanning to identify and infect unpatched machines. Unlike viruses, worms do not require user interaction to spread, allowing them to self-replicate and transmit through network shares, email attachments, or internet connections. Their ability to spread autonomously makes worms particularly aggressive in causing widespread network disruption and data compromise.
Famous Virus and Worm Attacks in History
The Melissa virus, unleashed in 1999, spread rapidly through email systems, causing widespread disruption by infecting Microsoft Word documents and email contacts. The ILOVEYOU worm, which struck in 2000, exploited email attachments to propagate globally, causing billions in damages and overwhelming networks. Both attacks highlighted vulnerabilities in email-based malware, prompting significant advancements in cybersecurity defenses.
Prevention Strategies: Virus vs. Worm Protection
Effective prevention strategies for viruses include regularly updating antivirus software, scanning files before opening, and avoiding downloads from untrusted sources. Worm protection requires robust firewall configurations, immediate patching of software vulnerabilities, and network monitoring to detect unusual traffic patterns. Employing comprehensive cybersecurity training also enhances user awareness and reduces the risk of both virus and worm infections.
Antivirus and Anti-Worm Tools & Technologies
Antivirus tools are designed to detect, quarantine, and eliminate viruses by scanning for known signatures and behavioral patterns within files and system memory. Anti-worm technologies focus on identifying and blocking worms by monitoring network traffic, detecting rapid self-replication, and preventing unauthorized propagation across connected devices. Both antivirus and anti-worm solutions leverage heuristic analysis, machine learning algorithms, and real-time updates to effectively mitigate threats and protect system integrity.
Future Threats: Evolving Viruses and Worms
Future threats in cybersecurity will increasingly involve evolving viruses and worms that leverage advanced machine learning algorithms to bypass traditional detection methods. These malicious programs are expected to exploit zero-day vulnerabilities and polymorphic techniques, making them more adaptable and harder to eradicate. Continuous development in AI-powered defense systems is crucial to counteract the sophisticated propagation and mutation strategies of next-generation viruses and worms.
Virus vs Worm Infographic
 difterm.com
difterm.com